In today’s rapidly advancing digital landscape, cybersecurity has emerged as a paramount concern for organizations worldwide.
The prevalence of cyber threats and attacks has underscored the need for robust and resilient cybersecurity measures to protect sensitive data, critical systems, and valuable assets.
In this dynamic environment, Microsoft Cybersecurity Reference Architectures (MCRA) plays a pivotal role in fortifying cybersecurity strategies. Designed as a comprehensive guide, MCRA equips organizations with invaluable insights and recommendations, empowering them to build a secure and well-protected digital infrastructure.
Let’s delve deeper into how MCRA serves as a guiding light in the realm of Microsoft Cybersecurity.
What are Microsoft Cybersecurity Reference Architectures?
Microsoft Cybersecurity Reference Architectures, the name itself implies that it is used for reference purposes and it has the set of documents and resources offered by Microsoft. It outlines some of the approaches while designing and deploying secured systems.
The MCRA serves as a definitive guide, presenting tailored strategies to fortify diverse system types, be it cloud-based, on-premises, or hybrid. This comprehensive resource addresses a wide array of crucial topics, including identity and access management, secure systems, network security, and incident response, providing unparalleled insights into safeguarding your digital infrastructure.
It helps the organization of all sizes while designing cybersecurity architecture. Positioned as a reference rather than a rigid roadmap, it encourages organizations to personalize and modify the recommendations to suit their particular environments and requirements effectively.
Flexibility and adaptability lie at the core of this resource, empowering businesses to enhance their cybersecurity measures with individuality.
What are the diagrams included in Microsoft Cybersecurity Reference Architectures?
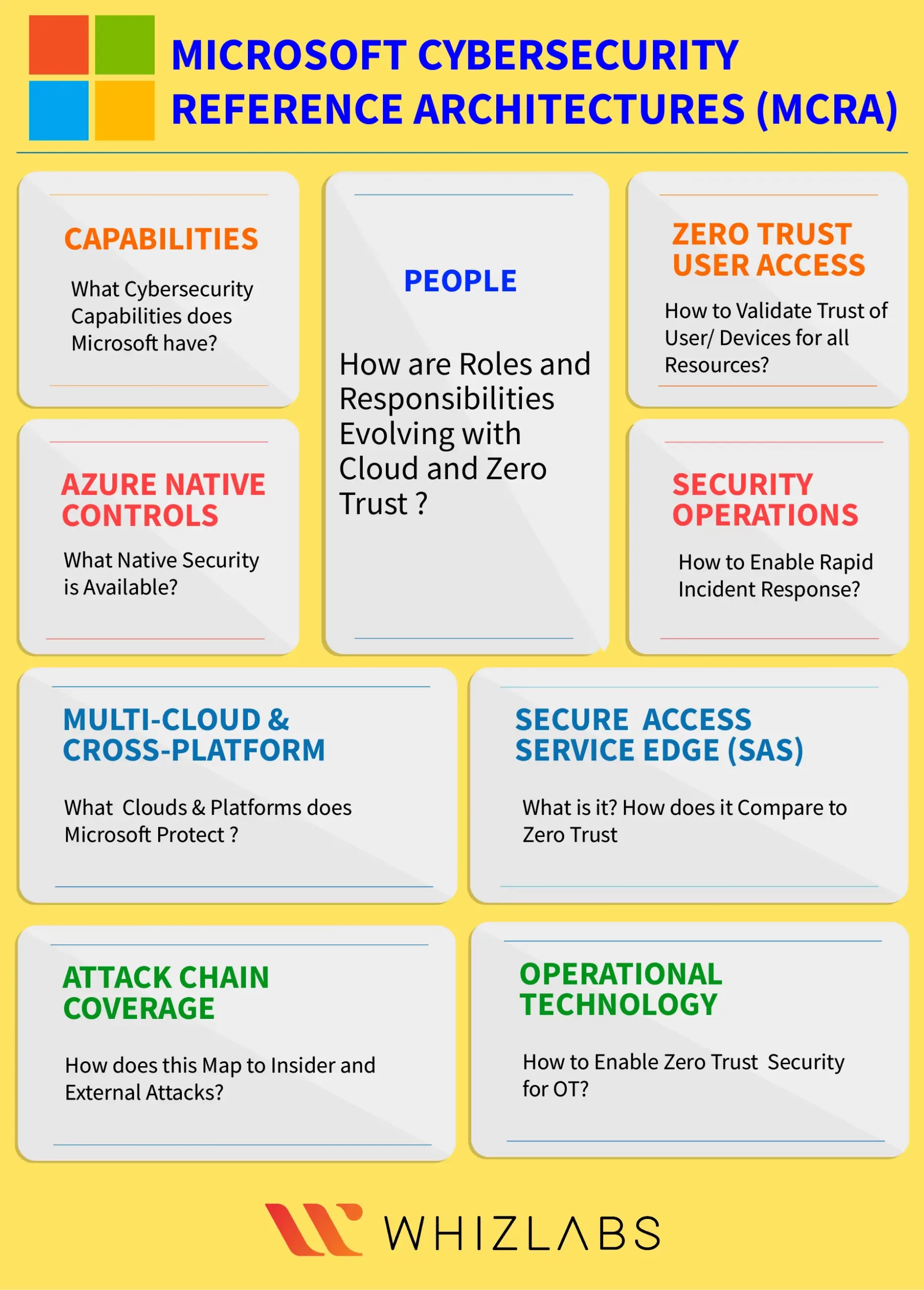
The Microsoft Cybersecurity Reference Architectures (MCRA) consist of technical diagrams that illustrate Microsoft’s cybersecurity capabilities and how they integrate with various platforms.
These platforms include Microsoft’s offerings such as Microsoft 365 and Microsoft Azure, third-party apps like ServiceNow and Salesforce, and third-party platforms like Amazon Web Services (AWS) and Google Cloud Platform (GCP).
The MCRA comprises diagrams covering essential cybersecurity topics, such as:
- Microsoft cybersecurity capabilities
- Zero Trust architecture and a Zero Trust rapid modernization plan (RaMP)
- Zero trust user access
- Security operations
- Operational technology (OT)
- Multicloud and cross-platform capabilities
- Attack chain coverage
- Azure native security controls
- Security organizational functions
Also Read : Preparation Guide on SC-100:Microsoft Cybersecurity Architect
Key features of Microsoft Cybersecurity Reference Architecture
Before getting into the technical aspects, you have to understand what are the capabilities of Microsoft Cybersecurity Reference Architecture.
Incident response
This capability encompasses suggestions for setting up incident response plans, assembling incident response teams, and adopting appropriate incident response tools.
Governance, risk, and compliance
The Microsoft Cybersecurity Reference Architectures (MCRA) provides a comprehensive approach to bolstering cybersecurity through various capabilities. These include identity and access management, data protection, network security, incident response, governance, risk, and compliance, as well as security operations.
Zero Trust User Access
The MCRA also promotes the adoption of the Zero Trust User Access model, wherein all users are treated as potential threats and must be authenticated and authorized before accessing resources. To support this model, multi-factor authentication, access control, identity federation, and device management are recommended.
Microsoft Cybersecurity Reference Architectures (MCRA) recommends various capabilities to strengthen access security:
- Multi-factor authentication: Users must provide multiple authentication factors (e.g., password and security token) to verify their identity before accessing resources.
- Access control: Policies and controls are implemented to authorize specific users’ access to designated systems and resources under defined conditions.
- Identity federation: Integration of diverse identity systems enables users to access resources using a unified set of credentials.
- Device management: Policies ensure that only trusted devices complying with security standards can access systems and resources.
Customizable and Adaptable
MCRA is designed to be customizable and adaptable, allowing organizations to tailor the recommendations to their specific needs and environments. Whether an organization has an on-premise, cloud-based, or hybrid infrastructure, MCRA provides valuable insights to bolster cybersecurity measures effectively.
Security Roles and Responsibilities
In the realm of Security Roles and Responsibilities, the MCRA underscores the significance of clearly defining and assigning tasks related to cybersecurity. By establishing roles like security architects, engineers, analysts, and administrators, organizations can ensure the effective execution of cybersecurity tasks.
Moreover, fostering collaboration and communication between different teams and departments within the organization strengthens the overall security posture.
How Microsoft Cybersecurity Reference Architecture is utilized?
These diagrams serve multiple purposes and are valuable in various scenarios:
- Starting Template for Security Architecture: Organizations often use these diagrams as a foundational blueprint to define their desired cybersecurity capabilities. The comprehensive coverage of modern enterprise environments, spanning on-premise, mobile devices, multiple clouds, and IoT/Operational Technology, makes this architecture a valuable resource for designing the target state of security measures.
- Comparison Reference for Security Capabilities: Some organizations leverage these diagrams to assess their current security landscape by comparing it against Microsoft’s recommendations. They discover that they may already possess several of the suggested technologies, providing insights into their existing security posture.
- Learning about Microsoft Capabilities: These diagrams also serve as a valuable learning tool. In presentation mode, each capability includes a “ScreenTip” with a concise description and links to documentation, facilitating a deeper understanding of Microsoft’s security offerings.
- Understanding Microsoft’s Integration Investments: Architects and technical teams can utilize this architecture to identify integration points within Microsoft’s capabilities and leverage them in conjunction with existing security measures. This enables a more seamless and effective security strategy.
- Learning About Cybersecurity: Particularly beneficial for newcomers to cybersecurity, these diagrams act as a comprehensive learning resource, aiding individuals as they embark on their first career or transition into the cybersecurity field.
How cybersecurity architect uses Microsoft Cybersecurity Reference Architecture?
Microsoft Cybersecurity Architects use Microsoft Cybersecurity Reference Architectures (MCRA) as a blueprint to design tailored and robust security solutions. They compare current capabilities, integrate Microsoft technologies, and embrace the Zero Trust model.
Microsoft Cybersecurity Reference Architectures (MCRA) guides incident response planning, ensures compliance, and enhances cybersecurity awareness. It supports decision-making and empowers architects to navigate evolving threats effectively.
Know More : 25 Free Question on SC-100: Microsoft Cybersecurity Architect
Security Best Practices in Microsoft Cybersecurity Reference Architectures for Reducing Attack Risk
Here are some common security best practices used in the Microsoft Cybersecurity Reference Architectures for minimizing the attacks:
- Continuous Improvement for Complete Coverage: Focus on continuously improving the coverage of the attack chain, identifying areas with no visibility and highly vulnerable sections lacking preventive controls.
- Balanced Control Investments: Ensure a balanced investment in security controls across the entire lifecycle, including identify, protect, detect, respond, and recover stages.
- Transition to “XDR + SIEM” from SIEM-only: Incorporate extended detection and response (XDR) tools alongside Security Information and Event Management (SIEM) capabilities for more effective detection and response, with reduced false positives.
- Utilize SOAR Automation and Modern Analytics: Integrate security orchestration, automation, and response (SOAR), Machine Learning (ML), and User Entity Behavioral Analytics (UEBA) technologies to reduce manual efforts and enhance threat detection.
- Adapt Processes to Operational Technology (OT): Adjust tools and processes to accommodate the constraints of OT environments, emphasizing passive network detections and system isolation.
- Develop Insider Risk Controls: Address insider risk separately from external attacks, focusing on mitigating leaks, confidentiality violations, IP theft, fraud, insider trading, and compliance breaches.
FAQs
What is security architecture design in cyber security?
Security architecture design in cybersecurity involves implementing information security controls and measures within IT systems to safeguard the confidentiality, integrity, and availability of data. It focuses on developing a structured and integrated approach to protect sensitive information from potential threats and attacks.
What is meant by NIST reference architecture?
The NIST cloud computing reference architecture concentrates on the functionalities and requirements of cloud services, providing a framework for understanding the operational aspects of cloud computing. It does not offer specific design solutions but serves as a guide to comprehending the complexities involved in cloud computing.
What are the benefits of using Microsoft Cybersecurity Reference Architectures?
A reference architecture has recommended structures and IT products and services integrations to create a security solution. It includes industry best practices to deliver optimal security methods for defined technologies.
What is another name for cyber security architecture?
Cybersecurity architecture, also known as network security architecture, is fundamental in designing computer systems to ensure the security of underlying data. It plays a crucial role in an organization’s defense against security threats.
What does Microsoft do for CyberSecurity?
Microsoft Services offers a comprehensive range of security, identity, and cybersecurity solutions. These services encompass strategic planning, implementation, and ongoing support to address the diverse security needs of organizations effectively.
Conclusion
Hope this Microsoft Cybersecurity Reference Architectures article covers everything you need to know about the Microsoft Cybersecurity Reference Architectures.
By aligning with Microsoft’s cybersecurity capabilities and integrating with diverse platforms, MCRA provides organizations with the necessary guidance to strengthen their cybersecurity defenses and combat modern cyber threats with confidence.
Through customization and adaptability, MCRA ensures that organizations can chart a secure and resilient cybersecurity course tailored to their specific needs and environments, safeguarding their digital assets and future-proofing their cybersecurity strategies. You can also try Sandbox & Hands-on Labs on the Whizlabs Platform.
If you have any questions about this Microsoft Cybersecurity Reference Architectures blog post, please feel free to comment to us!
- Which AWS Certification is Best For Developers - December 5, 2023
- Top Popular Hands on Labs for Google Cloud Platform (GCP) - October 29, 2023
- 7 Exam Tips for Google Cloud Database Engineer Certification - September 21, 2023
- What Is Azure Web Application Firewall (WAF)? - September 8, 2023
- The 5 Best Team Chat Apps for Business in 2024 - August 10, 2023
- What is Microsoft Cybersecurity Reference Architectures? - July 31, 2023
- How to Secure & Migrate your SAP Environment on AWS - July 26, 2023
- A Comparison of SUM-DMO and SWPM - July 21, 2023