Many companies increasingly rely on the cloud due to its numerous benefits. While migrating to the cloud network, more time needs to spend on security. Cloud-based services handle a significant amount of network data, but many organizations use these services without implementing any security strategies. Additionally, the use of cloud service providers and personal devices makes it challenging for companies to monitor and manage data flows.
The common cloud computing services such as IaaS ,PaaS and SaaS and organizations will select those models on the basis of their needs. Implementing a strong cloud security strategy is essential for protecting your assets, regardless of the service model you choose.
However, since each model operates differently, there is no universal approach to cloud security. It is important to consider the unique characteristics of each model when designing and implementing a security strategy.
In this article, you can gain knowledge on developing a cybersecurity plan that ensures the protection of cloud services in the Software-as-a-Service (SaaS), Platform-as-a-Service (PaaS), and Infrastructure-as-a-Service (IaaS) service delivery models.
Specifying security baselines for IaaS ,PaaS and SaaS services
The cybersecurity strategy will encompass the development of security baselines for SaaS, PaaS, and IaaS, and define security requirements for various components such as edge computing, containers, application services, databases, and storage accounts within Azure.
Learn More: Want to become a cybersecurity expert?, then take SC-100 Certification now!
Securing PaaS (Platform-as-a-Service), IaaS (Infrastructure-as-a-Service), and SaaS (Software-as-a-Service) services requires a comprehensive approach that addresses various security concerns. Here are some key steps to designing a strategy for securing these services:
- Patch Management: Keep the VM operating system and all applications running on it up-to-date with the latest security patches to reduce the risk of exploitation.
- Account Security: Create and manage accounts with strong passwords, configure accounts with the least necessary privileges, and enable multi-factor authentication to prevent unauthorized access.
- Network Security: Use network security groups (NSGs) to control inbound and outbound traffic to and from VMs. Use Azure Virtual Network and subnets to isolate VMs from the Internet and other networks.
- Disk Encryption: Encrypt VM disks using BitLocker or dm-crypt to protect against data theft.
- Monitoring and Logging: Set up monitoring and logging to detect and respond to security incidents in real-time.
- Backup and Disaster Recovery: Create backups of VMs and implement disaster recovery plans to ensure business continuity in case of data loss or system failure.
- Security Assessment: Conduct periodic security assessments to identify vulnerabilities and improve security posture.
- Data Protection: Use encryption to protect sensitive data both at rest and in transit. SaaS providers should implement strong authentication mechanisms and access controls to prevent unauthorized access to sensitive data.
- Identity and Access Management: Implement strong identity and access management controls, including multi-factor authentication, to prevent unauthorized access to SaaS applications.
- Configuration Management: Configure SaaS applications securely by following vendor best practices and established security benchmarks. SaaS providers should regularly review and update their configuration settings to ensure continued security.
- Network Security: Implement secure network architecture to ensure that all communications between SaaS applications and end-users are secured. SaaS providers should implement secure coding practices and conduct regular penetration testing to ensure the security of their applications.
- Incident Response: Establish a well-defined incident response plan that includes procedures for detecting, containing, and mitigating security incidents.
- Compliance and Audit: Implement appropriate security controls to comply with regulatory requirements and industry standards. SaaS providers should undergo regular audits to ensure compliance with security requirements and standards.
Specify security requirements for IoT workloads
To secure an Internet of Things (IoT) infrastructure, it is essential to implement a comprehensive security-in-depth approach. This involves implementing measures to secure data in the cloud, ensuring the integrity of data during transmission over public networks, and securely provisioning devices. By implementing security measures at each layer, you can increase the overall security of the infrastructure. And it can be achieved by following methods:
Device identity
Device identity for IoT refers to the unique identity that is assigned to each IoT device to ensure secure communication and prevent unauthorized access. A device identity is essentially a digital fingerprint that uniquely identifies an IoT device and enables secure communication between the device and other endpoints in the IoT ecosystem.
There are various methods for establishing device identity in IoT, such as:
- X.509 Certificates: X.509 certificates are digital certificates that use public key cryptography to verify the identity of devices in IoT. Each IoT device is assigned a unique X.509 certificate that includes its public key, which is used for secure communication.
- Pre-Shared Keys (PSK): Pre-shared keys are a simple method for device authentication in IoT. Each device is assigned a secret key that is shared between the device and the IoT gateway. The secret key is used to authenticate the device during communication.
- Unique Identifiers: IoT devices can be assigned unique identifiers such as serial numbers or MAC addresses. These unique identifiers can be used to authenticate the device during communication.
- Device-specific Secrets: Device-specific secrets are unique secrets that are assigned to each IoT device during manufacturing. These secrets can be used for device authentication and secure communication.
www.microsoft.com
Establishing device identity is a crucial aspect of IoT security, as it helps to prevent unauthorized access and ensures secure communication between IoT devices and other endpoints in the IoT ecosystem. By implementing robust device identity mechanisms, organizations can improve the security of their IoT deployments and protect against potential security threats.
Password-less authentication
Password-less authentication is a method of authentication that allows users to access their accounts without the need for a traditional password. Instead of relying on a password, password-less authentication uses alternative methods of authentication, such as biometric authentication, multi-factor authentication (MFA), or public key cryptography.
There are several benefits to password-less authentication. One of the main benefits is improved security, as traditional passwords can be vulnerable to attacks such as phishing, password cracking, and password reuse. Password-less authentication eliminates these vulnerabilities by using more secure authentication methods.
Another benefit of password-less authentication is improved user experience. Traditional passwords can be difficult to remember, leading to frustration for users. Password-less authentication simplifies the authentication process and can reduce the need for users to remember complex passwords.
There are several methods for implementing password-less authentication, including:
- Biometric authentication: Biometric authentication uses physical characteristics of the user, such as fingerprints, facial recognition, or iris scans, to authenticate the user.
- Multi-factor authentication (MFA): MFA requires the user to provide two or more methods of authentication, such as a fingerprint and a security token, to authenticate the user.
- Public key cryptography: Public key cryptography uses a public and private key pair to authenticate the user. The user’s private key is used to authenticate the user, while the public key is used to verify the user’s identity.
Monitoring
CISA recommends several key components for security monitoring in the context of IoT and OT devices:
- Asset inventory and network mapping: Generating an inventory of all IoT and OT devices, as well as a network map that shows how these devices are interconnected, is a crucial first step in security monitoring. This information is needed to identify potential attack paths and to track down specific devices that may be vulnerable or compromised.
- Protocol identification: Identifying all communication protocols used across IoT/OT networks is important for detecting suspicious activity and potential threats. Different protocols may have different security characteristics, and monitoring for unusual protocol usage can help identify malicious behavior.
- External connection cataloging: Cataloging all external connections to and from IoT/OT networks is important for detecting potential threats from outside the organization. This includes not only connections to the public internet, but also connections to third-party vendors, partners, or other networks.
- Vulnerability identification and mitigation: Identifying vulnerabilities in IoT/OT devices and using a risk-based approach to mitigate them is critical for maintaining the security of these devices. This involves regular vulnerability scanning, patching, and configuration management to ensure that devices are up-to-date and secure.
- Vigilant monitoring program: Implementing a vigilant monitoring program with anomaly detection is important for detecting and responding to potential threats. This program should monitor for unauthorized changes to controllers, unusual behavior from devices, and audit access and authorization attempts. It should also include threat intelligence feeds and incident response procedures to ensure that potential threats are identified and addressed in a timely manner.
By following these key components for security monitoring, organizations can help protect their IoT and OT devices from cyber threats and ensure the security of their critical infrastructure.
Specify security requirements for data workloads, including SQL, Azure SQL Database, Azure Synapse and Azure Cosmos DB
Benefits of Azure SQL on Azure VM
SQL Server on Azure Virtual Machines is the ideal solution if you simply want to move your databases to the cloud in their current state. This is not always the greatest option, however, as it occasionally needs to be used as an exemplar for compatibility concerns.
Azure SQL Managed Instance usage
It’s now possible to integrate Azure Active Directory authentication directly into your database, eliminating the need for manually created user accounts. This means that users who are created within your Azure environment can now seamlessly access the database with the added security and identity protection features of Azure Identity. With this integration, you can maintain a single identity for your users and simplify the authentication and authorization process.
In addition to the Azure Active Directory authentication, the deployment options for the database now include Elastic Pools. The two options available are a single database with its own set of resources managed via a logical SQL server, similar to a contained database in SQL Server. This option is ideal for modern application development of new cloud-based applications and offers both Hyperscale and serverless options.
Azure SQL Database features
The other option is an elastic pool, which is a collection of databases with a shared set of resources managed via a logical SQL server. An elastic pool is a fantastic option for developing contemporary applications using the multi-tenant SaaS application design since databases can be added to and removed from it with ease. Elastic pools provide a practical way to control the performance of numerous databases with various usage patterns.
Typically, the vital information in Azure Cosmos DB is collected and processed via Extract-Transform-Load (ETL) pipelines in order to evaluate huge operational datasets while reducing the effect on the efficiency of mission-critical transactional applications. The several layers of data transfer required by ETL pipelines add to operational complexity and have a negative influence on the performance of your transactional workloads. The analysis of operational information from the point of origin also takes longer.
Specify security requirements for web workloads, including Azure App Service
The Serverless computing key components include functions, logic apps and an event grid.
You can run code on-demand with Azure Functions, a serverless compute solution, without having to set up or maintain infrastructure. You may observe how Azure Functions responds to a range of events by executing a script or piece of code.
Since Azure functions are constructed using the same fundamental building blocks as Azure App Service, you can switch on some functionalities essentially “for free” without writing any more code.
Logic Apps
Azure App Service’s Logic Apps feature enables the creation of scalable integrations and workflows. It includes a visual designer for modeling and automating workflows using a series of steps. Additionally, Logic Apps offers a range of connectors for quickly connecting serverless apps to both cloud-based and on-premises services.
A Logic App is initiated by a trigger, such as the addition of an account to Dynamics CRM, and can include a combination of actions, conversions, and conditional logic. Logic Apps is particularly useful for orchestrating multiple functions within a process, especially when external systems or APIs need to be interacted with.
Event grid
You can create applications with occurrence architectures using Azure Event Grid. Therefore provide event handler or websocket endpoint to deliver the event to after selecting the Azure resource you wish to subscribe to.
To ensure the security of your apps in Azure App Service, there are several measures you should take. Firstly, it is important to secure your apps with HTTPS, using a TLS/SSL certificate to enable HTTPS connections to your custom domain. Additionally, you can disable insecure protocols and enforce HTTPS to prevent unsecured requests from reaching your app’s code.
Static IP restrictions can also be created to limit access to your app to a small subset of IP addresses. Azure App Service also provides authentication and authorization solutions, which can sign in users and client apps with minimal application code.
To protect your application secrets, avoid storing them in your code or configuration files. Instead, access them as environment variables using the standard pattern in your preferred language.
Lastly, network isolation can be implemented through the isolated tier, which runs your apps in a dedicated App Service environment. This environment provides complete network isolation and runs within your own instance of Azure Virtual Network.
Specify security requirements for storage workloads, including Azure Storage
Azure Storage Accounts are well-suited for workloads that demand rapid and consistent response times or require a high number of input/output (IOP) operations per second. They serve as a repository for all of your Azure Storage data objects, such as blobs, file shares, queues, tables, and disks.
To optimize security when setting up your Azure Storage Account, consider the following recommendations:
- Enable soft delete for blob data.
- Use Azure Active Directory (AD) to authorize access to blob data.
- Apply the principle of least privilege when assigning permissions to an Azure AD security principal through Azure Role-Based Access Control (RBAC).
- Use blob versioning or immutable blobs to store business-critical data.
- Limit default internet access for storage accounts.
- Configure firewall rules to restrict access to your storage account.
- Limit network access to specific networks.
- Allow trusted Microsoft services to access the storage account.
- Enable the “Secure transfer required” option for all your storage accounts.
- Limit shared access signature (SAS) tokens to HTTPS connections only.
- Avoid using Shared Key authorization to access storage accounts and prevent others from doing so.
- Regularly regenerate your account keys.
- Create a revocation plan and have it in place for any SAS issued to clients.
Specify security requirements for containers
A container is a pre-configured software environment that contains both the application code and its dependencies within an image.The ability to run several instances of an operating system simultaneously is made possible by machine virtualization, which acts at the hardware level. Unlike virtual machines, containers run as distinct processes while sharing the host operating system.
Configuration of security for container services
Authentication
| Method | Authentication steps | Scenarios | Azure RBAC | Limitations |
| Individual AD identity | az acr login in Azure CLI
Connect-AzContainerRegistry in Azure PowerShell |
Interactive push/pull done by developers, testers | Yes | AD token has to be renewed for every 3 hours |
| AD service principal | docker login
az acr login in Azure CLI Connect-AzContainerRegistry in Azure PowerShell |
Unattended push from CI/CD pipeline
Unattended pull to Azure or external services |
Yes | The password default expiry of SP is 1 year |
| AKS cluster managed identity | Attach registry when AKS cluster gets created or updated | Unattended pull to AKS cluster in the same or a varied subscription | No, pull access available | Only available with AKS cluster
Can’t be used for cross-tenant authentication |
Node security
AKS nodes are virtual machines in Azure that you have full control over and are responsible for maintaining. Linux nodes use an optimized Ubuntu distribution and the Moby container runtime, while Windows Server nodes use an optimized Windows Server 2019 release and the Moby container runtime as well. When you create or scale up an AKS cluster, the nodes are automatically provisioned with the latest OS security updates and configurations.
Azure platform applies OS security patches to Linux nodes every night, but if a Linux OS security update requires a reboot, it will not be performed automatically. You can reboot the Linux nodes manually or use Kured, an open-source reboot daemon for Kubernetes that runs as a DaemonSet and monitors each node for the presence of a file indicating that a reboot is needed. Reboots are managed throughout the cluster using the same cordon and drain process as a cluster upgrade.
RBAC roles
| Roles | Access |
| Owner | Access Resource Manager, Create/delete registry, push or pull image, delete image data, change policies |
| Contributor | Access Resource Manager, Create/delete registry, push or pull image, delete image data, change policies |
| Reader | Access Resource Manager, pull image |
| AcrPush | push or pull image |
Specify security requirements for container orchestration
A container orchestrator is responsible for managing the containers of an application. Orchestration involves automating all aspects of application management, from initial placement and scheduling to steady-state activities like health monitoring, scaling, and failover support.
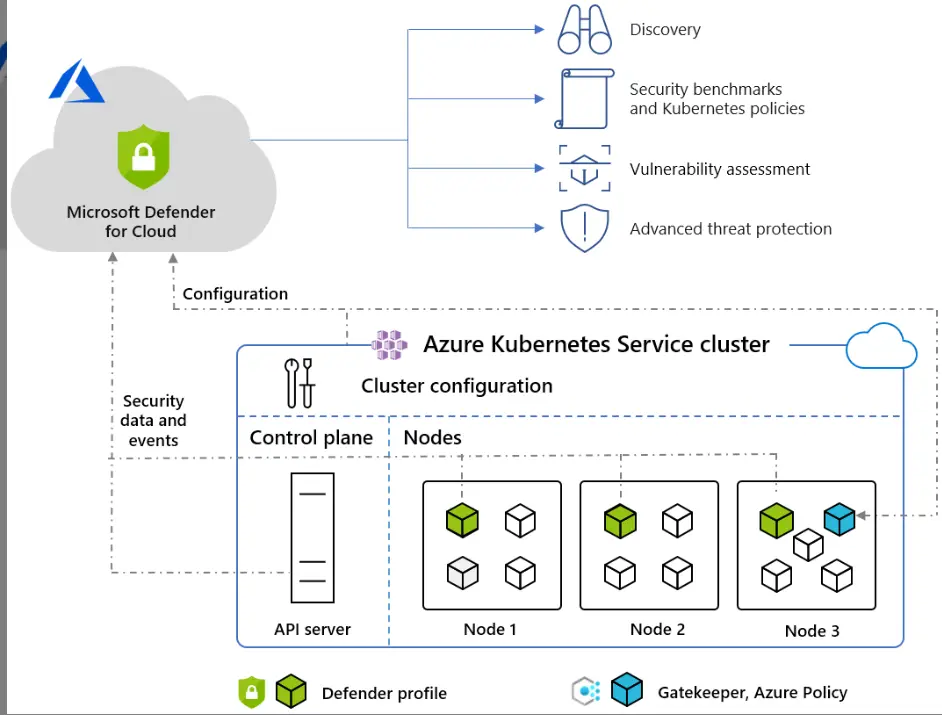
Kubernetes, which is the most widely used container orchestration system and has grown rapidly as an open-source project, has become an essential component of many companies’ computing infrastructure. The Azure platform provides three services that simplify the deployment and management of Kubernetes clusters.
By enabling Microsoft Defender for Containers, protection is automatically enabled for both Azure Kubernetes Service clusters and Azure Arc-enabled Kubernetes clusters (Preview). With this feature, you can also configure Kubernetes data plane hardening.
Security recommendations related to this feature will be displayed in the Defender for Cloud dashboard.
In the case of Azure Kubernetes Service clusters, audit log data is collected in a frictionless and agentless manner. Each node is deployed with a Defender profile, which provides runtime protection and signals collection. The Azure Policy add-on for Kubernetes is responsible for collecting cluster and workload configuration for admission control policies, as explained in the “Protect your Kubernetes workloads” guide. The following diagram provides an overview of this solution:
The Defender profile comprises a DaemonSet, a group of containers that gather inventory and security events within the Kubernetes environment. Additionally, it includes Gatekeeper, Azure Policy, which serves as the admission controller webhook for Open Policy Agent (OPA), to enforce and maintain safeguards on your clusters in a centralized and consistent manner at scale.
Summary
Hope this blog covers the complete information on how to design a security strategy for securing cloud service models. With the insights provided, you can be able to monitor, troubleshoot and optimize all the resources including public clouds and private data centers.
If you want to further enrich your career in cybersecurity, choose SC-100 certification and you can learn the basic things about cybersecurity in detail.
If you have further queries on this blog post, please feel free to comment us!
- Study Guide DP-600 : Implementing Analytics Solutions Using Microsoft Fabric Certification Exam - June 14, 2024
- Top 15 Azure Data Factory Interview Questions & Answers - June 5, 2024
- Top Data Science Interview Questions and Answers (2024) - May 30, 2024
- What is a Kubernetes Cluster? - May 22, 2024
- What are the Roles and Responsibilities of an AWS Sysops Administrator? - March 28, 2024
- How to Create Azure Network Security Groups? - March 15, 2024
- What is the difference between Cloud Dataproc and Cloud Dataflow? - March 13, 2024
- What are the benefits of having an AWS SysOps Administrator certification? - March 1, 2024