Did you come here looking for free Certified Ethical Hacker Certification questions and answers? You have come to the right place. Certified Ethical Hackers and professionals make use of techniques, methodologies, and commercial-grade hacking tools to legally hack an organization’s network. Find these free Ethical Hacker certification practice questions below and test your skills.
Let’s start learning!
Pre-requisites for Certified Ethical Hacker Certification
Although formal educational prerequisites are not mandatory for CEH certification, individuals who achieve certification usually possess a robust foundation in areas such as computer programming, computer science, software engineering, mathematics, and/or information security.
Job titles for Certified Ethical Hacker Certification
Individuals who obtain the Certified Ethical Hacker (CEH) certification can be eligible for various job titles within the field of information security and ethical hacking. Some common job titles associated with CEH certification include:
- Ethical Hacker
- Security Analyst
- Penetration Tester
- Vulnerability Analyst
- Security Consultant
- Cybersecurity Specialist
- Information Security Analyst
- Incident Response Analyst
- Network Security Engineer
- Security Auditor
Domain: Information Security Threats and Attack Vectors
Q1: The attacker copies the target’s password file and then tries to crack passwords in his system at a different location. What type of password attack that performed?
A. Active Online Attack
B. Passive Online Attack
C. Non-Electronic Attack
D. Offline Attack
Correct Answer: D
Explanation
Option A: not correct The attacker performs password cracking by directly communicating with the victim’s machine
Option B: not correct The attacker performs password cracking without communicating with the authorizing party
Option C: not correct The attacker does not need technical knowledge to crack a password, known as a non-technical attack
Option D: correct The attacker copies the target’s password file and then tries to crack passwords in his system at a different location
Reference: CEHv10, Ethical Hacking and Countermeasure EC-Council (Module 06 System Hacking)
Domain: Information Security Assessment Process
Q2: The company implements a security policy that has no restriction on the usage of system resources. What type of security policy did the company perform?
A. Promiscuous policy
B. Permissive policy
C. Prudent policy
D. Paranoid policy
Correct Answer: A
Explanation
Option A: correct The promiscuous Policy has no restriction on the usage of system resources.
Option B: not correct The permissive Policy restricts only widely known, dangerous attacks or behavior.
Option C: not correct The prudent Policy ensures the maximum and strongest security among them. However, it allows known, necessary risks, blocking all other services but individually enabled services.
Option D: not correct Paranoid Policy denied everything, limiting internet usage.
Reference: CEHv10, Ethical Hacking and Countermeasure EC-Council (Module 01 Introduction Ethical hacking)
Domain: Information Security Threats and Attack Vectors
Q3: It is a kind of malware (malicious software) that gets activated upon users’ certain predefined actions. When activated, it can grant attackers unrestricted access or control of all data stored on compromised information systems and can cause potentially immense damage. Which of the following terms best matches the definition?
A. Virus
B. Trojan
C. Ransomware
D. Worm
Correct Answer: B
Explanation
Option A: not correct A computer virus is a self-replicating program that produces its code by attaching copies of itself to other executable codes and operates without the knowledge or desire of the user. This infection of viruses can lead to data loss, system crash, and file corruption.
Option B: correct Trojan is a program in which the malicious or harmful code is contained inside apparently harmless programming or data in such a way that it can get control and cause damage, such as ruining the file allocation table on your hard disk.
Option C : not correct Ransomware is a type of malware that restricts access to the infected computer system or critical files and documents stored on it, and after that, demands an online ransom payment to the malware creator(s) to remove user restrictions. Ransomware might encrypt files stored on the system’s hard disk, or merely lock the system and display messages meant to trick the user into paying.
Option D : not correct Computer worms are standalone malicious programs that replicate, execute, and spread across network connections independently, without human intervention. Intruders design most worms to replicate and spread across a network, thus consuming available computing resources and, in turn, causing network servers, web servers, and individual computer systems to become overloaded and stop responding.
Reference: CEHv10, Ethical Hacking and Countermeasure EC-Council (Module 07 Malware Threat)
Domain : Information Security Technologies
Q4 : Server Administrator configures access settings for users to authenticate first before accessing web pages. Which requirement of information security is addressed by implementing the configuration?
A. Integrity
B. Availability
C. Confidentiality
D. Scalability
Correct Answer: C
Explanation
Option A : not correct Data integrity ensures that only authorized parties can modify data.
Option B : not correct Availability applies to systems and data. ensures that network services and the data are accessible and performing well under all condition
Option C : correct Confidentiality means that only authorized persons can work with and see our infrastructure’s digital resources
Option D : not correct Scalability is the property of a system to handle a growing amount of work by adding resources to the system
Reference: CEHv10, Ethical Hacking and Countermeasure EC-Council (Module 01 Introduction to Ethical Hacking)
Domain : Network and Communication Technologies
Q5 : An organization allows employees to work from the outside network to access the data for a specific purpose. Which technology should be implemented to ensure data confidentiality as data is transmitted?
A. Telnet
B. VLAN
C. WPA2
D. VPN
Correct Answer: D
Explanation
Option A : not correct Telnet is an application protocol used on the Internet or local area network to provide a bidirectional interactive text-oriented communication facility using a virtual terminal connection
Option B : not correct A virtual LAN (VLAN) is any broadcast domain that is partitioned and isolated in a computer network at the data link layer
Option C : not correct WPA2 is encryption method for wireless network
Option D : correct A virtual private network (VPN) extends a private network across a public network and enables users to send and receive data across shared or public networks with secure access to the private network
Reference: https://en.wikipedia.org/wiki/Virtual_private_network
Domain : Information Security Assessment Process
Q6 : Attackers use image files to hide some information for malicious purposes. What type of technique did the attacker perform?
A. Spyware
B. Cryptography
C. Steganography
D. Backdoor
Correct Answer: C
Explanation
Option A : not correct Spyware is stealthy computer monitoring software that allows you to record all the user activities on the target computer secretly
Option B : not correct Cryptography is the practice of concealing information by converting plain text (readable format) into ciphertext (unreadable format) using a key or encryption scheme.
Option C : correct Steganography refers to the art of hiding data ” behind ” other data without the target’s knowledge. Steganography hides the existence of the message. It replaces bits of unused data into the usual files such as graphic, sound, text, audio and video with some other surreptitious bits
Option D : not correct A backdoor is a program which can bypass the standard system authentication or conventional system mechanism like IDS, firewalls, etc . without being detected. In these types of breaches, hackers leverage backdoor programs to access the victim’s computer or a network.
Reference: CEHv10, Ethical Hacking and Countermeasure EC-Council (Module 06 System Hacking)
Domain : Information Security Controls
Q7 : Which Intrusion Detection System is the best applicable to analyze the system’s behavior for Desktop PC or Server?
A. HIDS
B. NIDS
C. Firewall
D. Antivirus
Correct Answer: A
Explanation
Option A : correct HIDS (Host-based Intrusion Detection System) analyze each system’s behavior and applicable on Desktop PC or Server
Option B : not correct NIDS (Network-based Intrusion Detection System) check every packet entering the network. It is used in a large environment to inspect all traffic.
Option C : not correct Firewall is not an IDS
Option D : not correct Antivirus is not an IDS
Reference: CEHv10, Ethical Hacking and Countermeasure EC-Council (Module 12 IDS, Firewall Honeypot)
Domain : Information Security Controls
Q8 : What is the purpose of a demilitarized zone on a network?
A. Protecting the network devices
B. Provide detection for malicious traffic on the network
C. Provide security on servers
D. Providing security to the internal network and only provide direct access to DMZ nodes
Correct Answer: D
Explanation
Option A : not correct For protecting network devices using the firewall.
Option B : not correct It is the purpose of using the Intrusion Detection System (IDS).
Option C : not correct Firewall and IDS will provide security for servers.
Option D : correct DMZ is a small network placed as a neutral zone between the internal (trusted) network and external (untrusted) network to prevent an outsider from accessing the internal network directly.
Reference: CEHv10, Ethical Hacking and Countermeasure EC-Council (Module 12 IDS, Firewall Honeypot)
Domain : Information Security Controls
Q9 : Which of the following types of firewall inspects specific traffic such as http:get or post?
A. Packet filtering firewall
B. Application-level firewall
C. Circuit-level gateway firewall
D. Stateful Multilayer Inspection
Correct Answer: B
Explanation
Option A : not correct Packet Filtering firewall work at the network layer of the OSI model, each packet compared to a set of criteria before it is forwarded
Option B : correct Application-level firewall (proxies) is filter packets at the application layer of the OSI model. This firewall inspect specific traffic on application such as http:get or post
Option C : not correct Circuit level gateway firewall is work at the session layer of the OSI model
Option D : not correct Combine aspect of the other type of firewalls packet filtering, application-level firewall, and circuit-level gateway firewall
Reference: CEHv10, Ethical Hacking and Countermeasure EC-Council (Module 12 IDS, Firewall Honeypot)
Domain : Information Security Attack Detection
Q10 : The system administrator uses virus detection to prevent viruses on the system. He uses a tool for monitoring system operation requests that are written to disk. What is the virus detection method that the system administrator performs?
A. Scanning
B. Interception
C. Code Emulation
D. Integrity Checking
Correct Answer: B
Explanation
Option A : not correct Use anti-virus to perform and detect viruses
Option B : correct The interceptors monitors system operation requests that are written to disk
Option C : not correct Use Virtual Machine to simulate CPU and memory activity
Option D : not correct Reading entire disk and recorded integrity data that acts as a signature for the files and systems sector
Reference: CEHv10, Ethical Hacking and Countermeasure EC-Council (Module 07 Malware Threats)
Domain : Information Security Tools
Q11 : Hyena is a tool to manages and secures Windows operating systems and uses a Windows Explorer-style interface for all operations. It shows shares and user login names for Windows servers and domain controllers. What is the purpose of using this tool?
A. NETBIOS Enumeration
B. LDAP Enumeration
C. SNMP Enumeration
D. SMTP Enumeration
Correct Answer: A
Explanation
Option A: correct Hyena is tool for NETBIOS Enumeration
Option B: not correct Hyena is not LDAP Enumeration tool
Option C: not correct Hyena is not SNMP Enumeration tool
Option D: not correct Hyena is not SMTP Enumeration tool
Reference: CEHv10, Ethical Hacking and Countermeasure EC-Council ( Module 04 Enumeration)
Domain : Information Security Technologies
Q12 : Hashing is generating a value or values from a string of text using a mathematical function. Which of the following is assured by the use of a hash?
A. Confidentiality
B. Integrity
C. Availability
D. Authentication
Correct Answer: B
Explanation
Option A: not correct Confidentiality means the only authorized person can access and read the data.
Option B: correct The main role of a cryptographic hash function is to provide integrity in document management. Integrity ensures an only authorized person can modify the data.
Option C: not correct Availability applies to system and data. Authorized persons can access data via network and minimalize the failure of the network.
Option D: not correct Authentication is processed to identifies users or devices to access some resources.
Reference: CEHv10, Ethical Hacking and Countermeasure EC-Council ( Module 01 Introduction Ethical Hacking)
Domain : Information Security Systems
Q13 : Domain Name System (DNS) has a few types of records. One type of them is AAAA Record. What is the purpose of the AAAA Record ?
A. IPv4 address resolution record
B. IPv6 address resolution record
C. Mail exchange record
D. Text record
Correct Answer: B
Explanation
Option A: not correct Record for IPv4 address is A Record.
Option B: correct AAA is used for Returns, a 128-bit IPv6 address, most commonly used to map hostnames to the host’s IP address.
Option C: not correct Mail exchanger record for DNS is MX
Option D: not correct Text record for DNS is TX.
Reference: https://en.wikipedia.org/wiki/List_of_DNS_record_types
Domain : Information Security Assessment and Analysis
Q14 : CVSS is a published standard that provides an open framework for communicating the characteristics and impacts of IT vulnerabilities. CVSS assessment consists of three metrics for measuring vulnerabilities. Which of the following is the best definition of base metric?
A. Represents the inherent qualities of a vulnerability
B. Represents the vulnerabilities that are based on a particular environment or implementation
C. Represents the features that keep on changing during the lifetime of vulnerability
D. Represent the type of vulnerability
Correct Answer: A
Explanation
Option A : correct Base metric represents the inherent qualities of a vulnerability
Option B : not correct Environmental metric represents the vulnerabilities that are based on a particular environment or implementation
Option C : not correct Temporal metric represents the features that keep on changing during the lifetime of a vulnerability
Option D : not correct Not represent any metric
Reference: CEHv10, Ethical Hacking and Countermeasure EC-Council (Module 05 Vulnerability Analysis)
Domain : Information Security Technologies
Q15 : Which type of hacker performs an attack on the system by using tools and knowledge found on the internet?
A. White Hat
B. Grey Hat
C. Black Hat
D. Script Kiddies
Correct Answer: D
Explanation
Option A : not correct Security analyst or individuals with hacking skill using them for defensive purpose
Option B : not correct Work for defensive and offensive purpose
Option C : not correct Hacker with malicious and destructive activities
Option D : correct Unskilled hackers, hacking and compromising system using tools are the scripts made by real hackers
Reference: CEHv10, Ethical Hacking and Countermeasure EC-Council (Module 01 Introduction to Ethical Hacking)
Domain : Information Security Controls
Q16 : Which of the following OSI layers is the packet filtering firewall work on?
A. Application
B. Application, Presentation, Session
C. Physical, Data Link
D. Data Link, Network, Transport
Correct Answer: D
Explanation
Option D : correct Please see the table below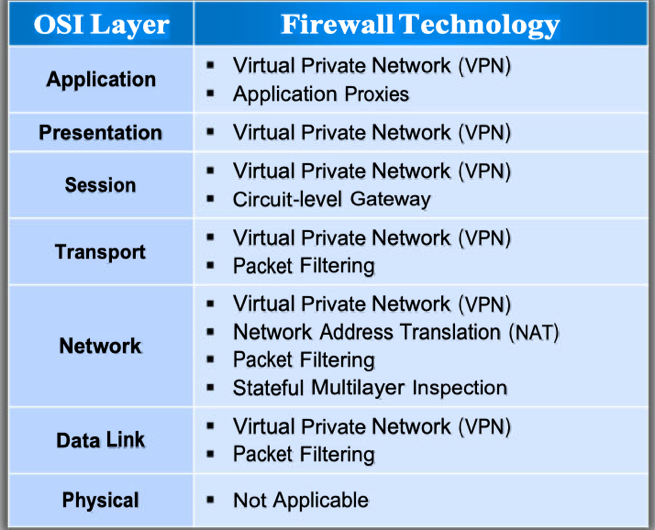
Reference: CEHv10, Ethical Hacking and Countermeasure EC-Council (Module 12 Evading IDS, Firewall and Honeypots)
Domain: Information Security Threats and Attack Vectors
Q17: The enormous usage of mobile devices has grabbed the attention of attackers. Mobile devices access many of the resources that traditional computers use. Apart from that, mobile devices also have some unique features that add new attack vectors and protocols to the mix. Which of the following are mobile attack vectors?
A. Malware
B. Data Exfiltration
C. Data Tampering
D. Data Breaking
Correct Answers: A, B, and C
Explanation
Options A, B & C: correct Mobile attack vectors shown the picture below: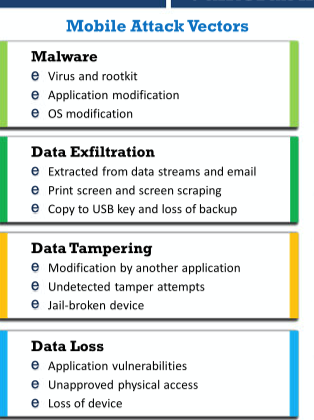
Reference: CEHv10, Ethical Hacking and Countermeasure EC-Council ( Module 17 Hacking Mobile Platform )
Domain: Network and Communication Technologies
Q18: Which of the following protocol used to ensure security in transferring files across the network?
A. SSL
B. HTTP
C. TLS
D. SFTP
Correct Answer: D
Explanation
Option A: not correct SSL is a protocol used to provide a secure authentication mechanism between two communicating applications
Option B: not correct HTTP is an application protocol that used to access the web application
Option C: not correct TLS is more secure than SSL. Transport Layer Security (TLS) is a protocol used to establish a secure connection between a client and a server and ensure the privacy and integrity of information during transmission
Option D: correct SFTP is the protocol to ensure security in file transfer across the network
Reference: https://en.wikipedia.org/wiki/SSH_File_Transfer_Protocol
Domain: Information Security Attack Detection
Q19: How to detect a honeypot that running on VMWare?
A. analyzing outgoing packets
B. Looking for MAC Address range on IEEE standard
C. Looking for specific TCP/IP parameters such as TTL, RTT, and, TCP timestamp
D. using time-based TCP fingerprinting method
Correct Answer: B
Explanation
Option A: not correct It is used to detect snort firewall.
Option B: correct It is used to detect honeypots running on VMware
Option C: not correct It is used to detect honeypots using Linux Virtual Machine
Option D: not correct An attacker can identify the presence of Honeyd honeypot by performing time-based TCP Fingerprinting
Reference: CEHv10, Ethical Hacking and Countermeasure EC-Council (Module 12 Evading IDS, Firewall and Honeypots)
Domain: Information Security Systems
Q20: XYZ company uses 10.20.29.0/27 for the local network. Which of the following subnet mask in this network?
A. 255.255.255.0
B. 255.255.255.252
C. 255.255.255.248
D. 255.255.255.224
Correct Answer: D
Explanation
Option A: not correct It is a subnet mask for the/24 prefix
Option B: not correct It is a subnet mask for /30 prefix
Option C: not correct It is a subnet mask for the/29 prefix
Option D: correct It is a subnet mask for /27 prefix
Reference: https://en.wikipedia.org/wiki/Subnetwork
Domain: Information Security Programs
Q21: In the Linux system, you want to view firewall logs to evaluate network traffic. It would be best if you searched the specific logs with fast and efficient. Which command-line utility are you most likely to use?
A. Notepad
B. Nano
C. Gedit
D. Grep
Correct Answer: D
Explanation
Option A: not correct Notepad is a text editor in the Windows system
Option B: not correct Nano is a tool used for the open text files in Linux
Option C: not correct Gedit is GUI based text editor in Linux
Option D: correct grep is a command-line utility for searching plain-text data sets for lines that match a regular expression
Reference: https://en.wikipedia.org/wiki/Grep
Domain: Information Security Tools
Q22: A pen-tester is attacking wireless networks using fake authentication and ARP request injection. Which tools should be used by a pen-tester?
A. Aircrack-ng
B. Aireplay-ng
C. Airman-ng
D. Wireshark
Correct Answer: B
Explanation
Option A: not correct Defacto WEP and WPA/ WPA 2- PSK cracking tool.
Option B: correct It is used for traffic generation fake authentication packet replay and ARP request injection.
Option C: not correct It is used to enable monitor mode on wireless interfaces from managed mode and vice versa.
Option D: not correct Wireshark allows attackers to read/capture live data from Ethernet, Token -Ring, FDDI, serial (PPP and SLIP), 802.11 wireless LAN, ATM connections, etc.
Reference: CEHv10, Ethical Hacking and Countermeasure EC-Council ( Module 16 Hacking Wireless Network)
Domain: Information Security Assessment Process
Q23: It is the process of replacing unwanted bits in an image and its source files with the secret data. Which of the term being described?
A. Spyware
B. Cryptography
C. Steganography
D. Backdoor
Correct Answer: C
Explanation
Option A: not correct Spyware is stealthy computer monitoring software that allows you to record all the user activities on the target computer secretly
Option B: not correct Cryptography is the practice of concealing information by converting plain text (readable format) into ciphertext (unreadable format) using a key or encryption scheme.
Option C: correct Steganography refers to the art of hiding data ” behind ” other data without the target’s knowledge. Steganography hides the existence of the message. It replaces bits of unused data into the usual files such as graphics, sound, text, audio, and video with some other surreptitious bits
Option D: not correct A backdoor is a program that can bypass the standard system authentication or conventional system mechanism like IDS, firewalls, etc . without being detected. In these types of breaches, hackers leverage backdoor programs to access the victim’s computer or a network.
Reference: CEHv10, Ethical Hacking and Countermeasure EC-Council (Module 06 System Hacking)
Domain: Network and Communication Technologies
Q24: Which protocol is used for setting up secure channels between two devices, typically in VPNs?
A. PPP
B. IPSEC
C. WPA
D. WEP
Correct Answer: B
Explanation
Option A: not correct PPP is protocol in WAN connection
Option B: correct
Options C & D: not correct WEP and WPA are encryption in wireless communication
Reference: https://en.wikipedia.org/wiki/Virtual_private_network
Domain: Information Security Tools
Q25: John the Ripper is a technical assessment tool used to test the weakness of which of the following?
A. Usernames
B. File permissions
C. Firewall rulesets
D. Passwords
Correct Answer : D
Explanation
Options A, B & C: not correct John the ripper targeted for password
Option D: correct John the ripper is the tool for brute force password attack. It is used to find a password combination.
Reference: CEHv10, Ethical Hacking and Countermeasure EC-Council (Module 13 Hacking Web Server)
Summary
We are hopeful that these Certified Ethical Hacker exam questions must have helped you get an assessment of the exam and you are more confident with your preparation now. We also provide you with more such Ethical Hacking practice exam Questions. Preparation is the key to success. Keep Learning!
- Top 25 DevSecOps Interview Question and Answers for 2024 - March 1, 2023
- How to prepare for VMware Certified Technical Associate [VCTA-DCV] Certification? - February 14, 2023
- Top 20 Cloud Influencers in 2024 - January 31, 2023
- 25 Free Question on SC-100: Microsoft Cybersecurity Architect - January 27, 2023
- Preparation Guide on MS-101: Microsoft 365 Mobility and Security - December 26, 2022
- Exam tips to prepare for Certified Kubernetes Administrator: CKA Exam - November 24, 2022
- Top Hands-On Labs To Prepare For AWS Certified Cloud Practitioner Certification - October 27, 2022
- Why do you need to upskill your teams with the Azure AI fundamentals? - October 11, 2022



