Are you studying for the MS-101: Microsoft 365 Mobility and Security certification exam? If so, you may need to practice on MS-101 exam questions about some of the topics covered on the exam. With this MS-101 exam, you can demonstrate your knowledge of Microsoft 365 security and compliance features, and show that you’re ready to implement these features in your organization.
Here we have the updated list of MS-101 practice questions on Microsoft 365 Mobility and security which are very relevant to the real exam as well.
Latest Updates : MS-101 will retire on September 30, 2023. A replacement exam, MS-102: Microsoft 365 Administrator(beta), is available.
Why do we provide Microsoft 365 Mobility and Security exam questions for free?
There are a few reasons why we offer MS-101: Microsoft 365 Mobility and Security exam questions for free.
First, we want to make sure that everyone has access to the latest and greatest information on Microsoft 365. By providing the MS-101 exam questions for free, we can help keep everyone up-to-date on the latest changes and news.
Second, we want to help people prepare for the certification exam. By providing the questions for free, we can help people get a head start on studying for the exam. Third, we want to show our support for the Microsoft 365 community. By providing the questions for free, we can help people who are using Microsoft 365 in their businesses or organizations.
We hope that these reasons why we offer MS-101: Microsoft 365 Mobility and Security questions for free will help you understand our motivations. We believe that by providing the MS-101 exam questions for free, we can help make Microsoft 365 a success for everyone.
Know About: Microsoft 365 Certification Path
What skills will you gain by obtaining MS-101 Microsoft 365 Mobility and Security exam?
One of the most important skills for the MS-101 certification exam is knowing how to configure and manage Microsoft 365 security settings. This includes understanding how to configure Azure Active Directory, Intune, and other security services. You can learn more about this by reading Microsoft 365 documentation, or by taking a free course on Microsoft Learn.
Another important skill for the MS-101 exam is knowing how to troubleshoot Microsoft 365 issues. This includes being able to troubleshoot issues with Exchange Online, SharePoint Online, and other Microsoft 365 services. You can learn more about this by reading Microsoft 365 documentation, or by taking a free course on Microsoft Learn.
Finally, it is also important to have a good understanding of Microsoft 365 licensing. This includes understanding the different types of licenses available, and how to configure them. You can learn more about this by reading Microsoft 365 documentation, or by taking a free course on Microsoft Learn.
By learning the skills we mentioned above, you will be well on your way to passing the MS-101 exam. And remember, you can always find more help and resources for studying for the exam on the Microsoft 365 Community website.
Let’s get started!
MS-101 Exam Questions on Microsoft 365 Mobility and Security
Domain : Implement modern device services
Question 1 : Whizlabs Inc has a Microsoft 365 tenant. You plan to allow users that are members of a group named Group_Hr Team to enroll their device in mobile device management (MDM).
The device limit restrictions are configured as shown in the following table.
| Priority | Name | Device limit | Assigned to |
| 1 | Group_HrTeam | 10 | Group_HrTeam |
| 2 | Head Office | 15 | Group_HrTeam |
| 3 | Mum_India | 20 | Test_Team |
| Default | All Users | 50 | All Users |
What is the device limit for the members of the Group_HrTeam group?
A. 10
B. 15
C. 20
D. 50
Correct Answer: A
Explanation:
The device limit set based on highest priority for Group_HrTeam is 10.
Device limit 15 is incorrect because it has a lower priority.
Device limit 20 is incorrect because Group_HrTeam is not part of this priority.
The default device limit does not implicitly assign to Group_HrTeam.
Domain : Manage Microsoft 365 security and threat management
Type: Drag & Drop – Matching
Question 2 : Whizlabs Inc. has a Microsoft 365 subscription. You are a global administrator in Microsoft 365, and you are given a responsibility to grant appropriate permissions to newly joined employees. Details of roles and the responsibility are as below:
| Responsibility | Roles |
| View and manage user’s email mailboxes, Microsoft 365 groups, and Exchange Online | A. Office Apps admin |
| Use the Office cloud policy service to create and manage cloud-based policies | B. Security administrator |
| Control organization’s overall security by managing security policies, reviewing security analytics and reports across Microsoft 365 products, and staying up-to-speed on the threat landscape. | C. Compliance administrator |
| Help organizations stay compliant with any regulatory requirements, manage eDiscovery cases, and maintain data governance policies across Microsoft 365 locations, identities, and apps. | D. Exchange admin |
Please match the correct role to each responsibility. The solution must use the principle of least privilege:
Correct Answer:
| Responsibility | Roles |
| View and manage user’s email mailboxes, Microsoft 365 groups, and Exchange Online | D. Exchange admin |
| Use the Office cloud policy service to create and manage cloud-based policies | A. Office Apps admin |
| Control organization’s overall security by managing security policies, reviewing security analytics and reports across Microsoft 365 products, and staying up-to-speed on the threat landscape. | B. Security administrator |
| Help organizations stay compliant with any regulatory requirements, manage eDiscovery cases, and maintain data governance policies across Microsoft 365 locations, identities, and apps. | C. Compliance administrator |
Explanation:
Exchange admin – With exchange admin permissions users can view and manage mailboxes, Microsoft 365 groups, and Exchange Online.
Office Apps admin – With this permission, one can configure an office cloud policy service to create and manage cloud-based policies
Security administrator – Security Administrator permission allows you to control an organization’s overall security by managing security policies, reviewing security analytics, and reports across Microsoft 365 products, and staying up-to-speed on the threat landscape.
Compliance administrator – Compliant administrator permission helps organizations stay compliant with any regulatory requirements, manage eDiscovery cases, and maintain data governance policies across Microsoft 365 locations, identities, and apps.
References: https://docs.microsoft.com/en-us/microsoft-365/admin/add-users/about-admin-roles?view=o365-worldwide, https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/permissions-microsoft-365-security-center?view=o365-worldwide
Domain : Implement modern device services
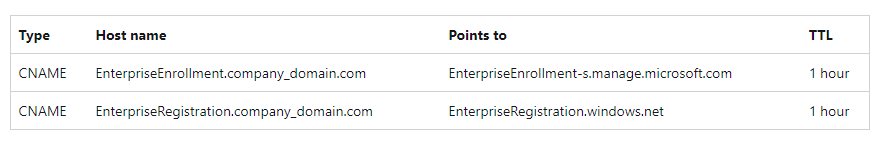
Question 3 : Whizlabs Inc. has a Microsoft 365 E5 subscription that uses an Azure AD tenant named Whizlabs.Inc. Every time a user registers their device in Intune, they have to enter the address of Intune servers. Which of the following two DNS records will solve this issue?
A. A CNAME record for AutoDiscover.whizlabs.inc
B. A CNAME record for EnterpriseEnrollment.whizlabs.inc
C. A SRV record for _SIPfederationTLS.whizlabs.inc
D. A CNAME record for EnterpriseRegistration.whizlabs.inc
Correct Answers: B and D
Explanation:
To simplify enrollment, create a domain name server (DNS) alias (CNAME record type) that redirects enrollment requests to Intune servers. Otherwise, users trying to connect to Intune must enter the Intune server name during enrollment.
Option A is incorrect because this CNAME record is used for auto-configuring outlook.
Option B is correct because this enables automatic enrollment without entering the address of Intune.
Option C is incorrect because this SRV record is used for publishing and will help to “discover” federation
Option D is correct because this enables automatic enrollment without entering the address of Intune.
Reference: https://docs.microsoft.com/en-us/mem/intune/enrollment/windows-enroll#step-1-create-cname-optional
Domain : Manage Microsoft 365 security and threat management
Type: Drag & Drop – Matching
Question 4 : Whizlabs has a Microsoft 365 subscription. You have the devices shown in the following table.
| Operating Systems | Quantity |
| Windows 11 | 50 |
| Windows Server 2008 R2 | 5 |
| Windows Server 2016 | 2 |
| Windows 8.1 | 4 |
You need to onboard the devices to Microsoft Defender for Endpoint. The solution must avoid installing any specific software on the devices whenever possible. Which onboarding method should you use for each operating system? To answer, drag the appropriate methods to the correct operating systems.
| Windows 11 | A. Local Script |
| Windows Server 2008 R2 | B. Intune |
| Windows Server 2016 | C. Microsoft Monitoring Agent (MMA) |
| Windows 8.1 | D. Azure Log Analytics agent |
Correct Answer: B, D, A and C
| Windows 11 | B. Intune |
| Windows Server 2008 R2 | D. Azure Log Analytics agent |
| Windows Server 2016 | A. Local Script |
| Windows 8.1 | C. Microsoft Monitoring Agent (MMA) |
Explanation:
Windows 11 – Since there are 50 devices it is desirable to configure it using Intune.
Windows Server 2008 R2 – For onboarding older operating systems, we need Azure Log Analytics Agent.
Windows Server 2016 – Since there are only two devices, the Local script is most appropriate for this deployment.
Windows 8.1 – Microsoft Monitoring agent is used on devices that are older than Windows 10.
Domain : Implement modern device services
Question 5 : Whizlabs Inc. has a Microsoft 365 E5 subscription. The company has 100 Windows 8.1 devices and 50 Windows 10 Pro devices, and they are joined to Azure Active Directory. You are asked to change the edition of Windows 10 Pro to Enterprise the next time a user logs into their devices. This change should not allow devices to reboot. Which of the following is the best solution suited for the given requirement?
A. An in-place upgrade
B. Windows Update
C. Subscription Activation
D. Provisioning a package
Correct Answer: C
Explanation: Deploying Windows 10 Enterprise or Windows 11 Enterprise in your organization can now be accomplished with no keys and no reboots. Devices with a current Windows 10 Pro license or Windows 11 Pro license can be seamlessly upgraded to Windows 10 Enterprise or Windows 11 Enterprise, respectively.
Option A is incorrect because the option requires a reboot.
Option B is incorrect because the option requires a reboot.
Option C is correct because devices with a current Windows 10 Pro license can be seamlessly upgraded to Windows 10 Enterprise.
Option D is incorrect because this would not help in activating the enterprise license.
Domain : Manage Microsoft 365 governance and compliance
Question 6 : This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals.
(same series – Q.6 to Q.8)
Whizlabs Inc has Microsoft 365 subscription. Company policy does not want users to send email messages that contain Social Security Numbers.
Solution: From the Microsoft Purview center, you create a data loss prevention (DLP) policy. State Yes if correct or No.
A. Yes
B. No
Correct Answer: A
Explanation: You can use either Exchange mail flow rules or Microsoft Purview data loss prevention (DLP) to create a sensitive information type policy with Office 365 Message Encryption.
Domain : Manage Microsoft 365 governance and compliance
Question 7 : This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals.
Whizlabs Inc has Microsoft 365 subscription. Company policy does not want users to send email messages that contain Social Security Numbers.
Solution: From the Azure portal, you create a Microsoft Azure Information Protection label and an Azure Information Protection policy. State Yes if correct or No.
A. Yes
B. No
Correct Answer: B
Explanation: You can use either Exchange mail flow rules or Microsoft Purview data loss prevention (DLP) to create a sensitive information type policy with Office 365 Message Encryption.
Domain : Manage Microsoft 365 governance and compliance
Question 8 : This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals.
Whizlabs Inc has Microsoft 365 subscription. Company policy does not allow users to send email messages that contain Social Security Numbers.
Solution: From the Microsoft Defender for Cloud Apps admin center, you create an access policy. Does this meet the goal?
A. Yes
B. No
Correct Answer: B
Explanation: You can use either Exchange mail flow rules or Microsoft Purview data loss prevention (DLP) to create a sensitive information type policy with Office 365 Message Encryption.
Domain : Implement modern device services
Type: Drag & Drop – Arranging
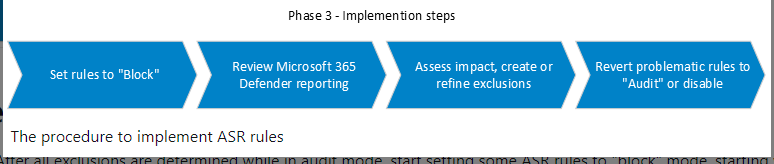
Question 9 : Whizlabs Inc. has 100 Windows 10 devices. The company wants to utilize Windows 10 features to reduce attack surfaces. After going through rigorous auditing of the feature, they are now moving towards the final phase of the implementation plan. What is the correct order of implementation steps for enabling attack surface reduction rules?
- Review Microsoft 365 Defender Reporting
- Set Rules to “Block”
- Assess impact, create, or refine exclusions
- Revert Problematic rules to “Audit” or disable
A. 1, 2, 3, 4
B. 2, 1, 3, 4
C. 3, 2, 1, 4
D. 2, 4, 3, 1
Correct Answer: B
Explanation: Microsoft recommends the below steps to the successful implementation of attack surface reduction for Windows 10 devices:
2. Set Rules to “Block”
1. Review Microsoft 365 Defender Reporting
3. Assess impact, create, or refine exclusions
4. Revert Problematic rules to “Audit” or disable
Option B is correct because this option lists the correct order.
Case Study (Q.10 to Q.12)
Overview
Whizlabs.io is a new startup based in India. The company is in the fintech business with 25 employees. The company is fully online, and all employees work remotely from their homes. The company processes the credit card data of the users and retains the user’s personally identifiable information such as name, age, address, and photos for a limited time.
Existing Environment
- Microsoft Azure Active Directory is used for identity management.
- Three apps are hosted using Microsoft Web Apps.
- Dev.whizlabs.io
- Prod.whizlabs.io
- Support.whizlabs.io
- Two virtual machines for File and Print Services
- Azure Firewall
- Microsoft 365 E3 Subscription
- Three Azure Active Directory (Azure AD) groups
Gr-Support-Team – All support services employees are part of this group
Gr-Management-Team – All managers are part of this group
Gr-Sales-Team – All sales team employees are part of this group
User Devices:
| Operating Systems | Number of Devices |
| Windows 7 | 2 |
| Windows 8.1 | 3 |
| Windows 10 | 5 |
| Windows 11 | 10 |
| MacOS | 5 |
Planned Changes
- Deploy Microsoft 365 voice calling services
- Implement a log collection solution based on Microsoft Services
- Manage, protect, and collect system logs of all user’s devices centrally
Technical Requirements
- Prevent leakage of any user’s credit card information
- Mark any documents or emails which contain credit card information as confidential and restrict its usage to the owner and management team group only.
Security Requirements
- Protect all the user devices against ransomware
- All user’s device drives should be encrypted
- Identify high-risk individuals in the company
- Retain User data for 7 years
Compliance Requirements
- All user’s data should be purged after 30 days of termination of account
- User data of the Gr-Management-Team group should be retained for 90 days after the account is terminated.
Domain : Manage Microsoft 365 governance and compliance
Question 10 : To deploy a phone calling solution, which of the following options is most feasible, cost-effective, and easy to implement?
A. Purchase Microsoft Teams Phone Standard Plan
B. Upgrade your Microsoft 365 E3 plan to E5
C. Microsoft 365 E3 comes with calling solutions
D. Upgrade your Microsoft 365 E3 plan to A5
Correct Answer: B
Explanation:
Microsoft 365 E5 includes a phone system that enables PBX capabilities such as call control in the cloud with Teams. Audio conferencing which conducts or calls in to meetings from your phone allows up to 300 phone attendees.
Microsoft 365 E5 is a premium purchasing option that includes best-in-class productivity apps and advanced security, compliance, and analytical capabilities for your enterprise. Current E1 and E3 customers can upgrade to E5 for a reduced price.
Option A is incorrect because a separate plan needs to be purchased.
Option B is correct because it is most feasible and easy to implement in a given scenario and there is reduced pricing for existing E3 subscribers.
Option C is incorrect because it is incorrect as E3 does not have a calling facility.
Option D is incorrect because plan A5 is for academic organizations.
Reference: https://www.microsoft.com/en-in/microsoft-teams/microsoft-teams-phone#coreui-banner-4zt270o
Domain : Manage Microsoft 365 governance and compliance
Type: Drg & Drop – Aligning
Question 11 : To meet the given compliance requirements, please match the best available option:
A. All user’s data should be purged after 30 days of termination of the account.
B. Emails of the Gr-Management-Team group should be retained for 90 days after the account is terminated.
C. Deletion of user account
D. Create a data loss prevention policy
E. Create a data retention policy
F. Create a service endpoint policies
Correct Answer: A and C
Explanation:
Deletion of user account – When you delete a user, the account becomes inactive for approximately 30 days. You’ve until then to restore the account before it’s permanently deleted.
Create a data retention policy – If a Microsoft 365 retention policy is applied to a mailbox, or one or more email items in a mailbox have a retention label applied, and then the Microsoft 365 user account is deleted, the mailbox will be converted into an inactive mailbox. If the retention settings are configured to retain and then delete content, items will be moved to the Recoverable Items folder when the retention duration expires, and then eventually purged from the inactive mailbox.
Service endpoint policies enable to filter virtual network traffic to specific Azure resources, over service endpoints. This is not suitable for any of the two requirements.
With DLP policies, you can identify, monitor, and automatically protect sensitive information across Office 365. This is not suitable for any of the two requirements.
References: https://docs.microsoft.com/en-us/microsoft-365/admin/add-users/remove-former-employee-step-7?view=o365-worldwide, https://docs.microsoft.com/en-us/microsoft-365/compliance/inactive-mailboxes-in-office-365?view=o365-worldwide#inactive-mailboxes-and-microsoft-365-retention, https://docs.microsoft.com/en-us/security/compass/information-protection-and-storage-capabilities, https://docs.microsoft.com/en-us/azure/virtual-network/virtual-network-service-endpoint-policies-portal
Domain : Manage Microsoft 365 governance and compliance
Type: Drag & Drop – Arranging (keeping 4th option as ‘No order’’)
Question 12 : To meet security requirements, please drag the correct Microsoft solution with respect to the requirements.
| Requirements | Microsoft Solution |
| Protect all the user devices against ransomware | A. Microsoft Azure Identity Protection |
| All user’s devices drive should be encrypted | B. Microsoft Defender for Endpoint |
| Identify high-risk individuals in the company | C. Microsoft Intune |
| Retain User data for 7 years | D. Microsoft Purview |
Correct Answer: B, D, A and C
| Requirements | Microsoft Solution |
| Protect all the user devices against ransomware | B. Microsoft Defender for Endpoint |
| All user’s devices drive should be encrypted | D. Microsoft Purview |
| Identify high-risk individuals in company | A. Microsoft Azure Identity Protection |
| Retain User data for 7 years | C. Microsoft Intune |
Explanation:
Microsoft Defender for Endpoint – Controlled folder access is a useful feature in helping to protect your documents and information from ransomware. In a ransomware attack, your files can get encrypted and held hostage. With controlled folder access in place, a notification appears on the computer where an app attempts to make changes to a file in a protected folder.
Microsoft Intune – Endpoint security Disk encryption profiles focus on only the settings that are relevant for a device’s built-in encryption method, like Filevault or BitLocker. This focus makes it easy for security admins to manage disk encryption settings without having to navigate a host of unrelated settings.
Microsoft Azure Identity Protection – Risk detections in Azure AD Identity Protection include any identified suspicious actions related to user accounts in the directory. Risk detections (both user and sign-in linked) contribute to the overall user risk score that is found in the Risky Users report.
Microsoft Purview – One can leverage the Data Lifecycle Management feature of Microsoft Purview and create retention policy based on requirement. Data lifecycle management provides you with tools and capabilities to retain the content that you need to keep, and delete the content that you don’t.
References: https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/concept-identity-protection-risks, https://docs.microsoft.com/en-us/mem/intune/protect/endpoint-security-disk-encryption-policy, https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/controlled-folders?view=o365-worldwide#why-controlled-folder-access-is-important
Domain : Manage Microsoft 365 governance and compliance
Type: Drag & Drop – Arranging
Question 13 : To achieve technical requirements of preventing leakage of any user’s personally identifiable and credit card information, you need to create a policy in Microsoft Purview. What are the correct steps for achieving it?
A. Data loss prevention
B. Create Policy
C. Policies
D. Choose the information to protect
E. Name your policy
F. Locations to apply the policy
G. Policy Settings
H. Review your settings
I. Test or turn on policy
Correct Answer: A, C, B, D, E, F, G, I and H
A. Data loss prevention
C. Policies
B. Create Policy
D. Choose the information to protect
E. Name your policy
F. Locations to apply the policy
G. Policy Settings
I. Test or turn on policy
H. Review your settings
Explanation:
The easiest, most common way to get started with DLP policies is to use one of the templates included in the Microsoft Purview compliance portal.
You can use one of these templates as is or customize the rules to meet your organization’s specific compliance requirements.
To configure the policy, you can navigate through the Microsoft Purview compliance portal > Solutions > Data loss prevention > Policies > Create Policy > Choose the information to protect > Name your policy > Locations to apply the policy > Policy Settings > Test or turn on the policy > Review your settings.
Option B is correct because it reflects the correct sequence.
Domain : Implement Microsoft 365 security and threat management
Type: Drag & Drop – Aligning
Question 14 : Whizlabs Inc. has Microsoft 365 subscription. The company is utilizing Microsoft 365 Defender for Cloud Apps which provides rich visibility, control over data travel, and sophisticated analytics to identify and combat cyber threats across all your Microsoft and third-party cloud services. Their endpoints are managed using Microsoft defender endpoints. The company wants to integrate Microsoft Defender for Cloud Apps with Microsoft Defender for Endpoint. Which of the following are the prerequisites for this implementation plan? [CHOOSE THREE]
A. Microsoft Defender for Endpoint Plan 2 license
B. Microsoft Azure Sentinel
C. Microsoft Defender Antivirus
D. Windows 10 or above
E. Cloud Access Security Broker (CASB)
Correct Answers: A, C and D
Explanation:
Microsoft Defender for Cloud Apps integrates with Microsoft Defender for Endpoint natively. The integration simplifies roll out of Cloud Discovery, extends Cloud Discovery capabilities beyond your corporate network, and enables device-based investigation, however, there are a few prerequisites for it as below:
- Microsoft Defender for Cloud Apps license
- Microsoft Defender for Endpoint Plan 2 license
- Windows 10 version 1709 (OS Build 16299.1085 with KB4493441), Windows 10 version 1803 (OS Build 17134.704 with KB4493464), Windows 10 version 1809 (OS Build 17763.379 with KB4489899) or later Windows 10 and Windows 11 versions
- Microsoft Defender Antivirus
- Real-time protection enabled
- Cloud-delivered protection enabled
- Network protection enabled and configured to block mode
Option A is correct because for this integration the license for Microsoft Defender for Cloud Apps is required.
Option B is incorrect because Azure Sentinel is a separate security information and event management (SIEM) solution and is not needed for this implementation.
Option C is correct because for this integration the license for Microsoft Defender for Endpoint Plan 2 license is required.
Option D is correct because only devices windows 10 or above are supported.
Option E is incorrect because Microsoft Defender for Cloud Apps itself is a Cloud Access Security Broker (CASB) that supports various deployment modes including log collection, API connectors, and reverse proxy.
Reference: https://docs.microsoft.com/en-us/defender-cloud-apps/mde-integration#prerequisites
Domain : Implement Microsoft 365 security and threat management
Question 15 : Whizlabs Inc. has a Microsoft 365 subscription. The company wants to ensure that all email senders to the organization are verified. Which of the following Microsoft 365 Defender threat policies do you need to configure?
A. Safe Links
B. Anti-phishing
C. Safe Attachments
D. Anti-spam
Correct Answer: B
Explanation:
Phishing is an email attack that tries to steal sensitive information in messages that appear to be from legitimate or trusted senders. In Microsoft 365 Defender you can configure impersonation protection settings for specific message senders and sender domains, mailbox intelligence settings, and adjustable advanced phishing thresholds.
Option A is incorrect because it protects users from opening and sharing malicious links in email messages and Office apps.
Option B is correct because under this policy you can configure impersonation protection settings for specific message senders and sender domains, mailbox intelligence settings, and adjustable advanced phishing thresholds.
Option C is incorrect because it protects organizations from malicious content in email attachments and files in SharePoint, OneDrive, and Teams.
Option D is incorrect because it protects an organization’s email from spam, including what actions to take if spam is detected.
Domain : Implement modern device services
Question 16 : Whizlabs Inc. has a Microsoft 365 tenant. Company is planning to allow users that are members of a group ‘Group_Hr Team’ to enroll their device in mobile device management (MDM). The device type restrictions are configured as shown in the following tables. Which of the following platforms, Group_HrTeam is able to enroll? To answer, select the appropriate options in the answer area.
| Priority | Name | Allowed Devices | Assigned to |
| 1 | Windows | Windows | Sales |
| 2 | iOS | iOS | Group_HrTeam |
| Default | All Users | All Platforms | All Users |
A. Windows
B. iOS
C. All Platform
D. None of them
Correct Answer: B
Explanation:
The allowed device type for Group_HrTeam is iOS, based on the priority set in device type restriction mentioned in the table.
Domain : Implement Microsoft 365 security and threat management
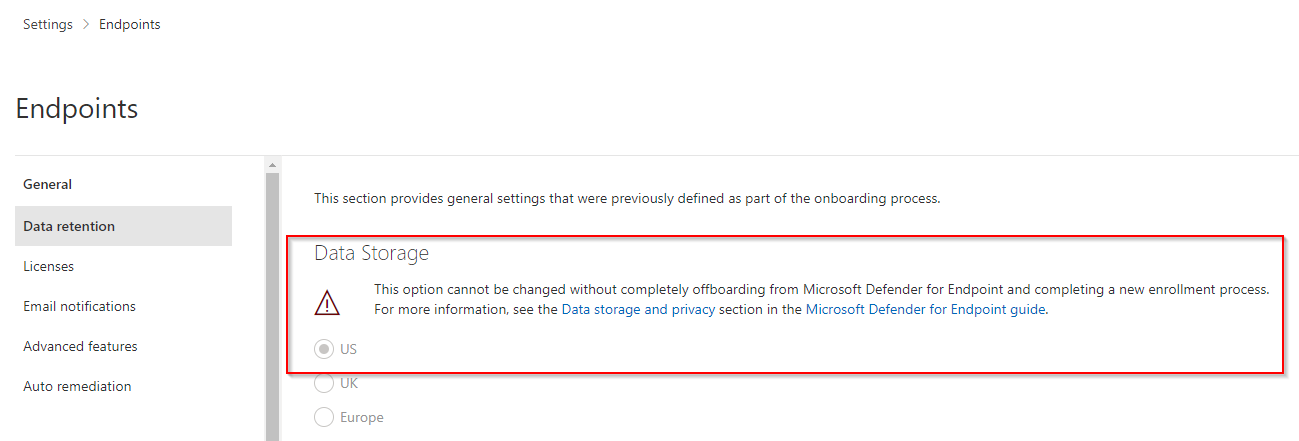
Question 17 : A software development company based in Germany has 1,000 Windows 11 devices. During the initial setup, by default, all log data were kept in the United States. You plan to onboard all the devices to Microsoft Endpoint Defender. To ensure GDPR compliance, you need to ensure data is stored in Europe. What should be the correct order to tackle the situation?
A. Create a workspace.
B. Onboard a new device.
C. Delete the workspace.
D. Offboard the test devices.
Correct Answer: D
Explanation:
Once the devices are onboarded, the storage location cannot be changed. In order to change the location, you first need to offboard the devices.
Option A is incorrect because creating a new workspace wouldn’t allow you to onboard existing devices.
Option B is incorrect because if you are onboarding new devices, they will still be stored in the same location which is currently configured.
Option C is incorrect because you can’t delete workspace until you have offboarded the devices residing in it presently.
Option D is correct because you need to offboard all the devices in the existing workspace to change the location of the data to be stored.
Domain : Manage Microsoft 365 governance and compliance
Question 18 : Whizlabs Inc. has a Microsoft 365 subscription. All users are assigned a Microsoft 365 E3 license. The company has Standard Audit enabled. What is the maximum number of days the audit log data will be retained in Microsoft 365?
A. 30 days
B. 90 days
C. 180 days
D. 365 days
Correct Answer: B
Explanation:
Option B is correct because when an audited activity is performed by a user or admin, an audit record is generated and stored in the audit log for your organization. In Audit (Standard), records are retained for 90 days.
All other options are incorrect.
Domain : Implement modern device services
Question 19 : An Organization has a Microsoft 365 subscription and manages all the devices using Microsoft Endpoint Manager. The company has 50 Windows 11 devices and 50 iOS devices. To meet the following requirements:
- Devices should be able to connect to a secured Wi-Fi network named WhizNet.
- Eight-character password is needed to lock the devices.
What is the minimum number of device configuration profiles you need to create in Microsoft Endpoint Manager?
A. 1
B. 2
C. 3
D. 4
Correct Answer: D
Explanation:
You would require 4 profiles to achieve the requirements.
2 x Wi-Fi configuration profiles (One for iOS. one for Win 10).
2 x Device restrictions for password requirements (One for iOS. one for Win 10).
Option A is incorrect because all requirements cannot be bundled into one policy.
Option B is incorrect because 2 profiles are not sufficient for two different types of devices and their two different requirements.
Option C is incorrect because 3 profiles would not meet all the requirements.
Option D is correct because 4 profiles are required to achieve the requirements.
2 x Wi-Fi configuration profiles (One for iOS. one for Win 10).
and 2 x Device restrictions for password requirements (One for iOS. one for Win 10).
References: https://docs.microsoft.com/en-us/mem/intune/configuration/device-restrictions-ios#password, https://docs.microsoft.com/en-us/mem/intune/configuration/device-restrictions-windows-10#password, https://docs.microsoft.com/en-us/mem/intune/configuration/wi-fi-settings-configure
Domain : Manage Microsoft 365 governance and compliance
Question 20 : An Organization has Microsoft 365 subscription. The compliance officer has requested to investigate user activity in Microsoft 365, including from where users signed in, which applications were used, and increases in activity in the past month. Which of the following Microsoft solution can provide you with the requested information?
A. Microsoft Defender for Identity
B. Microsoft Purview
C. Microsoft Defender for Cloud Apps
D. Flow Checker
Correct Answer: B
Explanation:
Microsoft Purview Communication Compliance is an insider risk solution that helps minimize communication risks by helping you detect, capture, and act on inappropriate messages in your organization. You can generate and review the activities by users and apps used by them.
Option A is incorrect because Microsoft Defender for Identity is a cloud-based security solution that leverages your on-premises Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization.
Option B is correct because Microsoft Purview Communication Compliance is an insider risk solution that helps minimize communication risks by helping you detect, capture, and act on inappropriate messages in your organization.
Option C is incorrect because Microsoft Defender for Cloud Apps is used for protecting your apps.
Option D is incorrect because Flow Checker in Power Automate promotes higher quality flows by ensuring you follow best practices when you design flows. When you run the checker, you get insights into questions like “which areas of my flow’s implementation pose a performance or reliability risk?”.
Domain : Implement Microsoft 365 security and threat management
Question 21 : An Organization has Microsoft 365 E5 tenant containing 50 Windows 10 devices. You need to configure a Windows 10 security baseline to protect the device from memory leakage. What should you configure in the profile?
A. Microsoft Defender Credential Guard
B. Windows Sandbox
C. Windows Defender Application Control
D. Microsoft Defender Exploit Guard
Correct Answer: A
Explanation:
Windows Defender Credential Guard helps protects your systems from credential theft attack techniques (pass-the-hash or pass-the-ticket) as well as helping prevent malware from accessing system secrets even if the process is running with admin privileges.
Option A is correct because Windows Defender Credential Guard helps protects your systems from credential theft attack techniques as well as helping prevent malware from accessing system secrets.
Option B is incorrect because Windows Sandbox provides a lightweight desktop environment to safely run applications in isolation. Software installed inside the Windows Sandbox environment remains “sandboxed” and runs separately from the host machine. A sandbox is temporary. When it’s closed, all the software and files and the state are deleted.
Option C is incorrect because Application control is one of the most effective security controls to prevent unwanted or malicious code from running. It moves away from an application trust model where all code is assumed trustworthy to one where apps must earn trust to run.
Option D is incorrect because exploit protection automatically applies several exploit mitigation techniques to operating system processes and apps. Exploit protection gives organizations detailed reporting into exploit protection events and blocks as part of typical alert investigation scenarios.
Reference: https://docs.microsoft.com/en-us/windows/security/identity
Domain : Implement modern device services
Question 22 : An Organization has a Microsoft Azure Active Directory (Azure AD) tenant named Whiz.inc and a Microsoft 365 subscription. The company has four new users who have the devices shown in the following table.
| Users | Operating Systems |
| WhizU1 | Windows 8.1 |
| WhizU2 | Windows 11 |
| WhizU3 | Android 11 |
| WhizU4 | iOS 15 |
Microsoft 365 subscription is configured to ensure that the new devices enroll in Microsoft Endpoint Manager automatically. Which user’s device can be enrolled in Microsoft Endpoint Manager automatically?
A. WhizU2 only
B. WhizU2 and WhizU3 only
C. WhizU2, WhizU3, and WhizU4 only
D. WhizU1, WhizU2, WhizU3, WhizU4
Correct Answer: A
Explanation:
Only Windows 10 and 11 are eligible for automatic enrollment in Endpoint Manager.
Option A is correct because users with Windows 10 or later are eligible for automatic enrollment in Microsoft Endpoint Manager.
Option B is incorrect because any earlier version than Windows 10 requires manual intervention for registering in Endpoint Manager.
Option C is incorrect because users with Windows 10 or later devices are entitled to automatically enroll their devices.
Option D is incorrect because users with iOS devices cannot automatically enroll their devices.
Reference: https://docs.microsoft.com/en-us/mem/intune/enrollment/windows-enroll
Domain: Implement Microsoft 365 security and threat management
Question 23 : A Company uses Microsoft Defender for Cloud Apps, and has planned to integrate Defender for Cloud Apps and security information and event management (SIEM). What do you need to perform to deploy a SIEM agent on a server running Windows Server 2016? [SELECT TWO]
A. Install Java 8
B. Install Microsoft .Net Framework 3.5
C. Run the Java command and specify the -jar parameter.
D. Run the Set-MMAgent cmdlet
Correct Answers: A and C
Explanation:
To install the agent, you would require a SIEM agent that is written in .jar format. To run .jar file you would require Java. For this particular file, you would require at least Java 8 or above. Extract the .jar file and run the below command to install the agent on the Windows Server 2016.
java -jar mcas-siemagent-0.87.20-signed.jar [–logsDirectory DIRNAME] [–proxy ADDRESS[:PORT]] –token TOKEN
Option A is correct because since the setup file is in a jar format, you would need Java 8 or later.
Option B is incorrect because it would require an application that is based on .exe or .msi format or agent is written in .net code.
Option C is correct because you need the SIEM agent based on jar format. Extract the file and run the command to install the agent.
Option D is incorrect because set-mmagent cmdlet will install Microsoft Monitoring Agent.
Domain : Manage Microsoft 365 governance and compliance
Question 24 : A Company has a Microsoft 365 subscription linked to an Azure Active Directory (Azure AD) tenant named whizlabs.onmicrosoft.com. Johannah (username: jgarratte) stores her documents in Microsoft OneDrive. The legal department wants to place her OneDrive data on an eDiscovery hold. Which URL should be set to use for the eDiscovery hold?
A. https://onedrive.live.com/jgarratte
B. https://whizlabs.onmicrosoft.com/Sites/jgarratte
C. https://whizlabs.sharepoint.com/whizlabs_onmicrosoft_com/jgarratte
D. https://whizlabs-my.sharepoint.com/personal/jgarratte_whizlabs_onmicrosoft_com
Correct Answer: D
Explanation:
When you want to search for a OneDrive, this domain https://contoso-my.sharepoint.com contains all your OneDrive data; so if you want to put a user’s drive on eDiscovery hold, you can use URL for https://contoso-my.sharepoint.com/personal/username_contoso_onmicrosoft.com a user’s OneDrive site.
Option A is incorrect because the link is for a public user account not related to Microsoft 365 service.
Option B is incorrect because the given site does not hold any OneDrive user’s URLs.
Option C is incorrect because the URL does not point to any personal folder of the user.
Option D is correct because the given link stores personal user’s data that can be used to put eDiscovery on hold for the user’s OneDrive Data.
Domain: Implement modern device services
Type: Drag and Drop – Arranging
Question 25 : A Company has a Microsoft 365 E5 tenant that contains 100 Android devices enrolled in Microsoft Intune. The company wants to deploy a Google Play app to the devices using Microsoft Endpoint Manager. The steps are given below, please put the steps in the correct order.
A. Add the app
B. Assign the app
C. Create a Google account
D. Link the account to Intune
Correct Answer: C, D, A and B
C. Create a Google account
D. Link the account to Intune
A. Add the app
B. Assign the app
Explanation:
Before you assign an app to a device or a group of users, you must first add the app to Microsoft Intune. To add an app in Microsoft Intune you must have a google account to link it with Intune.
References: https://docs.microsoft.com/en-us/mem/intune/apps/apps-add#before-you-add-apps, https://docs.microsoft.com/en-us/mem/intune/apps/store-apps-android
Summary
We hope the above list of MS-101 exam questions are helpful for your preparation journey. However the MS-101 exam covers a wide range of topics, including Azure Information Protection, Azure Active Directory, and Microsoft Intune. So, you can expect to see questions on topics such as configuring and managing Azure Information Protection, implementing and managing Azure Active Directory, and configuring and managing Microsoft Intune.
The enterprise administrator serves as the connecting point for all Microsoft 365 workloads. This position coordinates different Microsoft 365 workloads and provides advice to architects and workload administrators.
If you have any doubts on MS-101 exam questions preparation, please feel free to contact us!
- 25 Free Questions on MS-101: Microsoft 365 Mobility and Security - November 13, 2022
- What is Snowpipe & how does it works? - October 7, 2022
- Preparation Guide on DP-420 Designing and Implementing Cloud-Native Applications Using Microsoft Azure Cosmos DB Certification - September 12, 2022
- Preparation guide on MB-910: Microsoft Dynamics 365 Fundamentals (CRM) Certification Exam - August 5, 2022
- Snowflake Certifications – Which snowflake certification is best for you? - July 11, 2022
- All you need to know about Certified Ethical Hacker Certification - June 16, 2022
- What are Hands-On Labs? A beginner’s guide to Hands-on Labs - May 17, 2022
- 25 Free Question on Salesforce Administrator Certification - April 26, 2022