Here we bring the next topic “Granting Access to AWS Resources to Third Party via Roles and External Id” to help you in the AWS Certified Security Specialty exam preparation. This topic comes under the Identity and Access Management (IAM) domain as highlighted in the blueprint of AWS Certified Security Specialty exam guide.
Note that Identity and Access Management domain constitutes 20% of the total exam weight. So, this article will prove an invaluable resource in your AWS Certified Security Specialty exam preparation.
Problem Statement
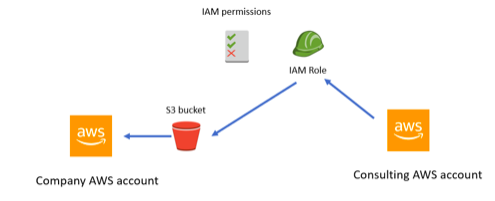
Let us take a common use case of consulting companies that need access to resources in an AWS account. Sometimes to carry out an audit of a company’s AWS account, a consultant company might need to have access to AWS resources in the company’s AWS account.
Giving Access Keys or creating an IAM user for this purpose is not the right way to go. Instead, you need to create an IAM Role that could be assumed and then have access to AWS resources (S3 in this example).
Below diagram shows this use case scenario:
Solution: Granting Access to AWS Resources to Third Party via Roles & External Id
To solve this scenario, you must carry out the following steps:
- First, we need to create an IAM policy that would grant access to the S3 bucket. This would be done in the Company AWS account.
- Next, we need to create an IAM role in the Company AWS account. This would have the policy assigned to it.
- We would ensure that the Consulting AWS account number is given the required permission to assume this role.
- The Consulting AWS account would then assume the role and then have access to the underlying S3 bucket.
Let’s look at an example on this using the AWS Console
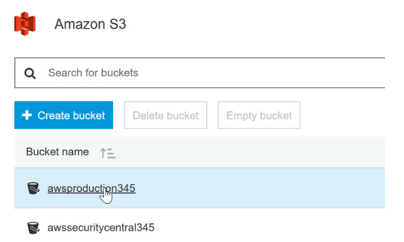
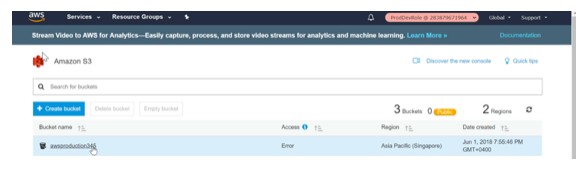
Step 1) Let’s assume that we have a bucket called awsproduction345 in an AWS account called cloud-production
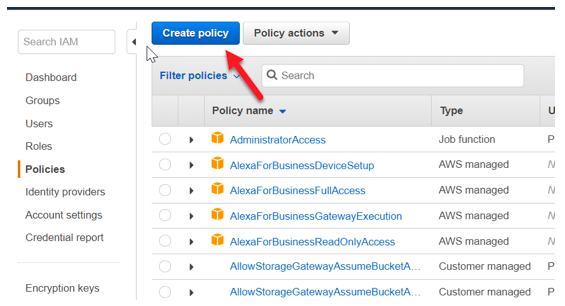
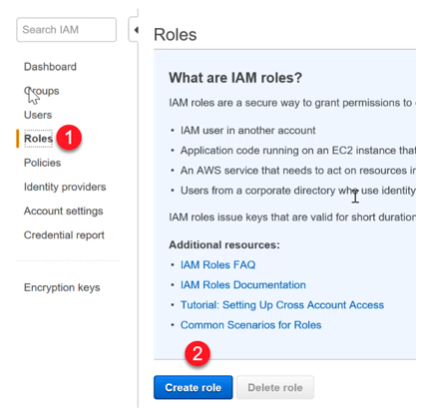
Step 2) Now let’s go to IAM and create a new policy
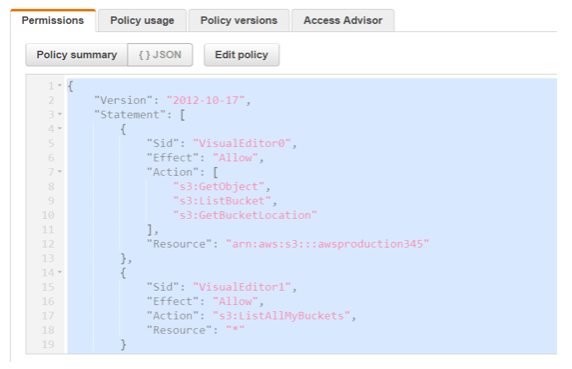
We then add the below JSON to give access to the S3 bucket
{ "Version": "2012-10-17", "Statement": [ { "Sid": "VisualEditor0", "Effect": "Allow", "Action": [ "s3:GetObject", "s3:ListBucket", "s3:GetBucketLocation" ], "Resource": "arn:aws:s3:::awsproduction345" }, { "Sid": "VisualEditor1", "Effect": "Allow", "Action": "s3:ListAllMyBuckets", "Resource": "*" } ] }
The policy gives access to get the objects from the S3 bucket.
Step 3) Now let us create a role
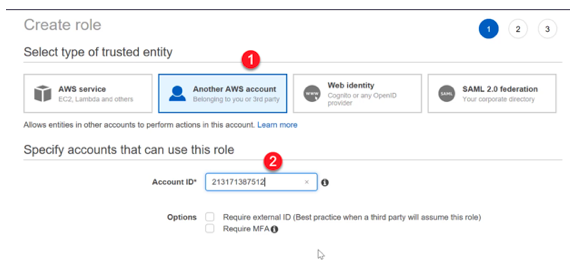
Step 4) Next, ensure that the trusted entity is “Another AWS account” (as shown in below image). Also, enter the account number of the AWS Consulting company. So here the consulting company would need to give you their account number.
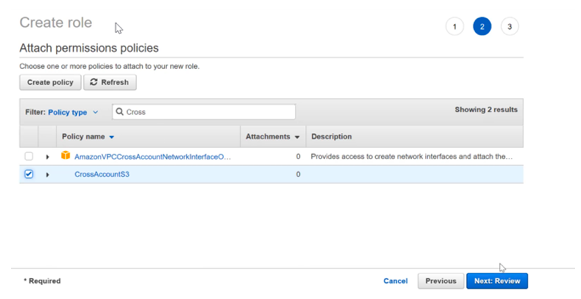
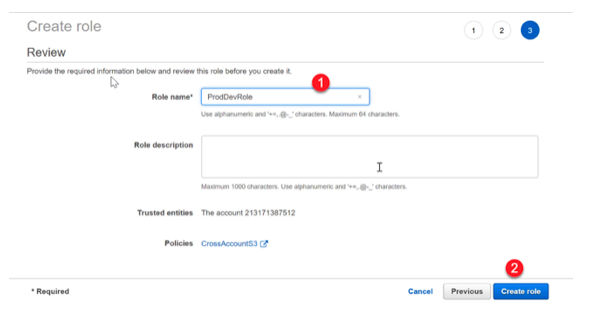
Step 5) For the role when the time to assign permissions comes, ensure to assign the IAM policy which was created in the earlier step
Let’s assume that we created the policy with the name of CrossAccountS3
Step 6) Next go ahead and create the role.
Step 7) Once the role is created, you need to take the ARN of the role. You need to give the role ARN to the Administrator of the Consulting Company.
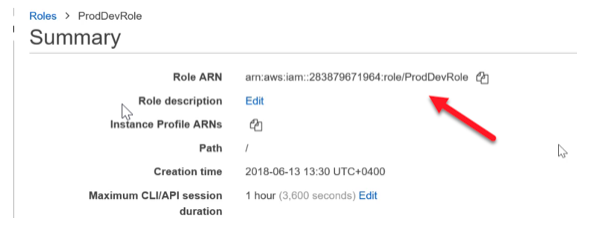
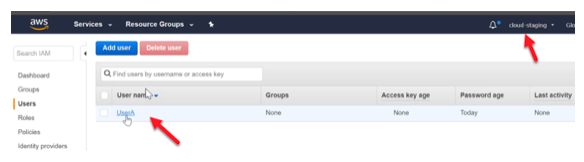
Step 8) Now for the consulting company to start using the role, in their account, they need to ensure that a user will have the ability to assume the role
Now let’s assume we are in the consulting company’s (i.e. 3rd party) AWS account. Let’s go to the user who is going to assume the role.
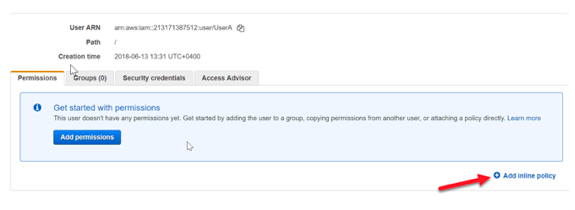
Step 9) Now go to the permissions and click on Add inline policy
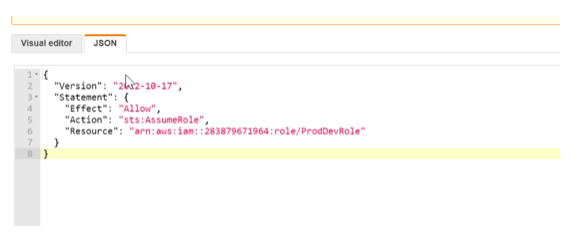
Step 10) In the JSON editor, add the policy for the user to assume the role which was created in the earlier step
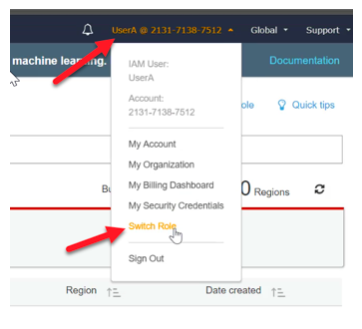
Step 11) Once you log in as the user, you can now switch roles as shown below:
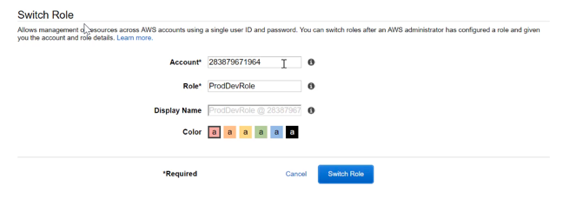
Step 12) Provide the account number of the main company’s AWS account, specify the Role name and then switch roles.
Once you do this, you will now be able to access the bucket in the production account
Other Related Resources:
Working with IAM and Bucket Policy
How to use a Central CloudTrail S3 Bucket for Multiple AWS Accounts?
How to set right inbound and outbound rules for Security Groups and NACLs?
Summary
- Cross-account roles are used to give users access to resources in other AWS accounts.
- The users can assume the role to have access to the resources in the external account.
- The IAM policy will govern what type of access will be given to the role.
- This is more secure than giving Access Keys for accessing the resources.
So, this is how you can grant access to AWS Resources to the third party via roles and external Id. It is very important to cover this topic while you are preparing for the AWS Security Specialty exam. Here we explained the solution with the example of the S3 bucket as an AWS resource. Hope this article helped you to understand the concepts of access granting to the third party. Once done with the preparation, you can check your preparation level with the AWS Certified Security Specialty practice tests.
Preparing with practice tests make you confident enough to pass the exam in the first attempt. So, join us now and become a certified AWS Security Specialist.
Need any other help with your AWS Certified Security Specialty exam preparation? Write in the comment below or reach us at Whizlabs Helpdesk, we’ll be happy to help you!
- Top 20 Questions To Prepare For Certified Kubernetes Administrator Exam - August 16, 2024
- 10 AWS Services to Master for the AWS Developer Associate Exam - August 14, 2024
- Exam Tips for AWS Machine Learning Specialty Certification - August 7, 2024
- Best 15+ AWS Developer Associate hands-on labs in 2024 - July 24, 2024
- Containers vs Virtual Machines: Differences You Should Know - June 24, 2024
- Databricks Launched World’s Most Capable Large Language Model (LLM) - April 26, 2024
- What are the storage options available in Microsoft Azure? - March 14, 2024
- User’s Guide to Getting Started with Google Kubernetes Engine - March 1, 2024




Hi,
how and where to generate external ID in 3rd party account. I came across that it would act as an additional layer of security.