Cloud IAM or Identity and Access Management service intend to allow you granular access to the specific resources within Google Cloud. Along with that, it also prevents unauthorized access to any of the respective resources. Google Cloud IAM is more like the security principle of the cloud services, which clearly states that no one should get the additional permissions that are not authorized by the main user. As the technology environments of the organizations are growing with several cloud resources under Google, there is a strong need for ensuring appropriate access to protect their integrity and data security.
Traditionally, before cloud services were popular, the companies used on-premises IAM software. It was then satisfactorily offering identity management policies to meet the specific accessibility control demands. But with time, when the organizations are implementing more cloud services to operate their business aspects, the identity and access management process became complex. And the traditional software measures were not effective anymore. Therefore, it was important for the organizations to switch to cloud-based IAM solutions for implementing a logical management step.
Interested in Google Cloud Certifications? Check out Whizlabs online courses, practice tests and free tests here!
Cloud IAM by Google has earned a great name upon its security prospects. Most of the organizations who are new to Google Cloud, and its resources, should have a clear idea of what is Google IAM Cloud. Knowing about this feature or service is what will ensure the future of data and resource security for those companies.
Working Overview of Google Cloud IAM
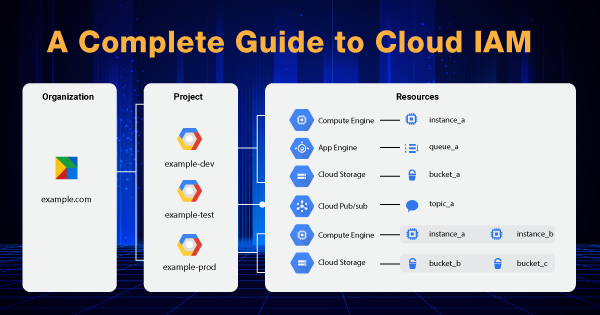
With Identity and Access Management, you get the authorization to control the accessibility to select resources. It means that you will be defining the identity, who will be having access or role to interfere with a particular cloud resource. Some of the cloud resources by Google include Compute Engine VM instances, GKE Clusters, and others. Not just these, but the projects upon which you are working, and the folders that have critical information about your resources can also be limited with access control by Cloud IAM.
With IAM, there is no such granting of permission directly to the person who has requested for the same. Instead, all of the permissions are in groups, depending upon the roles. And the roles are specified to only the members who are authenticated by the organization that has adopted Google Cloud IAM for their resources.
The IAM policy within Google Cloud defines and gives the assigned roles to select members. And then, this policy is attached with one of the several cloud resources! And when any of the members makes an attempt to access that particular resource, the IAM policy verifies whether the member is authenticated or not. Based upon their authentication, IAM checks whether they are permitted to carry on with the action or not.
Read more about Introduction to Google Cloud Platform!
Different policies are made for different resources, and the authentication process is strictly according to that! The entire model or architecture of Access management comes with three major parts, which include Member, Role, and Policy. Here is a brief definition for all of them:
1. Member
The member is specified as end-users or can be any of the Google accounts, service accounts, Google group, or a Cloud Identity domain that has the permission to access a select resource. The member’s identity is linked to his/her email address, Google group, or service account. If not that, then the member must have a domain name that is in association with the Cloud Identity domains or Google Workspace.
2. Role
Role is termed a collection of several permissions. The permissions are the major elements that hold power to determine the operations that are allowed upon a resource. When you, as the owner, grant a role to any member, then you are eventually granting them all of the permissions that are embedded within that role.
3. Policy
IAM policy is again a collection of several roles. It is more like the role bindings that bind more than one member to specific roles. When you intend to define what member should possess what access or role over a resource, you must create an IAM policy and then attach it to the resource.
A collective integration of these three elements is what makes the Google Cloud IAM functional and operational. Cloud IAM is rich in offering access control interface, enhanced security, and resource-level accessibility control to help a user with all-around protection for the cloud platform services, applications, and resources. Cloud IAM means to help you with different attributes that include:
-
- You will have to spend less over enterprise security by relying upon the centralized model of trust for dealing with Identity and Access Management.
- Moreover, Cloud IAM intends to help your end-users to work from any device or location without any hassle.
- With just one role, you can give access to your end-users for all of the applications or resources.
- You can also implement multi-factor authentication for adding extra security for some sensitive resources, data, or apps.
- The compliance of processes & procedures is maintained with cloud IAM solutions. It means that there should be a problem of providing unnecessary privileges to the end-users or employees by not revoking their accessibility when they complete their tasks over the resource, application, or project folder. Cloud IAM by Google intends to offer that management prospect with its IAM policies.
The best part is that all of the use associated with Identity and Access Management API has no additional charges upon your bills. You just pay for the resources and services that you use within Google Cloud. And Google Cloud IAM is a complementary security and access management service by the tech giant.
Different Types of Members within Google Cloud IAM
Google Cloud IAM allows you to offer access to diverse members. They are of different types that include:
1. Google Account
A Google account intends to represent an administrator, developer, or anyone who has some interaction with Google Cloud. Any email address that is connected to a Google Account can be considered as an identity. Hence, this also includes the domain ‘gmail.com’ and others. If you intend to sign-up for a Google Account, you can head to the sign-up page for it.
2. Service Account
It is not just an individual account but an account for the entire application. When you are running the code that is being hosted over the Google Cloud platform, the code is also running upon the accounts that you specify. You can create different service accounts for representing varying logical components of the application. You can get an idea upon using the service account upon the application by referring to this link!
3. Google Workspace Domain
Google Workspace Domain represents the virtual group of all Google Accounts. All of these Google accounts are created within the Google Workspace account. The Google workspace domains then represent the internet domain name of the organization. When you successfully add the user to the workspace domain of Google, a new Account will be created for the respective user. Hence, this account will be within that virtual group!
4. Cloud Identity Domain
Cloud Identity Domain is just similar to that of Google Workspace domain. It is so because it represents the virtual group of all of the Google Accounts within an organization. The users of Cloud Identity domain do not have access to the Google Workspace features and applications. You can get a better glimpse into it by checking out the official documentation about Cloud Identity.
5. All Users and All Authenticated Users
All Authenticated Users is a special identifier that indicates all of the users and service accounts over the internet who are authenticated with the use of a Google Account. All users are also an identifier that has the potential of representing anyone who is over the internet, that includes authorized as well as unauthenticated users.
Types of Roles within the Google Cloud IAM
The roles are the elements within Cloud IAM by Google that hold the set of permissions. Therefore, it is important for you to know about the type of role under which permission exists. But before that, you should know about the different types of Cloud IAM roles that are:
1. Basic Roles
Basic roles include editor, viewer, and owner roles. These are the roles that existed even before IAM was introduced to the users. All of these roles are concentric, which means that the Owner role consists of the permissions in the Editor role. And the Editor role consists of the permissions within the Viewer role. You can make use of API, gcloud tool, or the Cloud Console to apply the basic roles to a service or project. To know how to use Cloud Console for granting roles, refer to this documentation.
2. Pre-Defined Roles
The pre-defined roles offer granular access to the specific services that are managed by Google Cloud. It gives access to the resources within Google Cloud and considers preventing unwanted access to all of the other resources. Google maintains these roles and considers updating the permissions as per necessity. It usually happens when Google adds new services or features.
3. Custom Rules
It is a type of role under which you can provide a granular mode of access to the user-specific permission list. As there are predefined roles, Google Cloud IAM is also offering the flexibility to users for creating their own IAM roles. You can add one or more select permissions upon a custom role. And then, you can grant that role to the users, who are an integral part of your organization. Here is the official documentation to give you a clear idea of how to create and manage the custom roles.
If you intend to know more in-depth about the role types within cloud IAM, then refer to this documentation. It has a clear explanation of every bit of information associated with different role types. Along with that, it will also explain to you how Cloud IAM allows you to manage those roles.
Conceptual Features of Google Cloud IAM
As of now, you are well-versed with how Google Cloud IAM manages accessibility and identity control. But there are several conceptual features that make it even better. Therefore, as you have understood the working of Cloud IAM, it is better to head out and end the guide with a plethora of features embedded with it. The features include:
1. Enterprise-Grade Control over Accessibility
The administrators within an organization can implement Google Cloud IAM to authorize people or employees to gain access to specific resources. It offers complete control & visibility to the administrators for managing the cloud resources through a central security portal.
2. Smart Accessibility Control
As managing the permissions might be difficult for the owner or administrator, they prefer to use Recommender to simplify the task. Recommender intends to remove all of the unwanted accessibility to the Cloud resources over Google. It is done with the help of Machine Learning for making recommendations upon implementing smart access controls.
With the use of Recommender, the security team of your organization will be able to detect the over-permissive accesses. And then, they can also set them right, based upon the access patterns of other similar users within the organization.
3. Easy Creation of the Enterprise Identity
You can go ahead and use Cloud Identity, which is the built-in managed identity service of Google Cloud, for creating and syncing the user accounts. You can create your enterprise identity over the projects and applications with the use of Cloud Identity. With Cloud Identity, it is easy to manage and provision the users & groups. You can also gain access to the Google Cloud Organization, which will enable you to manage the projects centrally, with the use of a resource manager.
Final Words
The flexible roles within Google Cloud IAM are what have made it an integral element of security for organizational resources. To provide ease to the organization’s compliance processes, it also implements a full audit trail that is only made available to the administrators without putting in any of the additional efforts.
IAM is free from all the charges, and you will just have to pay the charges associated with other Google Cloud services. You will get control of managing the IAM policies over the central console of Google Cloud. So, explore the efficacy of Google Cloud IAM by setting up the roles and IAM policies within the console.
- Cloud DNS – A Complete Guide - December 15, 2021
- Google Compute Engine: Features and Advantages - December 14, 2021
- What is Cloud Run? - December 13, 2021
- What is Cloud Load Balancing? A Complete Guide - December 9, 2021
- What is a BigTable? - December 8, 2021
- Docker Image creation – Everything You Should Know! - November 25, 2021
- What is BigQuery? - November 19, 2021
- Docker Architecture in Detail - October 6, 2021



Great post. thanks.