If you are new to AWS world, we would like to inform you that being certified on AWS has great benefits for your career. Are you preparing for AWS Certified SysOps Administrator – Associate certification exam? Are you ready to pass this exam? In this blog, we are writing a series of articles on topics which are covered in the AWS Certified SysOps Associate certification exam. You can subscribe to us for receiving further updates on this topic.
The SysOps Associate certification exam is the hardest exam at the associate certification level. We would recommend you pass both solution architect associated certification exam and developer associated certification exam first before of taking this exam.
The AWS Certified SysOps Administrator – Associate exam validates technical expertise in deployment, management, and operations on the AWS platform
- TRY NOW : 10 Free Practice Questions for SysOps Associate Exam
- OFFER : 420 Practice Questions for SysOps Associate Exam (50% Discount)
The AWS Certified SysOps Administrator – Associate Level exam validates the candidate’s ability to:
- Deliver the stability and scalability needed by a business on AWS
- Provision systems, services, and deployment automation on AWS
- Ensure data integrity and data security on AWS technology
- Provide guidance on AWS best practices
- Understand and monitor metrics on AWS
Figure #0. Domains covered by the AWS Certified SysOps associate exam
You can download the related AWS Certified SysOps Administrator – Associate Level Exam Blueprint for more detail about it.
In this article, we are going to explain about the topic that addresses the ensure data integrity and access controls when using the AWS platform as highlighted in the AWS Blueprint from the above exam guide.
Context
Cloud security at AWS is the highest priority. As an AWS customer, you will benefit from a data center and network architecture built to meet the requirements of the most security-sensitive organizations. The access to your AWS resources should be following always the least privilege. It will warrant a better integrity, confidentiality and availability of your AWS resources and data/information.
Amazon Web Services Cloud Compliance enables customers to understand the robust controls in place at AWS to maintain security and data protection in the cloud. As systems are built on top of AWS cloud infrastructure, compliance responsibilities will be shared.
You’re responsible for securing your data, establishing access control list and encrypting your data for avoiding information risks. AWS provides you several alternatives to secure your data files when you’re using the Amazon Simple Storage Service (Amazon S3) as follow.
What is Amazon S3?
Amazon Simple Storage Service (Amazon S3) is storage for the Internet. You can use Amazon S3 to store and retrieve any amount of data at any time, from anywhere on the web.
It’s a simple storage service that offers software developers a highly-scalable, reliable, and low-latency data storage infrastructure at very low costs.
You can store virtually any kind of data in any format. The total volume of data and number of objects you can store are unlimited. Individual Amazon S3 objects can range in size from a minimum of 0 bytes to a maximum of 5 terabytes. The largest object that can be uploaded in a single PUT is 5 gigabytes. For objects larger than 100 megabytes, customers should consider using the Multipart Upload capability.
You can accomplish these tasks using the simple and intuitive web interface of the AWS Management Console.
How to use S3?
Amazon S3 provides a simple web service interface that you can use to store and retrieve any amount of data, at any time, from anywhere on the web. Amazon S3 is also designed to be highly flexible.
There are many of the ways you can use Amazon S3 like:
- Backup and Storage: Provide data backup and storage services for others.
- Application Hosting: Provide services that deploy, install, and manage web applications.
- Media Hosting: Build a redundant, scalable, and highly available infrastructure that hosts video, photo, or music uploads and downloads.
- Software Delivery: Host your software applications that customers can download.
Controlling the access to your files
Amazon S3 provides authentication mechanisms to secure data stored in Amazon S3 against unauthorized access. By default, all Amazon S3 resources—buckets, objects, and related subresources— are private: only the resource owner, an AWS account that created it, can access the resource. The resource owner can optionally grant access permissions to others by writing an access policy.
Amazon S3 offers access policy options broadly categorized as resource-based policies and user policies.
| Type | Brief description |
| Resource-based policies | Access policies you attach to your resources (buckets and objects) are referred to as resource-based policies. Both bucket policies and access control lists (ACLs) are resource-based policies.Each bucket and object have an ACL associated with it. An ACL is a list of grants identifying grantee and permission granted.For your bucket, you can add a bucket policy to grant other AWS accounts or IAM users permissions for the bucket and the objects in it. |
| User policies | Access policies you attach to your users in your account are called user policies.You can use AWS Identity and Access Management (IAM) to manage access to your Amazon S3 resources. Using IAM, you can create IAM users, groups, and roles in your account and attach access policies to them granting them access to AWS resources including Amazon S3. |
Table # 1. Type of policies related
You may choose to use resource-based policies, user policies, or some combination of these to manage permissions to your Amazon S3 resources. Amazon S3 supports user authentication to control access to data. A bucket policy is a JSON access policy options available for you to grant permission to your Amazon S3 resources:
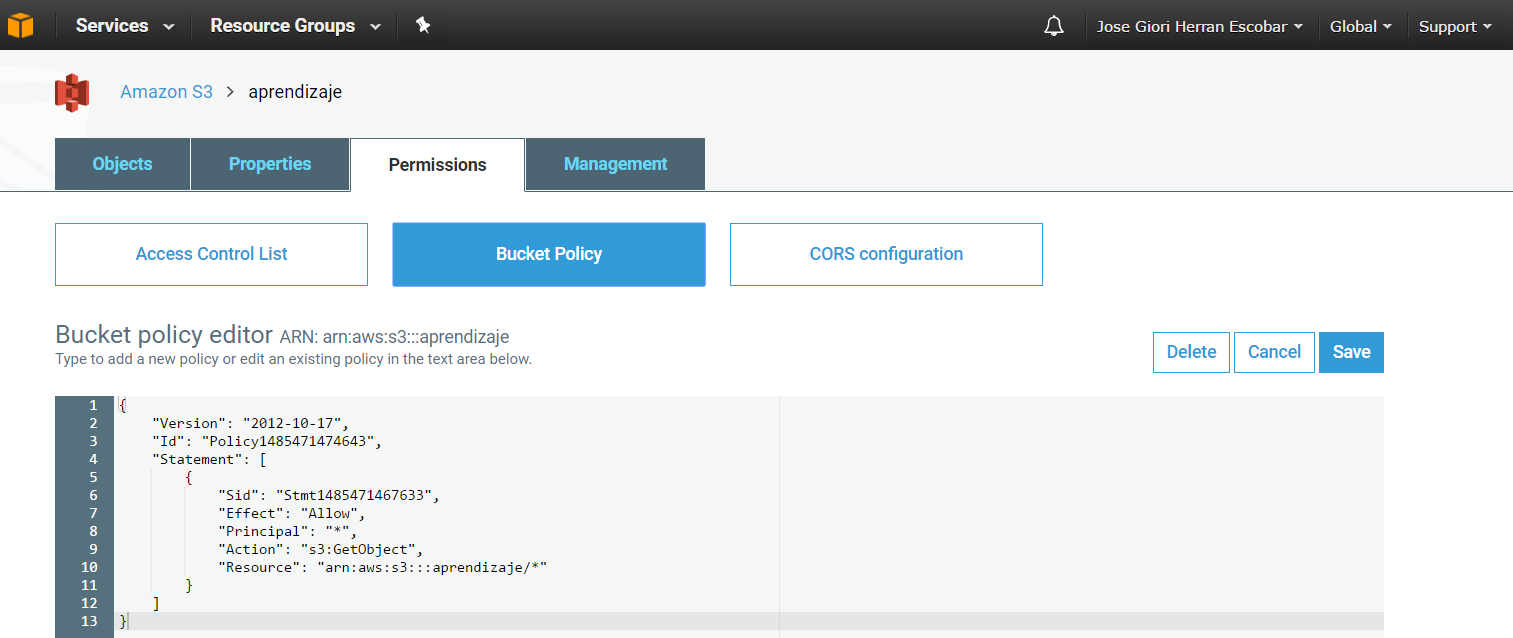
Figure #2. A bucket Policy sample
You can use access control mechanisms such as bucket policies and Access Control Lists (ACLs) to selectively grant permissions to users and groups of users. You can securely upload/download your data to Amazon S3 via SSL endpoints using the HTTPS protocol. If you need extra security you can use the Server Side Encryption (SSE) option or the Server Side Encryption with Customer-Provide Keys (SSE-C) option to encrypt data stored-at-rest. Amazon S3 provides the encryption technology for both SSE and SSE-C. Alternatively, you can use your own encryption libraries to encrypt data before storing it in Amazon S3.
Availability and Durability according to Type
For data protection, the best practice is to have a backup and to put in place safeguards against malicious or accidental user’s errors. For S3 data files, that best practice includes secure access permissions, Cross-Region Replication, versioning and a functioning, regularly tested backup.
The S3 Standard is designed for 99.99% availability and the Amazon S3 buckets in all Regions provide read-after-write consistency for PUTS of new objects and eventual consistency for overwrite PUTS and DELETES.
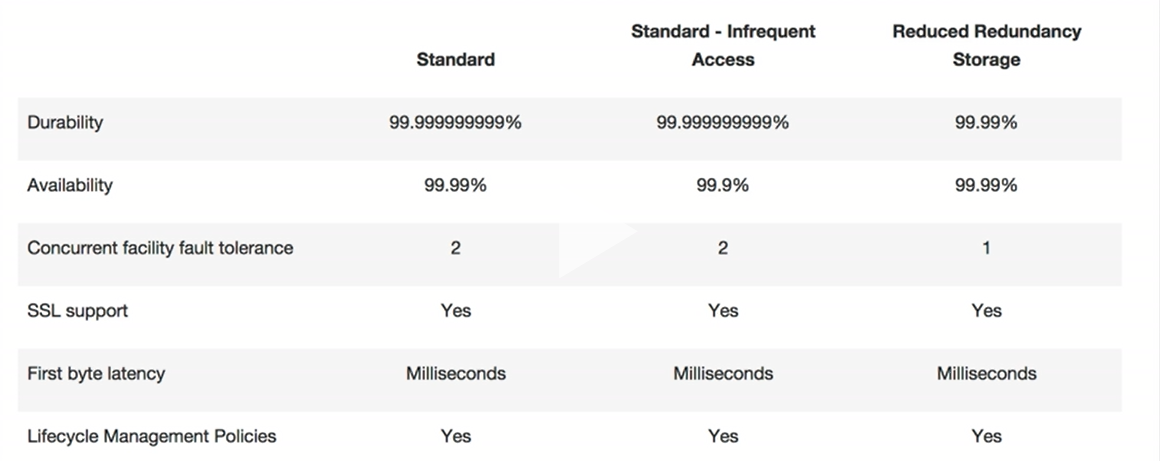
Figure #3. Durability and Availability characteristics according to S3 type
Versioning Data Files
Versioning is a means of keeping multiple variants of an object in the same bucket. You can use versioning to preserve, retrieve, and restore every version of every object stored in your Amazon S3 bucket. With versioning, you can easily recover from both unintended user actions and application failures.
Versioning-enabled buckets enable you to recover objects from accidental deletion or overwrite. You can enable versioning following the instructions:
To enable or disable versioning on an S3 bucket
- Sign in to the AWS Management Console and open the Amazon S3 console at https://console.aws.amazon.com/s3/.
- In theBucket name list, choose the name of the bucket that you want to enable versioning for.
- ChooseProperties and select the option Versioning.
- ChooseEnable versioning or Suspend versioning, and then choose Save, as you can see in the following figure:
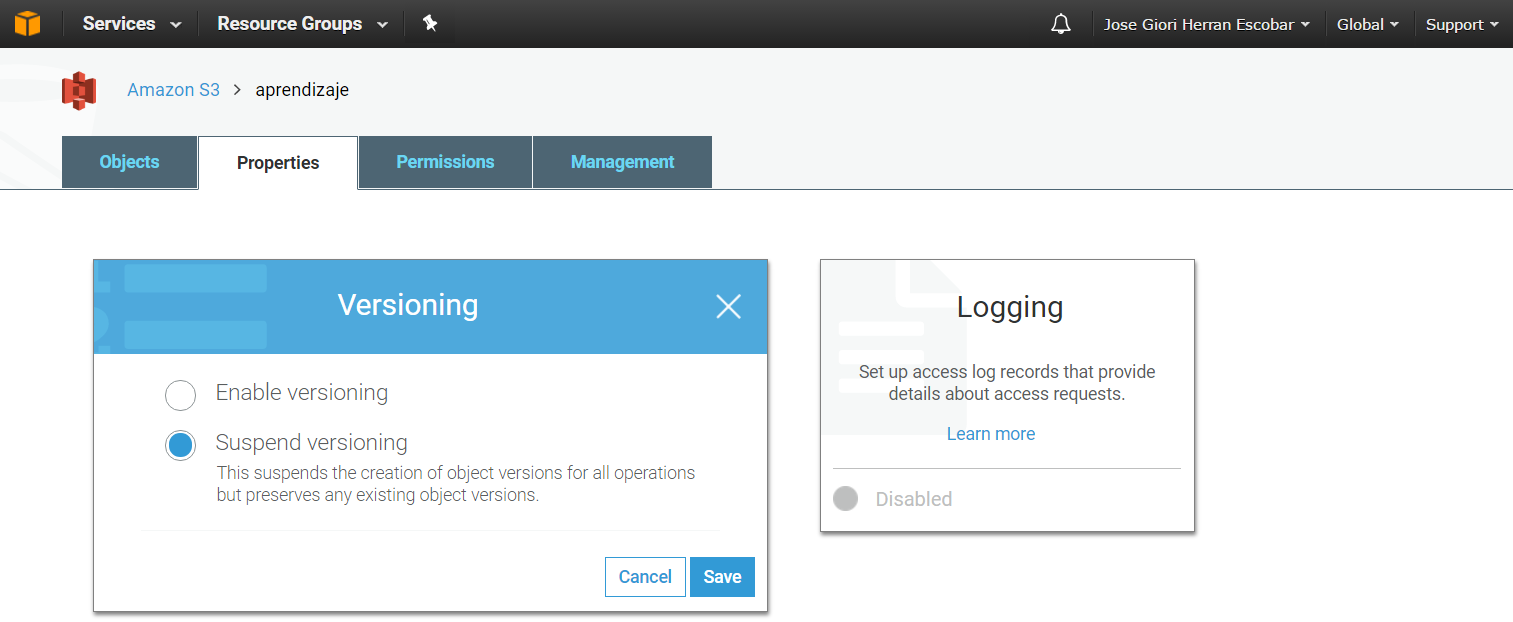
Figure #4. Enabling or Suspending Versioning into an S3 bucket
Remember that if you suspend versioning into a bucket, from that moment you’re suspending the creation of new object versions, but it preserves object versions created before.
You can optionally add another layer of security by configuring a bucket to enable MFA (Multi-Factor Authentication) Delete, which requires additional authentication for either of the following operations:
- Change the versioning state of your bucket
- Permanently delete an object version
Versioning could be integrated and used in conjunction with Lifecycle rules.
Lifecycle Rules
You can set Lifecycle rules to manage the lifetime and the cost of storing multiple versions of your objects.
Lifecycle configuration enables you to specify the lifecycle management of objects in a bucket. The configuration is a set of one or more rules, where each rule defines an action for Amazon S3 to apply to a group of objects.
These actions can be classified as follows:
- Transition actions: In which you define when objects transition to another storage class. For example, you may choose to transition objects to the STANDARD_IA (IA, for infrequent access) storage class 30 days after creation or archive objects to the GLACIER storage class one year after creation.
- Expiration actions: In which you specify when the objects expire. Then Amazon S3 deletes the expired objects on your behalf.
Important Points to Remember for the AWS Certified SysOps Administrator – Associate Certification exam
- Amazon S3 is a service that provides storage for the internet. You can use it to store and retrieve any amount of data at any time, from anywhere on the web
- There is not limit the total volume of data and number of objects you can store
- All S3 objects storage could be accessed directly using an Internet URL
- An Amazon S3 object have 0 bytes to a maximum of 5 terabytes of size
- You should consider using the Multipart Upload capability when you’re uploading big data files (>100 MB) uploading parts in parallel to improve throughput
- You can set an S3 Bucket policy to make all data files stored in a bucket, public
- Amazon S3 provides the encryption technology for both SSE and SSE-C
- You should use versioning to preserve, retrieve, and restore any version of an S3 object stored
- You can implement a rollback window for your Amazon S3 objects, combining Lifecycle rules and Versioning.
- You could use Amazon CloudFront to serve content as a method of controlling access to your S3 data file content by requiring users to use signed URLs.
- You can enable MFA delete, it requires and additional authentication before to delete a file
Glossary
| Term | Brief description |
| Access Control List (ACL) | A document that defines who can access a particular bucket or object. Each bucket and object in Amazon S3 has an ACL. The document defines what each type of user can do, such as write and read permissions. |
| Authenticated Encryption | Encryption that provides confidentiality, data integrity, and authenticity assurances of the encrypted data. |
| S3 Access Policy | A document defining permissions that apply to a user, group, or role; the permissions in turn determine what users can do into an S3 bucket. A policy typically allows access or can also explicitly deny access. |
| Delete Marker | An object with a key and version ID, but without content. Amazon S3 inserts delete markers automatically into versioned buckets when an object is deleted. |
| Private Content | When using Amazon CloudFront to serve content with an Amazon S3 bucket as the origin, a method of controlling access to your content by requiring users to use signed URLs. Signed URLs can restrict user access based on the current date and time and/or the IP addresses that the requests originate from. |
| Versioning | Every object in Amazon S3 has a key and a version ID. Objects with the same key, but different version IDs can be stored in the same bucket. Versioning is enabled at the bucket layer using PUT Bucket versioning. |
Summary
In this article, we have explained about the data integrity and access control associated to data files storage at Amazon S3, and how to use access control lists and policies to secure your vital information using security best practices, guaranteeing high availability, continuity and recovery against a disaster.
References:
[1] Amazon S3 FAQs. Amazon AWS. https://aws.amazon.com/s3/faqs
[2] Amazon S3 Documentation. Amazon AWS. https://aws.amazon.com/documentation/s3
[3] AWS Certified SysOps Administrator – Associate Certification.https://aws.amazon.com/certification/certified-sysops-admin-associate/
- Top 20 Questions To Prepare For Certified Kubernetes Administrator Exam - August 16, 2024
- 10 AWS Services to Master for the AWS Developer Associate Exam - August 14, 2024
- Exam Tips for AWS Machine Learning Specialty Certification - August 7, 2024
- Best 15+ AWS Developer Associate hands-on labs in 2024 - July 24, 2024
- Containers vs Virtual Machines: Differences You Should Know - June 24, 2024
- Databricks Launched World’s Most Capable Large Language Model (LLM) - April 26, 2024
- What are the storage options available in Microsoft Azure? - March 14, 2024
- User’s Guide to Getting Started with Google Kubernetes Engine - March 1, 2024




Perfect one on aws s3 data security. Thanks