Are you looking for SC-900 exam questions ? – This blog post has free questions and answers on SC-900 certification exam which acts as a preparation guide for your real exam. The SC-900 exam is intended for the ones looking forward to learning and attesting their knowledge on the fundamentals of Compliance, Security and Identity, across Cloud-based and relevant Microsoft services.
Who this exam is intended for?
It enwraps students, new and experienced IT Professionals, Business Stakeholders, or anyone trying their hand in the field of Microsoft Security, Identity and Compliance solutions.
Prerequisites
Candidates appearing for the SC-900 certification are presumed to be familiar with the concepts of Microsoft 365 and Azure. They should have an understanding of how Microsoft Security, Identity, and Compliance solutions span across the solution zones to give an overall end-to-end solution.
This certification tests you for your understanding of Microsoft Identity and Access Management solutions, Microsoft’s security solutions and compliance solutions capabilities, and the concepts of security, identity, and compliance.
By undergoing these questions, You will be able to understand the certification requirements and the concepts covered in the exam. Microsoft certifications seem hard at first look, but with the right training and resources, are easy to crack. Let’s start learning!
Exam Domain for SC-900 exam:
Here comes the SC-900 exam on Microsoft Security, Compliance, and Identity Fundamentals skillsets overview as follows:
- Describing the concepts of security, compliance, and identity (10—15%)
- Describing the capabilities of Microsoft identity and access management solutions (25-30%)
- Describing the capabilities of Microsoft Security solutions (25—30%)
- Describing the capabilities of Microsoft compliance solutions (25-30%)
Domain : Describe the concepts of security, compliance, and identity
Q1 : Your company is planning on using Azure Cloud services. They are looking at the different security aspects when it comes to Microsoft privacy. Is Transparency a key Microsoft privacy principal?
A. Yes
B. No
Correct Answer: A
Explanation:
Below are the key privacy principals as addressed by Microsoft
Control
Transparency
Security
Strong legal protections
No content-based targeting
Benefits to you
When it comes to Transparency, Microsoft tells us that they are transparent when it comes to data collection.
For more information on Microsoft Privacy control , please refer to the below URL: https://privacy.microsoft.com/en-US/
Domain : Describe the concepts of security, compliance, and identity
Q2 : Your company is planning on using Azure Cloud services. They are looking at the concept of the Zero Trust principle. Is Verify explicitly a Zero Trust principle?
A. Yes
B. No
Correct Answer : A
Explanation:
Yes. Here you have to ensure that not everyone is provided access to a system. Here you should always authenticate and authorize users.
The principles when it comes to Zero trust are
Verify explicitly
Use least privileged access
Assume breach
For more information on the Zero Trust Principle , please refer to the below URL: https://www.microsoft.com/en-us/security/business/zero-trust
Domain : Describe the concepts of security, compliance, and identity
Q3 : Your company is planning on using Azure Cloud services. Which of the following can be used to ensure that data can be read only by authorized users?
A. Encryption
B. Deduplication
C. Archiving
D. Compression
Correct Answer : A
Explanation:
You can ensure data is encrypted. Then only authorized users would have the encryption key. The encryption key can then be used to decrypt and read the data.
Option B is incorrect since this is normally used to eliminate duplicate copies of repeating data
Option C is incorrect since this is normally used to store data that is not used that frequently
Option D is incorrect since this is normally used to reduce the storage size of data
For more information on encryption in Microsoft Cloud , please refer to the below URL: https://docs.microsoft.com/en-us/microsoft-365/compliance/office-365-encryption-in-the-microsoft-cloud-overview?view=o365-worldwide
Domain : Describe the capabilities of Microsoft identity and access management solutions
Q4 : A company is planning on using Azure Active Directory. Which of the following is used to describe the exact term for Azure Active Directory?
A. Federation server
B. Identity Provider
C. Proxy server
D. Firewall
Correct Answer : B
Explanation:
Azure Active Directory is Microsoft’s identity provider. This is used for storage of identities and for access management. Both Azure and Microsoft Office 365 can use Azure Active Directory for identity and access management
All of the other options are incorrect since Azure Active Directory is used for identity and access management.
For more information on Azure Active Directory , please refer to the below URL: https://docs.microsoft.com/en-us/azure/active-directory/fundamentals/active-directory-whatis
Domain : Describe the capabilities of Microsoft identity and access management solutions
Q5 : Your company is planning on using Azure Active Directory for the storage of identities. They want to make use of the self-service password reset feature. Which of the following authentication methods are available for self-service password reset? Choose 3 answers from the options given below
A. Email
B. A passport identification number
C. A picture message
D. Mobile app notification
E. Mobile app code
Correct Answers: A, D and E
Explanation:
Below are the authentication methods available for self-service password reset
Mobile app notification
Mobile app code
Email
Mobile phone
Office phone
Security questions
Since the authentication methods are clearly mentioned, all other options are incorrect
For more information on self-service password reset , please refer to the below URL: https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-sspr-howitworks
Domain : Describe the capabilities of Microsoft identity and access management solutions
Q6 : Your company is planning on making use of Azure Active Directory. Do all versions of Azure Active Directory provide the same set of features?
A. Yes
B. No
Correct Answer : B
Explanation:
There are different pricing models available for Azure Active Directory. The most basic version is the Free model. Here there is a limitation in terms of features. For example, you will not get features such as
A service level agreement
Self-service password reset for cloud users
Group access management
For more information on Azure AD Pricing , please refer to the below URL: https://azure.microsoft.com/en-us/pricing/details/active-directory/
Domain : Describe the capabilities of Microsoft security solutions
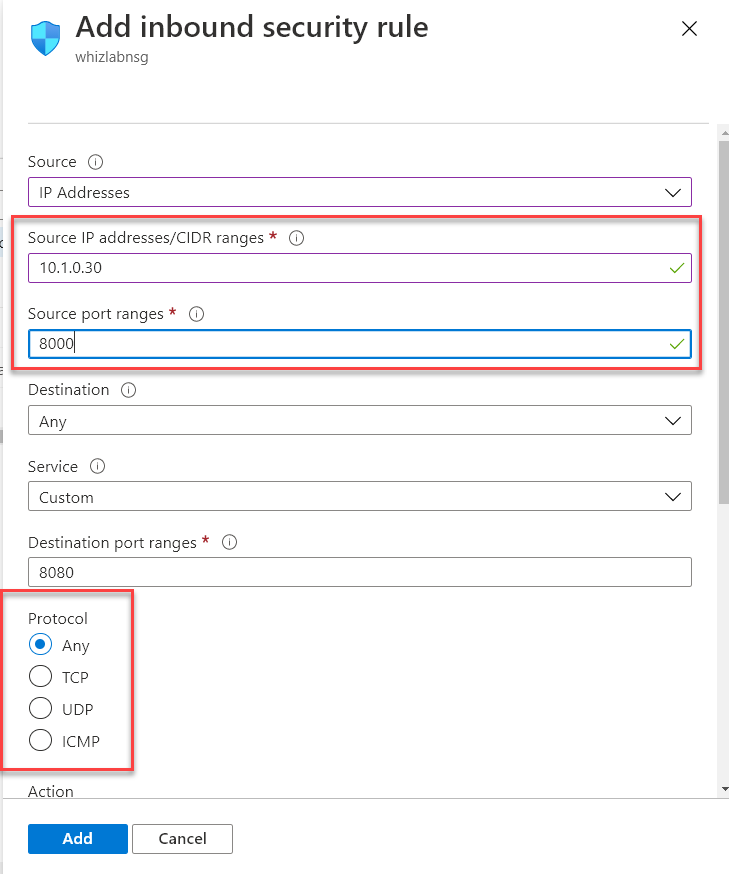
Q7 : Your company is planning on making use of Network Security Groups. Can you make use of network security groups to filter traffic based on the IP address, protocol and port number?
A. Yes
B. No
Correct Answer : A
Explanation:
For a network security group rule, you can create a rule that is based on the IP address, the protocol and the port number. An example screenshot is given below which shows the IP address, the protocol and the port number.
For more information on Azure network security groups , please refer to the below URL: https://docs.microsoft.com/en-us/azure/virtual-network/network-security-groups-overview
Domain : Describe the capabilities of Microsoft identity and access management solutions
Q8 :Your company is planning on using Azure AD Identity Protection. Can you use Azure AD Identity protection to provide access to resources in Azure?
A. Yes
B. No
Correct Answer : B
Explanation:
Azure AD Identity protection is used to identify risks based on the user sign-in process. It is not used to provide access to resources in Azure.
For more information on Azure AD Identity Protection , please refer to the below URL: https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/overview-identity-protection
Domain : Describe the capabilities of Microsoft security solutions
Q9 : You have to decide on the right service to use based on the requirement. Which of the following would you use for the below requirement?
“Provide Network address translation”
A. Azure Bastion
B. Azure Firewall
C. Network Security Groups
D. Azure DDoS Protection
Correct Answer : B
Explanation:
The Azure Firewall service has the facility to translate traffic via its public IP address to private IP addresses to virtual networks
Option A is incorrect since this provides a service to RDP/SSH into your Azure virtual machines
Option C is incorrect since this is used to filter the traffic to your Azure virtual machine
Option D is incorrect since this is used to protect your Azure resources against large scale attacks from the Internet
For more information on the Azure Firewall feature , please refer to the below URL: https://docs.microsoft.com/en-us/azure/firewall/features#inbound-dnat-support
Domain : Describe the capabilities of Microsoft security solutions
Q10 : You have to decide on the right service to use based on the requirement. Which of the following would you use for the below requirement?
“Provide a secure way to RDP/SSH into Azure virtual machines”
A. Azure Bastion
B. Azure Firewall
C. Network Security Groups
D. Azure DDoS Protection
Correct Answer : A
Explanation:
The Azure Bastion service is a managed service that allows you to connect to an Azure virtual machine via the browser and the Azure portal.
Option B is incorrect since this is a managed firewall service
Option C is incorrect since this is used to filter the traffic to your Azure virtual machines
Option D is incorrect since this is used to protect your Azure resources against large scale attacks from the Internet
For more information on the Azure Bastion service , please refer to the below URL: https://docs.microsoft.com/en-us/azure/bastion/bastion-overview
Domain : Describe the capabilities of Microsoft security solutions
Q11 : You company is planning on using the Microsoft Defender for Endpoint service. Can you use Microsoft Defender for Endpoint to protect Windows 10 machines?
A. Yes
B. No
Correct Answer : A
Explanation:
Yes, Windows 10 devices are also supported for Microsoft Defender for Endpoint service
For more information on the on-boarding devices for Microsoft Defender for endpoint, please refer to the below URL: https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/onboard-configure
Domain : Describe the capabilities of Microsoft compliance solutions
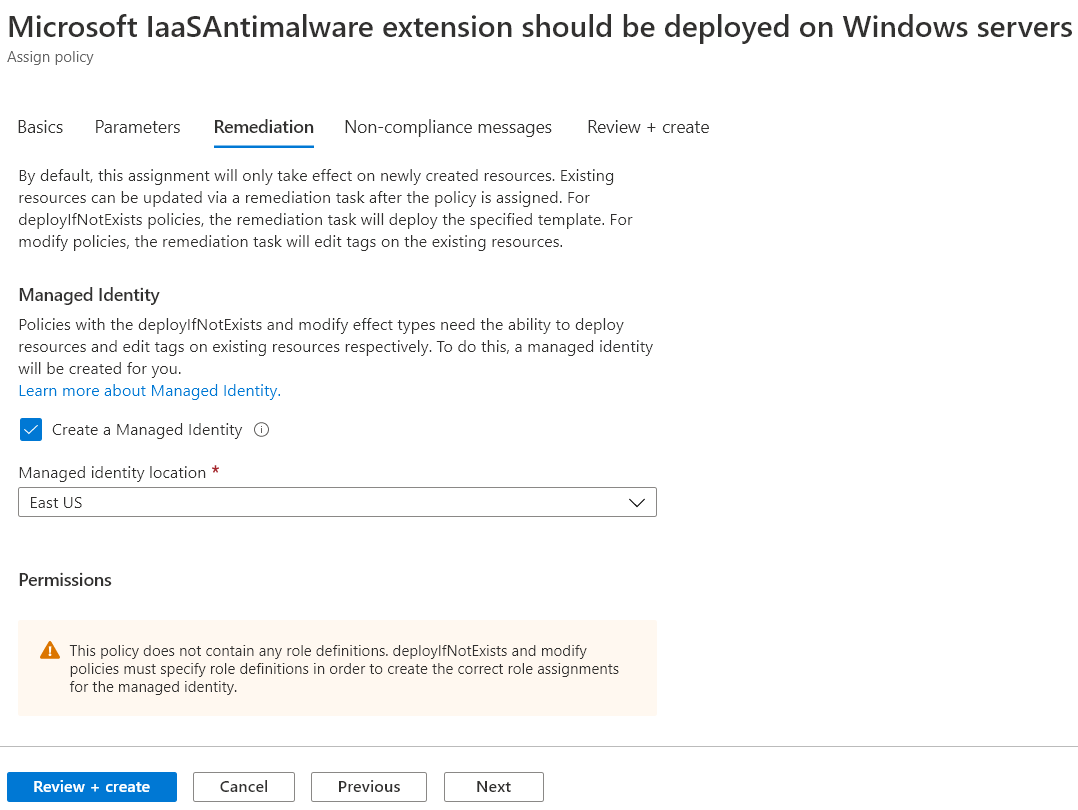
Q12 : Your company has just set up an Azure subscription. They have the following requirements
“Be able to deploy a set of resources, resource groups, role assignments to a set of subscriptions.”
“Be able to ensure no one can delete resources defined in a resource group named whizlabs-staging”
“Ensure that all Windows Servers defined as Azure virtual machines should have the Microsoft IaaS Antimalware extension installed”
Which of the following can be used for the following requirement?
“Be able to deploy a set of resources, resource groups, role assignments to a set of subscriptions.”
A. Azure Policy
B. Azure Blueprints
C. Azure AD Identity Protection
D. Azure Resource locks
Correct Answer: B
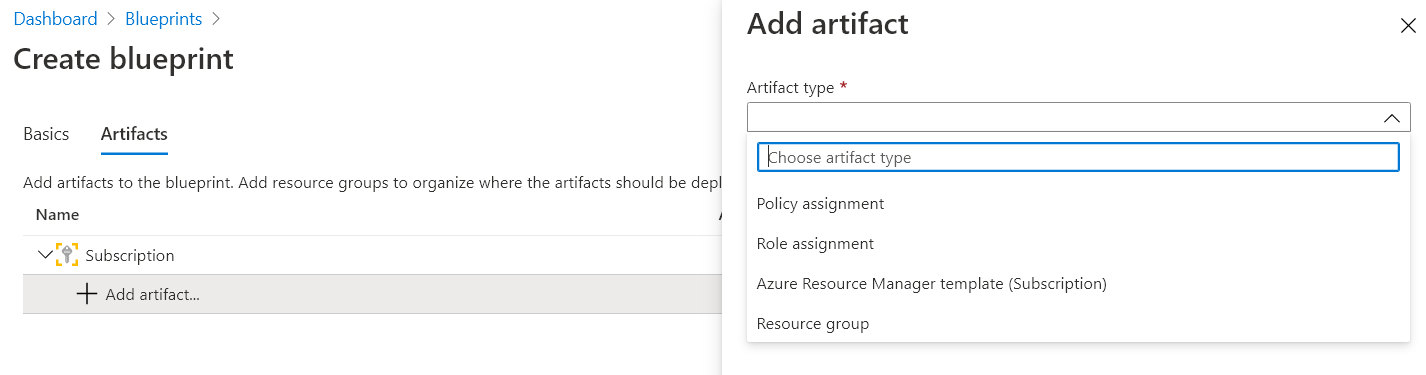
Explanation:
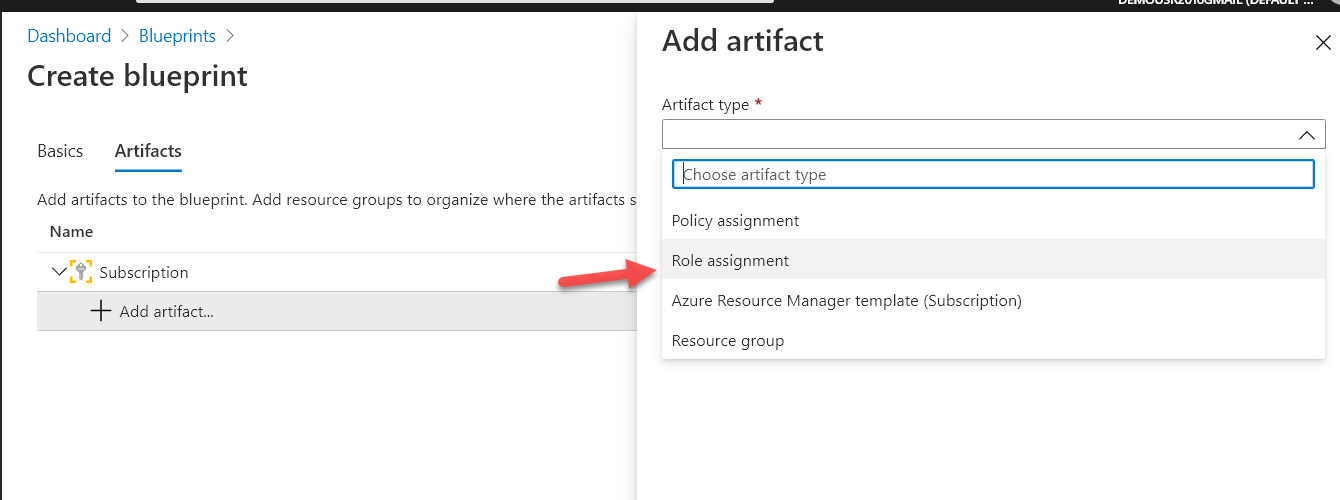
You can use Azure Blueprints to deploy a set of artifacts. The artifacts can be resources as ARM templates, resource groups and role assignments.
Below is a screenshot of the artifacts that can be deployed via Azure Blueprints
Option A is incorrect since this is used as a governance for your resources defined as part of your Azure account
Option C is incorrect since this is used to protect your identities in Azure AD
Option D is incorrect since this is used to prevent the accidental deletion and modification of resources in Azure
For more information on Azure Blueprints, please refer to the below URL: https://docs.microsoft.com/en-us/azure/governance/blueprints/overview
Domain : Describe the capabilities of Microsoft compliance solutions
Q13 : You are considering the use of sensitivity labels in Microsoft 365. Do sensitivity labels add a header and footer to the underlying Office 365 document for which the label is applied?
A. Yes
B. No
Correct Answer: A
Explanation:
When you apply a sensitivity label to a document, it will also add a header and footer to the document.
For more information on Sensitivity labels for Microsoft 365, please refer to the below URL: https://docs.microsoft.com/en-us/microsoft-365/compliance/sensitivity-labels?view=o365-worldwide
Domain : Describe the capabilities of Microsoft compliance solutions
Q14 : Your company is looking at the different options available when it comes to security solutions for Microsoft 365. Below are the key requirements
Search for email in Exchange mailboxes, documents in Sharepoint sites and OneDrive locations
Restrict communication and collaboration between two groups to avoid a conflict of interest in the organization
Provide access to a Microsoft support engineer to a user’s Exchange Online data
Provide just-in-time access to users in Microsoft Office 365 Exchange Online
Which of the following can be used for the following requirement?
“Provide access to a Microsoft support engineer to a user’s Exchange Online data”
A. Information Barriers
B. Content Search Tool
C. Customer Lockbox
D. Privileged Access Management
Correct Answer: C
Explanation:
Sometimes Microsoft Engineers need access to user’s data to diagnose an issue. This can be done with the help of the Customer Lockbox feature.
Option A is incorrect because this is used to restrict communication and collaboration between two groups to avoid a conflict of interest in the organization
Option B is incorrect because this is used to search for content in Exchange mailboxes, documents in SharePoint sites and OneDrive locations
Option D is incorrect because this is used to give just-in-time access to services in Microsoft 365
For more information on Customer Lockbox, please refer to the below URL: https://docs.microsoft.com/en-us/microsoft-365/compliance/customer-lockbox-requests?view=o365-worldwide
Domain : Describe the capabilities of Microsoft identity and access management solutions
Q15 : Your company wants to start making use of Azure. They are looking at different security aspects when it comes to using Azure. Which of the following could be used for the following requirement?
“Be able to sync users from the on-premises Active Directory onto Azure AD”
A. Azure AD Identity Management
B. Azure Conditional Access
C. Azure AD Roles
D. Azure AD Connect
Correct Answer: D
Explanation:
Azure AD Connect is used to synchronize identities from the on-premises Active Directory onto Azure Active Directory. There are different methods available for user identity synchronization.
Option A is incorrect since this is used to protect identities in Azure
Option B is incorrect since this is used to provide Conditional access to Azure
Option C is incorrect since this is used to assign permissions to users for manage various aspects in Azure Active Directory
For more information on roles in Azure Active Directory Connect , please refer to the below URL: https://docs.microsoft.com/en-us/azure/active-directory/hybrid/whatis-azure-ad-connect
Domain : Describe the capabilities of Microsoft compliance solutions
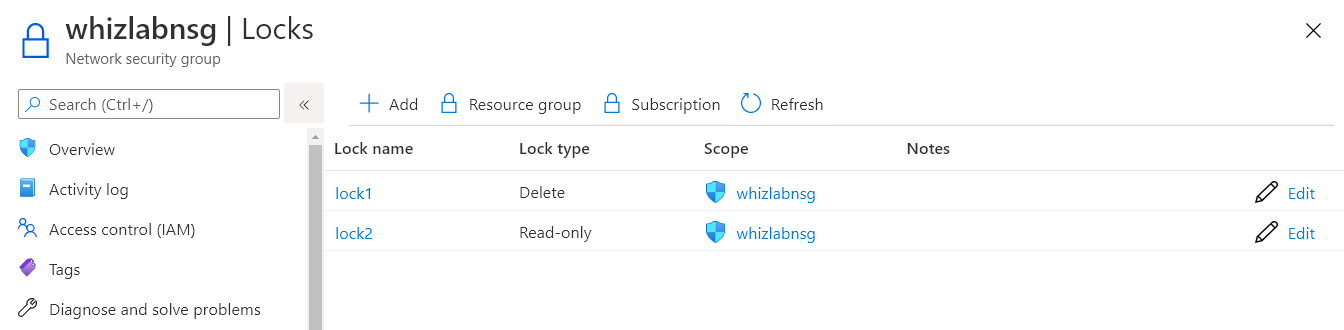
Q16 : You have a set of resources in Azure. Can you add a delete lock to a resource that already has a read-only lock?
A. Yes
B. No
Correct Answer: A
Explanation:
Yes, this is possible. Below is a screenshot of both types of locks assigned to a resource
For more information on Azure resource locks , please refer to the below URL: https://docs.microsoft.com/en-us/azure/azure-resource-manager/management/lock-resources
Domain : Describe the capabilities of Microsoft security solutions
Q17 : Which of the following is a scalable, cloud-native, security information event management and security orchestration automated response solution?
A. Azure Sentinel
B. Azure Security Center
C. Azure Active Directory
D. Azure AD Identity Protection
Correct Answer: A
Explanation:
You can use Azure Sentinel as a scalable, cloud-native, security information event management and security orchestration automated response solution. Azure Sentinel has the capability to ingest data from a variety of sources and performance threat monitoring on that data.
Option B is incorrect because Azure Security Center can give various security metrics and recommendations for your environment, but it can’t provide a complete orchestration and response-based solution
Option C is incorrect because this is your identity-based solution in Azure
Option D is incorrect because this is used to protect your identities in Azure
For more information on Azure Sentinel , please refer to the below URL: https://docs.microsoft.com/en-us/azure/sentinel/overview
Domain : Describe the capabilities of Microsoft compliance solutions
Q18 : Your company is currently looking at using the Azure Policy service. Can the Azure Policy service be used to remediate issues that get detected via its compliance checks?
A. Yes
B. No
Correct Answer: A
Explanation:
Some of the policies in Azure Policy has a Remediation section. This can be used to remediate issues if the resources are found to be not complaint with the policy.
For more information on the Azure Policy service , please refer to the below URL: https://docs.microsoft.com/en-us/azure/governance/policy/overview
Domain : Describe the capabilities of Microsoft compliance solutions
Q19 : Your company is planning on making use of Azure Blueprints. Can Azure Blueprints be used to create role assignments for an Azure subscription?
A. Yes
B. No
Correct Answer: A
Explanation:
When you create an Azure Blueprint , you can create multiple artifacts as part of the Blueprint. One of them is role assignments. A screenshot of this is given below
For more information on the Azure Blueprints , please refer to the below URL: https://docs.microsoft.com/en-us/azure/governance/blueprints/overview
Domain : Describe the capabilities of Microsoft security solutions
Q20 : Which of the following provides advanced and intelligent protection of Azure and hybrid resources and workloads?
A. Azure Defender
B. Azure Policies
C. Azure Blueprints
D. Azure Active Directory
Correct Answer: A
Explanation:
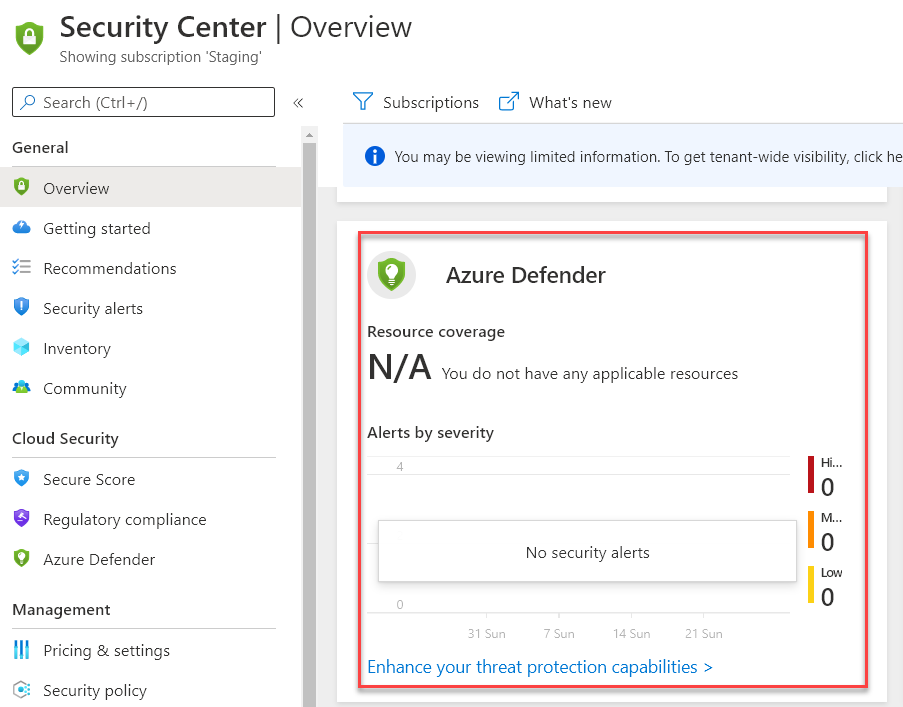
With Azure Defender , you can enable intelligent protection of your resources that are defined in Azure and also in your on-premises infrastructure.
This is an additional security feature that comes as part of Azure Security Center as shown below
Option B is incorrect since this is used for governance of resources in your Azure account
Option C is incorrect since this is used for the deployment of various artifacts to your Azure account
Option D is incorrect since this is used as an Identity store
For more information on the Azure Defender , please refer to the below URL: https://docs.microsoft.com/en-us/azure/security-center/azure-defender
Domain : Describe the capabilities of Microsoft security solutions
Q21 : Which of the following is available for the Azure Application Gateway service that helps to protect web applications from common exploits and vulnerabilities?
A. Azure Firewall
B. Azure Web Application Firewall
C. Azure Policy
D. Azure Identity Protection
Correct Answer: B
Explanation:
The Azure Web Application Firewall can be used along with the Azure Application Gateway resource to protect web applications from common exploits and vulnerabilities. It can help to protect against attacks such as SQL injection attacks or cross-site scripting attacks.
Option A is incorrect since this is managed firewall service for the resources that are part of your Azure virtual network
Option C is incorrect since this is used for governance of your Azure resources
Option D is incorrect since this is used to protect your Azure AD identities
For more information on the Azure Web Application Firewall , please refer to the below URL: https://docs.microsoft.com/en-us/azure/web-application-firewall/ag/ag-overview
Domain : Describe the capabilities of Microsoft identity and access management solutions
Q22 : Your company is planning on making use of Azure Active Directory Privileged Identity Management. Can Privileged Identity Management be used to provide time-bound assignments for Azure resources?
- Yes
- No
Correct Answer: A
Explanation:
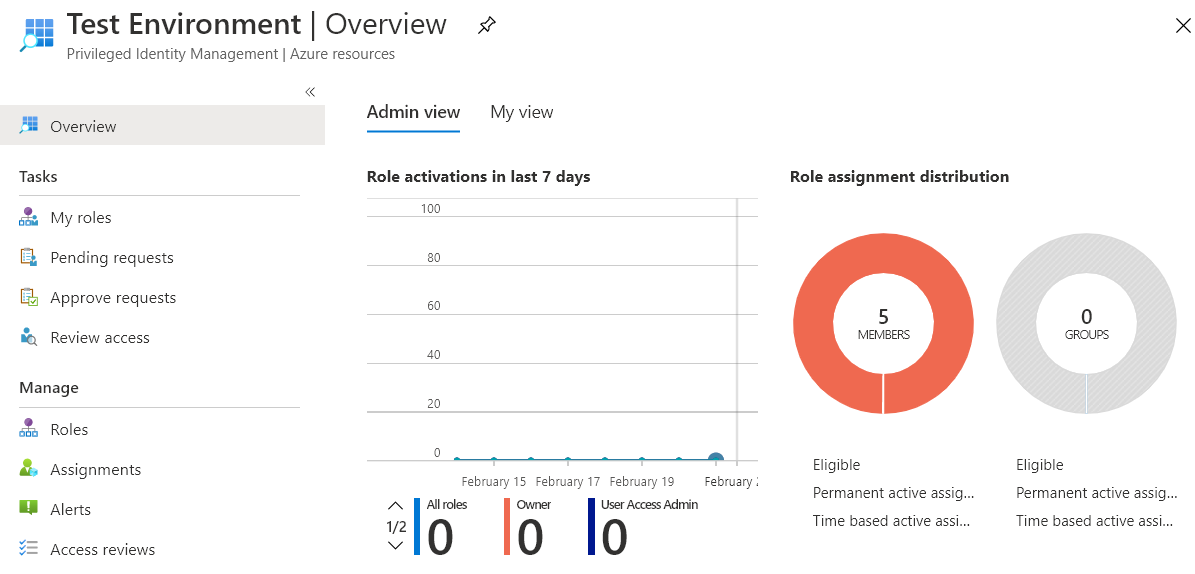
You can manage the access of users to Azure resources. You can also give time-bound access to Azure resources. Below is a screenshot of the quick start page of Privileged Identity Management for Azure resources
For more information on the Azure AD Privileged Identity Management with Azure roles , please refer to the below URL: https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-resource-roles-assign-roles
Domain : Describe the capabilities of Microsoft security solutions
Q23 : Which of the following maps to the below encryption technique?
“Encrypting information that resides in persistent storage on physical media”
A. Encryption in transit
B. Encryption at rest
C. In-memory Encryption
D. SSL Encryption
Correct Answer: B
Explanation:
Here this concept is mapped to the concept of ensuring that data is encrypted at rest. Here the data on the underlying physical media is encrypted.
The other options are all incorrect since the keyword of “rest” maps to data that resides on the physical device
For more information on Azure Encryption, please refer to the below URL: https://docs.microsoft.com/en-us/azure/security/fundamentals/encryption-overview
Domain : Describe the capabilities of Microsoft security solutions
Q24 : You are planning on using the Azure Firewall service. Can you use the Azure Firewall service to encrypt incoming network traffic to Azure virtual machines?
A. Yes
B. No
Correct Answer: B
Explanation:
The Azure Firewall service is a managed service that can be used to protect your Azure virtual network resources. But it can’t be used to encrypt the incoming traffic onto Azure virtual machines.
For more information on the Azure Firewall service, please refer to the below URL: https://docs.microsoft.com/en-us/azure/firewall/overview
Domain : Describe the capabilities of Microsoft identity and access management solutions
Q25 : You are looking at using Azure Active Directory Access Reviews. Can you use Azure AD Access reviews to review group memberships for users defined in Azure AD?
A. Yes
B. No
Correct Answer: A
Explanation:
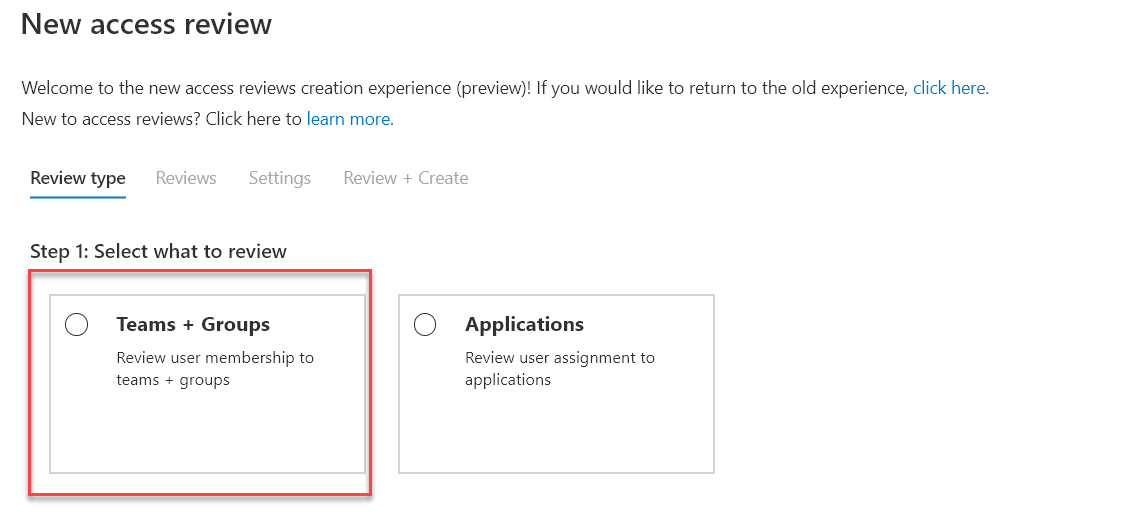
When you create an Access Review in Azure Active Directory, you can review the access of users to teams and groups as shown below
For more information on Azure AD Access reviews, please refer to the below URL: https://docs.microsoft.com/en-us/azure/active-directory/governance/access-reviews-overview
Summary
Hope you have enjoyed this post. These SC-900 exam questions give you an overall assessment of the exam. By hovering through these questions, you can get to know the pattern of the questions asked. To get a detailed view, take the practice tests further, and with their elaborate explanations, learn and understand the concepts.
- 25 Free Questions on MS-101: Microsoft 365 Mobility and Security - November 13, 2022
- What is Snowpipe & how does it works? - October 7, 2022
- Preparation Guide on DP-420 Designing and Implementing Cloud-Native Applications Using Microsoft Azure Cosmos DB Certification - September 12, 2022
- Preparation guide on MB-910: Microsoft Dynamics 365 Fundamentals (CRM) Certification Exam - August 5, 2022
- Snowflake Certifications – Which snowflake certification is best for you? - July 11, 2022
- All you need to know about Certified Ethical Hacker Certification - June 16, 2022
- What are Hands-On Labs? A beginner’s guide to Hands-on Labs - May 17, 2022
- 25 Free Question on Salesforce Administrator Certification - April 26, 2022




Wonderful Content!!