Amongst all the Azure services, Sentinel is one of the most crucial ones in the lot. Azure Sentinel offers security intelligence aspects for your enterprise. The data essential for the analysis is programmed to be stored within Azure Monitor Log Analytics space. Progressing to the cloud doesn’t keep you blindly safe from all of the security hassles; it does need protection! Cloud services are more prominent targets, just like any of the other on-premise systems. It is solely because they are gaining popularity in today’s era. There are people or programs that are looking for ideal opportunities to steal information from cloud users, and Azure Sentinel intends to stop that.
Any large organization that is connected with a lot of cloud services eventually misses out on keeping track of all of them, which is what becomes an opportunity for information hackers. Therefore, organizations need to adapt ideal measures for identifying those issues beforehand and fill the gaps before someone takes advantage of it. Therefore, protective systems need to be engaged at the right time to detect serious problems but should also be smart enough to avoid raising false alarms, as it might disturb the entire administration work.
Azure Sentinel is the new service that is currently in play! It is a security intelligence service that offers ideal protection and cloud service management by integrating Artificial Intelligence on priority. Therefore, if your business is operating with cloud services, then this article will be reviewing and educating you about Azure Sentinel and its important attributes.
In-Depth Overview of Azure Sentinel
Azure Sentinel is the new SIEM (Security Information and Native Management)! As the name suggests, this software or service intends to offer you a complete overview of the security status within an infrastructure. The information within the cloud usually comes from diverse sources that include system logs as well. All of that information is organized in an appropriate manner to ensure that it covers almost everything. The functionality of this software or service also includes issue reporting, event collection, information mapping, and other such activities.
Azure Sentinel is native to Azure and was launched in 2019. Anyone who has an active Azure account can access the features of Azure Sentinel. There are many other cloud SIEM tools within the platform, but Azure Sentinel is designed in a way to help Azure cloud grow and thrive, without even a tiny possibility of a security loophole. As per the administrators are concerned, they believe that the major turning point for Azure Sentinel is its dashboard, as it offers ideal ways of looking at the security aspects or situation within the cloud. The toolbar within the dashboard enlightens you about the various information based upon the alerts and events over a specified period of selected time span. Along with that, it also gives elaboration upon the recently investigated or closed events as per the security norms. Not just that, but there are innumerable types of views available within the dashboard that include a geospatial view of all of the malicious activities embedded in your cloud services.
AZ-304: Azure Architect Design exam is intended for the Solution Architects. Prepare with Azure AZ-303 training course and get ready to become a Microsoft Certified Azure Architect. Try the Free Test today!
Apart from that, Azure Sentinel Dashboard also includes Azure AD Logs, Insecure protocols, firewall information, Azure activities, and a lot of other insights. Moreover, you get the chance to customize your dashboard and implement role-based authorization upon it. It means that people, who possess different roles within your organization or IT department, can be given the necessary authorization to access the Sentinel Dashboard. You can customize more than one dashboard within Azure Sentinel, and the IT staff can be given access to respective dashboards related to their jobs or unified access to all of them.
Attributes of Azure Sentinel
Azure Sentinel is built over the Log Analytics Workspace, for which it has the potential to collect information from all the security logs and turn around the information into a properly managed format. Some of the services from which Azure Sentinel is actively collecting data are Microsoft Cloud App Security, Azure Identity Protection, Azure Information Protection, Azure Threat Protection, and others.
Currently, Azure Sentinel is also in integration with some of the exclusive third-party tools. One such tool is Cisco ASA! There is a plan to integrate more third party tools into Azure Sentinel in the coming time. Currently, you can take Azure Sentinel as a cloud-native, scalable, SIEM and SOAR (Security Orchestration Automated Response) solution. It is the tracking hub for you to ensure that the enterprise operations within the cloud services are safe from malicious attacks or activities. Some of the core efficacies offered by Azure Sentinel includes:
- You get to collect the data at a high-end cloud scale, irrespective of the devices, users, infrastructure, and applications. It doesn’t matter whether the data is on-premise or across different clouds; Azure Sentinel is an ideal choice for offering security prospects to them all.
- With Azure Sentinel, you will be able to detect all of the threats that went undetected in your random search or filtering process. Moreover, this will help reduce the number of false alarms raised by your previous security assistant. Azure Sentinel does this with the assistance of threat intelligence and Microsoft analytics potential.
- Artificial Intelligence is the key for all features offered by Azure Sentinel. With the use of AI, Sentinel hunts down all of the suspicious activities within your cloud services.
- The best part of Azure Sentinel is that it responds to security threats immediately, without delays. It is possible due to the built-in orchestration potential, along with the automation of some possible tasks.
The cycle of Azure Sentinel is pretty much simple, as it collects the security data across your enterprises, detects the threats, investigates the critical incidents with the help of AI, and responds to it with automated protection or by raising alarms. Azure Sentinel does have a lot of connectors, especially for Microsoft Solutions, that come with the potential of real-time integration. Some of the probable connectors include Microsoft 365 Defender solutions, Microsoft 365 sources, Microsoft Defender for the Identity, and others. Apart from that, you will also explore the built-in connectors for widening the ecosystem of security offered by the Sentinel. It is especially for the non-Microsoft solutions!
How to Enable Azure Sentinel?
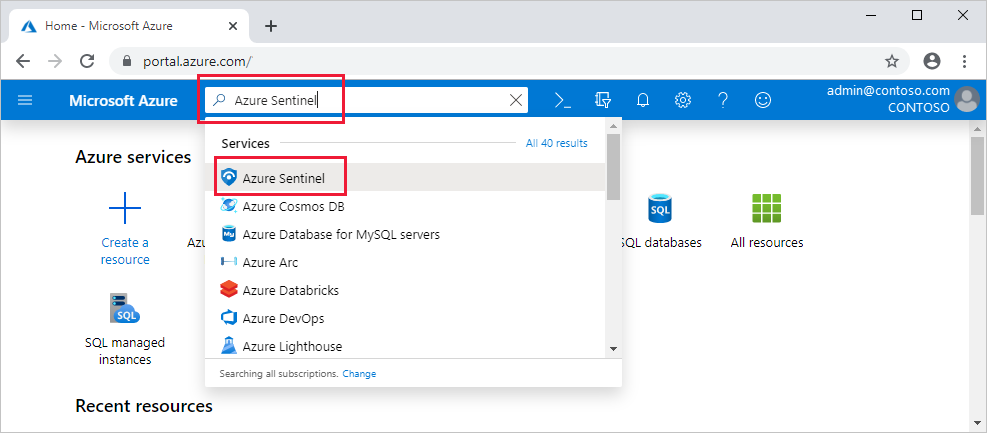
Now that you are aware of how the Microsoft Azure Sentinel actually works, you need to get an insight into the steps of enabling the Azure Sentinel perks. And for that, you need to keep in mind these steps, as stated below:
- You need to sign in to the Azure Portal first! You need to have an active subscription within Azure, to be able to access Azure Sentinel or enable it.
- After entering the portal, you need to search for the ‘Azure Sentinel’ tab and select it for further process.
- Now, in the new dialog box, you will see an option to ‘Add.’ Click on it!
- Now, you need to select the workspace that you intend to use for enabling Azure Sentinel. If you do not have an existing workspace, then you can always create one.
- Now, go ahead and select the option ‘Add Azure Sentinel.’ And the process is complete!
Connecting the Data Sources to Azure Sentinel
Azure Sentinel has the potential of ingesting data from diverse apps and services by connecting them to the Sentinel service. In addition to that, it will forward the logs and events to Sentinel! For all of the Virtual and Physical machines, you can prefer installing the agent for Log Analytics that will take care of collecting the log and passing them on to the Azure Sentinel. Similarly, for the proxies and firewalls, Azure Sentinel intends to install the agent of Log Analytics onto the Linux Syslog server for the collection of data.
And it evidently proves that it is important to connect the data sources to Azure Sentinel for enabling its functionality. Azure Sentinel demands an ideal connection to all of your security sources at first. It is because, without this access, the Sentinel will have no functionality to execute upon securing your cloud services. To know in-depth details on how you can connect the data sources to Azure Sentinel, refer to the official documentation. But the crucial steps of connecting the data sources are stated below:
- Head to the main menu and choose ‘Data Connectors’ for opening up the gallery of data connectors.
- The gallery will consist of a list of all of the data sources that is available for the Sentinel to connect with.
- Select the data source from the list, and then click on the ‘Open Connector Page’ tab.
- The connector page will then show you the instructions for further configuration of the connector. Apart from that, any of the additional instruction that might seem essential is also displayed over this page.
- Follow the specified instructions and give the required information, to move onto the next step.
- You will see a tab ‘Next Steps’ over the connector page that will show you relevant built-in workbooks, analytics rule templates, and sample queries that will go along with the data connector. You need to select them for use or modify them to get effective insights into your data.
After completing all of these steps, all of your data and security sources will be connected to Azure Sentinel. Now, your data streaming will commence onto the Microsoft Azure Sentinel hub, and you will be ready to work with it. You can now build queries within Log Analytics for data investigation or view the available logs over the workbooks.
How to Use the Built-in Workbooks within Azure Sentinel?
Built-in workbooks are hubs to provide you the data that has been integrated from all of the connected data sources. It will allow you to dive deep into the events generated in all of those services. Some of the built-in workbooks are Azure activity events and Azure AD. The workbooks can also be based upon on-premise attributes that include data from firewall traffic logs, Office 365, Windows events from the servers, and others. These workbooks co-relate to the workbooks of Azure Monitor. And this aspect will offer you ideal customizability & flexibility upon designing one of your own. To know more about Azure Monitor workbooks, you should refer to the official documentation!
Follow these below steps to get an idea of how to use the built-in workbooks efficiently to leverage the potential of Microsoft Azure Sentinel:
- Go to the settings tab within your Azure Sentinel dashboard.
- Now select ‘Workbooks’ from the available options.
- Go to the ‘Installed’ tab, and you will get a list of all of the installed workbooks.
- Change the filter to ‘All’ by clicking on the given tab to get an entire gallery of built-in workbooks that are ready for installation.
- Run your search for the specific workbook to get a complete description and list of what each of it is offering.
- For instance, if you are using Azure AD to start Azure Sentinel’s execution, then you should go ahead and install a few of the workbooks, such as Azure AD sign-ins and Azure AD audit logs.
- Now, consider adding a workbook for the respective firewall. You can go ahead and add the Palo Alto workbook, which has features of analyzing the traffic of firewall and will provide you with co-relations between the treat events and important firewall data. It is just one of the many options available over the list of built-in workbooks.
To know more about how to create new workbooks, rather than using the one pre-set within Azure Sentinel, refer to this official documentation of Microsoft.
Final Words
Hence, this is all about the theoretical details associated with Azure Sentinel. Now, all you need to do is execute its true potential by putting your hands and mind into it. But for that, you need to understand the conceptual aspects of Azure Sentinel and what it has to offer! Check the Azure Sentinel pricing as well to decide upon the plan you wish to prefer!
Understand the use, execute the steps and connect your data sources to Azure Sentinel! Hence, this is all you need to do to get your cloud services and data secured and safe from malicious threats and hacking attempts.
- Top 20 Questions To Prepare For Certified Kubernetes Administrator Exam - August 16, 2024
- 10 AWS Services to Master for the AWS Developer Associate Exam - August 14, 2024
- Exam Tips for AWS Machine Learning Specialty Certification - August 7, 2024
- Best 15+ AWS Developer Associate hands-on labs in 2024 - July 24, 2024
- Containers vs Virtual Machines: Differences You Should Know - June 24, 2024
- Databricks Launched World’s Most Capable Large Language Model (LLM) - April 26, 2024
- What are the storage options available in Microsoft Azure? - March 14, 2024
- User’s Guide to Getting Started with Google Kubernetes Engine - March 1, 2024


