In the past, companies primarily focused on securing a defined “perimeter” based on geographical boundaries. However, with the shift towards a cloud-centric environment, these perimeters have become obsolete and ineffective. As a result, implementing a Zero trust architecture (ZTA) has emerged as the essential strategy for strengthening cybersecurity defenses.
Implementing a Zero Trust Architecture is a crucial step in today’s rapidly evolving cybersecurity landscape. Zero Trust Architecture is a security concept that assumes no user or device can be trusted by default, regardless of its location within the network. It focuses on verifying and validating every access request, minimizing potential attack vectors, and reducing the impact of security breaches.
In the context of SC-100 Exam: Microsoft Cybersecurity Architect, understanding the key steps involved in implementing Zero Trust Architecture is essential. The SC-100 exam tests your knowledge and proficiency in designing and implementing robust security solutions using Microsoft technologies.
In this blog, you will walk through steps to be followed to build zero trust architecture and also brief some of the best practices to be followed to ensure security.
Let’s dig in!
Zero Trust Architecture Principles
Applying the “default deny” security stance to various company assets provides the foundation of five of these principles, including:
Zero Trust Networks: For business cybersecurity or a zero trust security policy, protecting the conventional network perimeter is insufficient. A zero-trust network is typically micro-segmented, with boundaries created around each of the important assets of the firm.
It is easy to conduct security inspections and implement access rules at these boundaries, making it simpler to stop threats from moving laterally across the network and to limit and isolate a potential breach. And thus ensuring perimeter-based security can help to attain the zero-trust networks.
Workloads with Zero Trust: Cybercrime rising at a higher rate and cybercriminals find cloud-based workloads, comprising assets such as containers, functions, and virtual machines, to be appealing targets, and they have particular security requirements. These resources must be protected using tailored, granular zero trust safety surveillance and access management, especially in public clouds.
Zero Trust Data: One of the main goals of a zero trust security strategy is to improve data security. In order to implement zero trust, it is necessary to locate data caches that are sensitive or important, map typical information flows, and provide access rules based on business requirements. The whole IT ecosystem of an organisation, including desktops, smartphones, tablets, application and database servers, and deployments in the cloud, must be uniformly established and adhered to by these standards.
Zero trust people: Data breaches are most often caused by compromised credentials, therefore authentication based on users and passwords is no longer acceptable. Zero trust demands strong authentication employing zero trust network access (ZTNA) and multi-factor authentication (MFA).
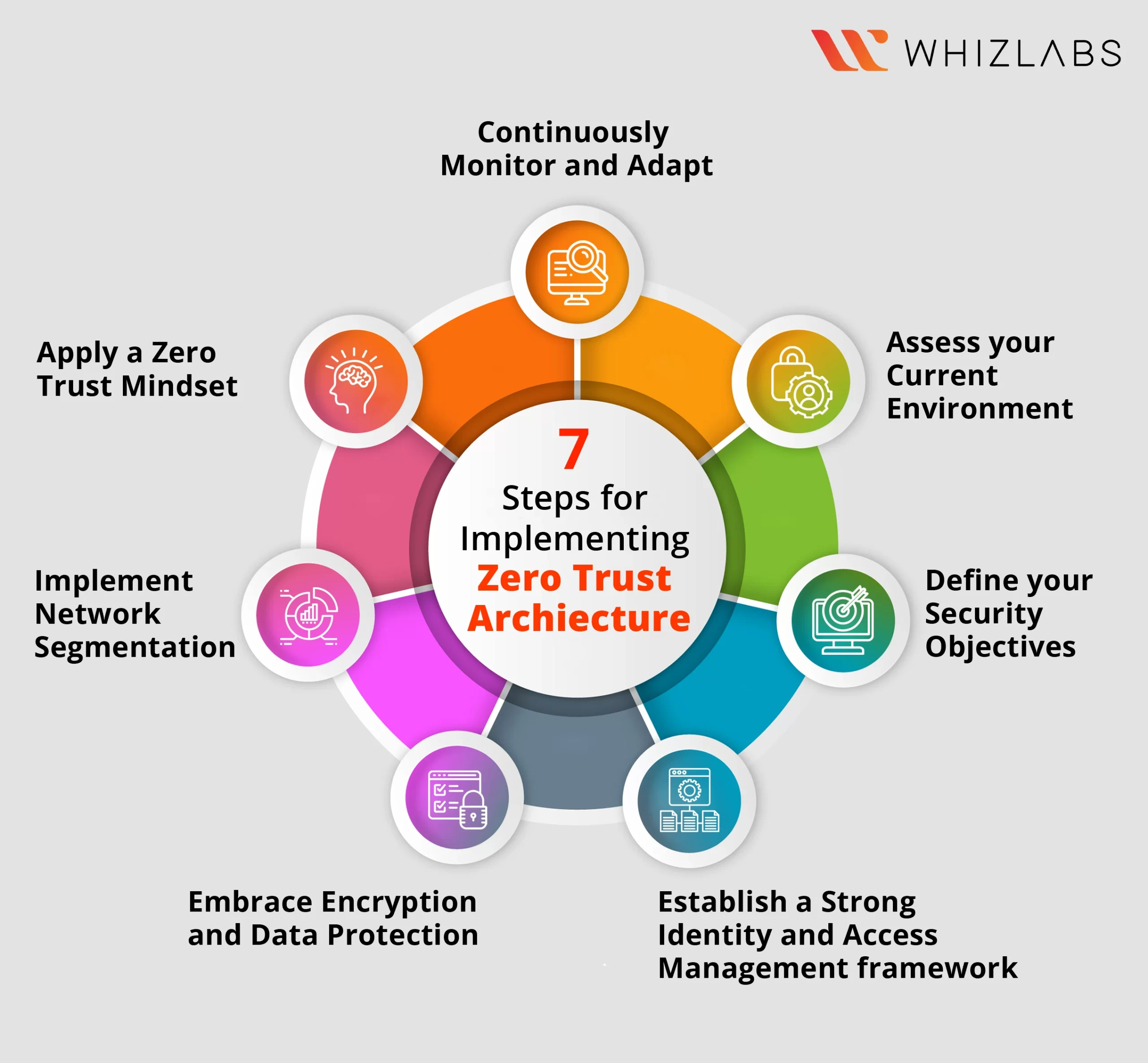
7 steps for implementing zero trust Architecture
To help you prepare for the SC-100 exam, here are seven fundamental steps for implementing Zero Trust Architecture, tailored to the requirements of Exam SC-100 and Microsoft’s cybersecurity ecosystem.
Also Read: Free Question on SC-100 exam: Microsoft Cybersecurity Architect
Step 1. Forming a dedicated zero-trust team
Zero trust is one of the most important initiatives an enterprise can undertake. Instead of placing the “move to zero trust” job at the bottom of everyone’s priority list, assign a small team to oversee the planning and execution of the migration.
The zero trust team can be build from the below listed specialized areas which can paves way to attain zero trust and
- application and data security
- Network and infrastructure security
- User and device security
In particular, having individuals from the security operations center and risk management will be highly valuable.
Step 2. Selection of zero-trust implementation on-ramp
In default, the zero trust security has three major on-ramps with its common technology path. The enterprise can be integrated with zero trust to all the existing on-ramps, beginning with an optimal one on the basis of the current environment and zero trust strategy.
Option 1: User and device identification
Organizations with a sizable population of distant users accessing cloud-based apps may find the user and device identification on-ramp to be the most appealing.
The user and device identity is found as the best option for an organization with a large group of remote users who are involved in accessing the cloud-based solutions.
- Biometrics: The user and device can be verified with the help of this trusted technology known as biometrics. The biometric can serve as an essential part of the authentication process and it can be done on the basis of the unique physical and behavioral characteristics of the user. Adopting biometric technology can make it easier to deploy zero trust-based user identity.
- Multifactor authentication: This is another way to track the user to the device to a certain trust.
- Identity and access management: IAM offers single based credential and single login authentication will be carried out across the various cloud platforms and internal systems.
- Zero-trust network access: In order to restrict access to apps based on user identity, contextual indicators like geolocation and device security posture, and business security policies, ZTNA technology can be coupled with IAM and MFA. The Secure Access Service Edge (SASE) and security service edge systems also provide ZTNA technology as a standalone service.
Option 2: Applications and data
To ensure security of the applications and data, the following practices can be followed:
Data classification: It is the practice of ensuring security level for certain data types, regardless of where the data has been stored such as cloud, data centers and endpoints etc. The data classification offers data underpinning services for the access control to achieve zero trust.
Authentication and authorization of the Microservices: To take effective security initiatives, microservice authentication will be the best solution. In this method, technology such as Keycloak was adopted and it is an advanced level of authentication framework.
Data loss prevention: It refers to a tool for tracking and accessing the data whether it is cloud based or on premises. And it also has certain control points for the deployment of zero trust policies.
Container security: The management and security of container groups can be achieved in an automated way with the help of container security. And it offers some of the services such as orchestration, launching, tracking, shutting down the containers and implementation of the policy across the containers.
Cross-system integration through APIs: It refers to the collaboration of various cybersecurity infrastructure components. It serves as the foundation for many of the advanced security initiatives, specifically zero-trust security.
Organizations that choose applications and data to ensure zero trust security must focus on the deployment of certain initiatives such as data classification, microservices, API integration and usage of some critical technologies such as container security and DLP. The usage of such services can enable security for the applications and data.
Option 3: Network
Enterprises that largely rely on a reputable internal network with networking-based controls and a sizable number of workloads that continue to be handled in an on-premises data center are a suitable fit for the network on-ramp for achieving zero trust. Additionally, it becomes sense to upgrade network-based restrictions to zero trust if the network is the present cybersecurity platform.
Automation: Streamlining network restrictions makes them dynamic, enabling the zero-trust principle of being able to cancel authorization in the middle of a session. By building their own scripts or by choosing management products with incorporated automation, engineers can automate network controls.
Microsegmentation: The core of many modern security measures, like zero trust, is microsegmentation. Instead of port, IP address, and traffic type, the concept relates to the permission of data flows depending on user and resource type.
For instance, a list of permitted users can decide that accounting can only access system X, no matter where it is or what IP address it is using at the moment. The majority of cutting-edge network suppliers are now using microsegmentation.
Centralized firewall management, cloud-based firewalls, and network virtualization: Network virtualization, cloud-based firewalls, and centrally controlled firewalls will facilitate the adoption and administration of zero-trust procedures, while they are not necessarily related to it. Automation of controls is simpler, quicker, and easier when network components are made virtual or cloud-based than when they need to be physically managed.
This in turn facilitates the deployment of zero-trust policies, especially dynamic ones, quicker and simpler. No matter where they are situated or if they are virtual or physical, all of the firewalls in the organisation can be managed and configured by security teams thanks to centralised firewall administration.
Step 3: Evaluating the environment
Implementing a zero-trust strategy will be simpler if you are aware of the controls in your environment.
Checking the security measures: The security controls in a network context include firewalls, internet-based gateways, and similar devices. Endpoint security, including detection and reaction to endpoints or expanded detection and response, and IAM may be the controls in a user/identity environment. These include container safety DLP, microservices authorisation, and comparable controls in an app and information environment.
What degree of dynamic, specific, end-to-end trusted frameworks that are independent of preexisting categories do these restrictions provide? For instance, firewalls often don’t use granular, end-to-end, or dynamic categorisation
Step 4. Review the available technology
The review of existing technology for taking the initiatives of zero trust security will be a significant solution.Assess new technologies to support the zero-trust initiative’s on-ramp either concurrently with or after the evaluation. The capabilities of next-generation networking hardware, including microsegmentation, virtual routing, and stateful session management, can transform these devices into essential elements of a zero-trust architecture. IAM capabilities are rapidly evolving to become more flexible and granular.
Step 5. Launching the key zero-trust initiatives
The outcomes of the technology analysis should be compared to the technologies you require. The comparison helps in the development, prioritization, and implementation of activities like upgrading current network infrastructure to microsegmentation hardware or implementing microservices authentication.
Step 6. Defining operational changes
Zero-trust solutions have the potential to drastically alter security procedures. To stay ahead of automation and avoid security breaches, for instance, comparable manual operations needs to be changed or automated.
Step 7. Deploy, rinse and repeat
Evaluate the value of new technologies as the company implements them using security KPIs. This includes the average time it takes to put incidents under control, which ought to drop sharply the nearer an organisation gets to zero trust.
FAQs
Is the SC 100 exam challenging?
The Microsoft Security Operations Analyst certification exam, also known as the Microsoft SC-100 exam, is rated as having a medium level of difficulty. The purpose of this exam is to evaluate a candidate’s abilities and knowledge in security surveillance, detection of threats, and incident handling in a Microsoft Azure environment.
What are the goals of Zero Trust?
The main objectives of zero trust include fostering a zero trust culture, ensuring the security and defense of DoD information systems, accelerating the adoption of new technologies, and enabling the full implementation of zero trust principles.
What are the pillars of zero trust architecture?
The zero trust architecture approach includes eight (8) pillars such as User, Device, Networking, Infrastructure, Apps, Data, Visibility and Analytics, and Orchestration and Automation.
How to achieve zero trust?
Implementation of Zero Trust can be achieved in 5 Easy Steps
- Set the Attack Surface in detail.
- Put in place restrictions on network traffic.
- Create a network with zero trust.
- Create a policy of zero trust.
- Monitoring the network.
What is the goal of zero trust architecture?
An approach to cybersecurity known as “zero trust” goes beyond the maxim “trust but verify” and views all networks and traffic as potentially dangerous. A zero-trust architecture aids organizations in integrating corporate and industrial infrastructure and workflows with zero-trust principles.
Summary
Hope this blog envelops detailed steps on how to deploy zero trust architecture. By implementing the above steps, you can establish a robust Zero Trust Architecture that helps to minimize the risk of unauthorized access, lateral movement, and data breaches within your organization. It demonstrates your ability to design and implement secure solutions using Microsoft technologies, a crucial skill for the Microsoft Cybersecurity Architect role.
Prepare thoroughly for the SC-100 Exam by understanding the concepts, technologies, and best practices associated with Zero Trust Architecture in Microsoft’s cybersecurity ecosystem. You can utilize some of the preparation materials like practice tests, hands on labs and sandboxes to achieve better understanding of SC-100 exam concepts.
If you have any questions about this blog, please feel free to contact us!
- Study Guide DP-600 : Implementing Analytics Solutions Using Microsoft Fabric Certification Exam - June 14, 2024
- Top 15 Azure Data Factory Interview Questions & Answers - June 5, 2024
- Top Data Science Interview Questions and Answers (2024) - May 30, 2024
- What is a Kubernetes Cluster? - May 22, 2024
- What are the Roles and Responsibilities of an AWS Sysops Administrator? - March 28, 2024
- How to Create Azure Network Security Groups? - March 15, 2024
- What is the difference between Cloud Dataproc and Cloud Dataflow? - March 13, 2024
- What are the benefits of having an AWS SysOps Administrator certification? - March 1, 2024