Are you preparing for AWS Certified SysOps Administrator – Associate certification exam? Are you ready to pass this exam? In this blog, we are writing a series of articles on topics which are covered in the AWS certified SysOps associate certification exam. You can subscribe to us for receiving further updates on this topic.
The SysOps Associate certification exam is the hardest exam at the associate certification level. We would recommend you pass both solution architect certification exam and developer associated certification exam first before of taking this exam.
The AWS Certified SysOps Administrator – Associate exam validates technical expertise in deployment, management, and operations on the AWS platform
- TRY NOW : 10 Free Practice Questions for SysOps Associate Exam
- OFFER : 420 Practice Questions for SysOps Associate Exam (50% Discount)
The AWS Certified SysOps Administrator – Associate Level exam validates the candidate’s ability to:
- Deliver the stability and scalability needed by a business on AWS
- Provision systems, services, and deployment automation on AWS
- Ensure data integrity and data security on AWS technology
- Provide guidance on AWS best practices
- Understand and monitor metrics on AWS

Figure #0. Domains covered by the AWS Certified SysOps associate exam
You can download the related AWS Certified SysOps Administrator – Associate Level Exam Blueprint for more detail about it.
In this article, we are going to explain about the topic that addresses the assurance of access controls when using the AWS platform as highlighted in the AWS Blueprint from the above exam guide.
Context
From an enterprise point of view, the asset security is one of most important things for taking in count when you are designing and running infrastructure services. The access to your AWS resources should be following always the least privilege. It will warrant a better integrity, confidentiality and availability of your AWS resources.
As part of your AWS account, AWS offers a feature called AWS Identity and Access Management (IAM) for controlling the access to your AWS resources.
What is AWS Identity and Access Management (IAM)?
AWS Identity and Access Management (IAM) enables you to securely control access to AWS services and resources for your users. Using IAM, you can create and manage AWS users and groups, and use permissions to allow and deny their access to AWS resources.
You can use AWS IAM to securely control individual and group access to your AWS resources. You can create and manage user identities (“IAM users”) and grant permissions for those IAM users to access your resources. You can also grant permissions for users outside of AWS.
IAM is a feature of your AWS account offered at no additional charge. You will be charged only for use of other AWS services by your users.
You can use the IAM console (for web-based access), the AWS Command Line Interface (CLI, for command line access), or the API or SDKs (for programmatic access). To grant permissions, you create policy documents that you attach to users, groups, or other entities
How to Create Groups?
You use IAM to control who can use your AWS resources (authentication) and what resources they can use and in what ways (authorization). For greater security and organization, you can give access to your AWS account to specific user. When assign permissions, use Groups to assign permissions to multiple IAM Users and apply to those groups pre-build secure policies.
A group is a collection of IAM users. Manage group membership as a simple list:
- Add users to or remove them from a group.
- A user can belong to multiple groups.
- Groups cannot belong to other groups.
- Groups can be granted permissions using access control policies. This makes it easier to manage permissions for a collection of users, rather than having to manage permissions for each individual user.
- Groups do not have security credentials, and cannot access web services directly; they exist solely to make it easier to manage user permissions.
To create an IAM group and attach policies using the AWS Management Console, you should:
Step 1. Create a New Group, after signing in to the IAM console at https://console.aws.amazon.com/iam/ :
Group names must be unique within an account. They are not distinguished by case, for example, you cannot create groups named both “ADMINS” and “admins”.
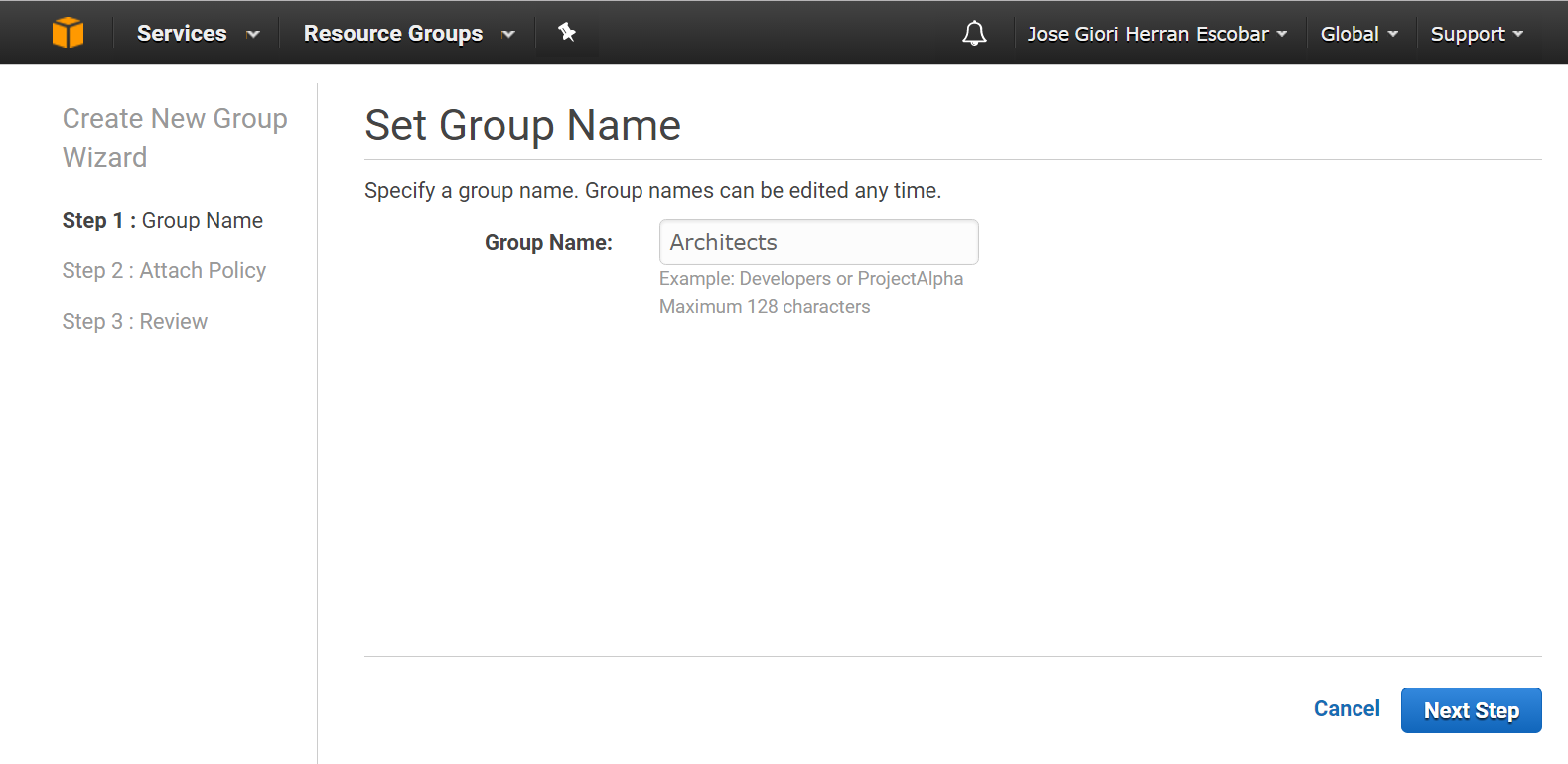
Figure #1. Creating a Group
Step 2. Select and attach policies. In the list of policies, select the check box for each policy that you want to apply to all members of the group.
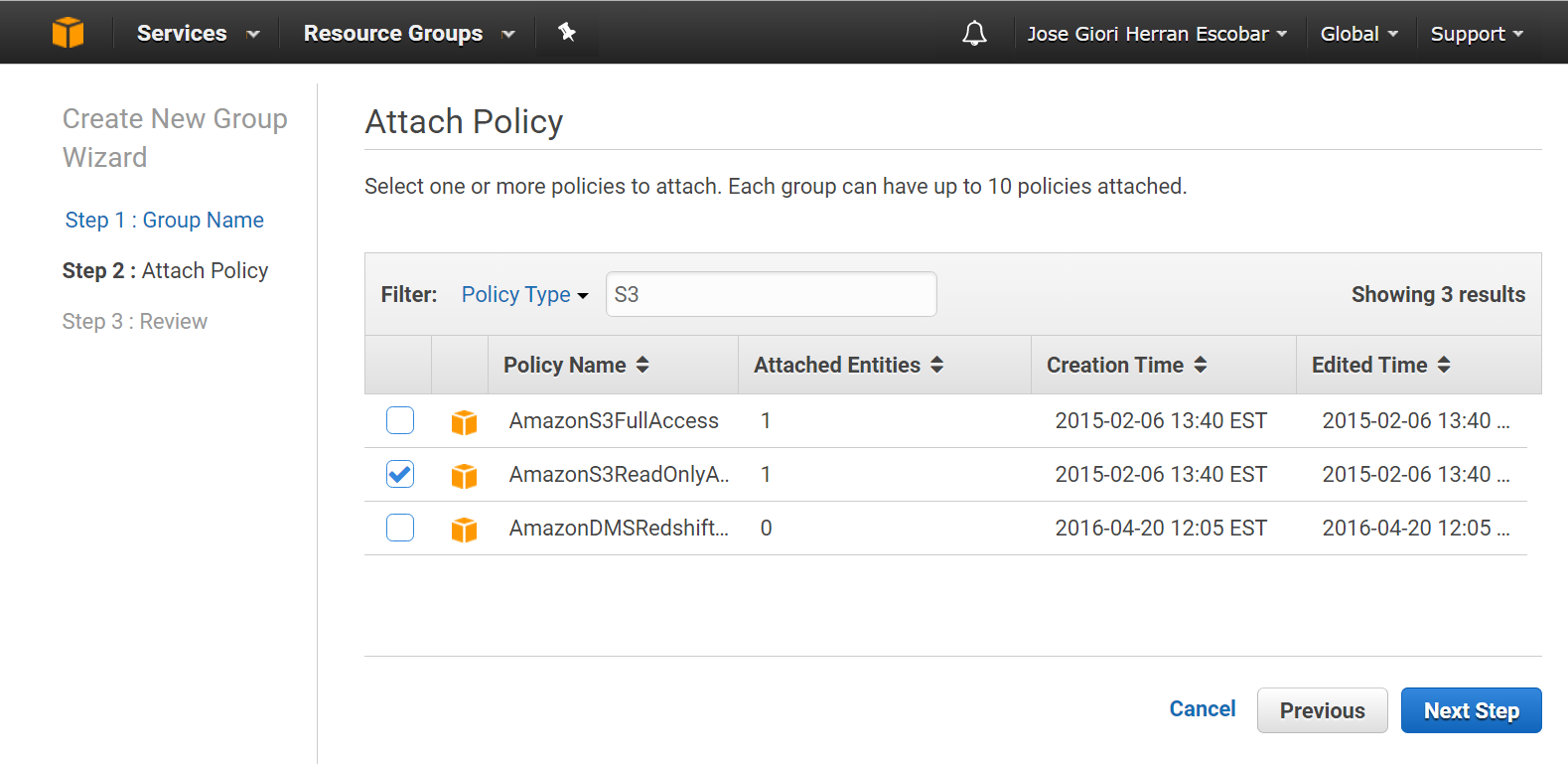
Figure #2. Attaching a Policy
You can use roles to delegate access to users, applications, or services that don’t normally have access to your AWS resources. You can use IAM roles to grant permissions to applications running on your instances that need to use a bucket in Amazon S3. You can specify permissions for IAM roles by creating a policy in JSON format. These are like the policies that you create for IAM users. If you make a change to an IAM role, the change is propagated to all instances.
Security Credentials
IAM users can have any combination of credentials that AWS supports, such as an AWS access key, X.509 certificate, SSH key, password for web app logins, or an MFA device.
You can access AWS in diverse ways using the diverse types of credentials that can be associated with a user:
- Console password: A password that the user can type to sign into interactive sessions such as the AWS Management Console.
- Access keys: An access key is the combination of an access key ID and a secret access key. You can assign two to a user at a time. These can be used to make programmatic calls to AWS when using the API in program code or at a command prompt when using the AWS CLI or the AWS PowerShell tools.
- SSH keys for use with AWS CodeCommit: An SSH public key in the OpenSSH format that can be used to authenticate with AWS CodeCommit.
- Server certificates: SSL/TLS certificates that you can use to authenticate with some AWS services. We recommend that you instead use AWS Certificate Manager to create and manage your certificates
You can also use the AWS Security Token Service (AWS STS) to create and provide trusted users with temporary security credentials that can control access to your AWS resources. Temporary security credentials work almost identically to the long-term access key credentials that your IAM users can use
IAM Best Practices
To help secure your AWS resources, follow these recommendations and best practices for the IAM feature:
- Lock Away Your AWS Account (Root) Access Keys: You use an access key (an access key ID and secret access key) to make programmatic requests to AWS. However, do not use your AWS account (root) access key
- Create Individual IAM Users: Avoid using your AWS root account credentials to access AWS, always create individual users for anyone who needs access to your AWS services
- Use AWS-Defined Policies to Assign Permissions Whenever Possible: We recommend that you use the managed policies that are created and maintained by AWS to grant permissions whenever possible.
- Use Groups to Assign Permissions to IAM Users: First, create groups that relate to job functions (sysops, architects, developers, etc.). After, define the relevant permissions for each group. Finally, assign IAM users to those groups.
- Grant Least Privilege: When you create IAM policies, follow the standard security advice of granting least privilege—that is, granting only the permissions required to perform a task.
- Use Access Levels to Review IAM Permissions: To improve the security of your AWS account, you should regularly review and monitor each of your IAM policies.
- Configure a Strong Password Policy for Your Users: If you allow users to change their own passwords, require that they create strong passwords and that they rotate their passwords periodically
- Enable MFA for Privileged Users: For extra security, enable multi-factor authentication (MFA) for privileged IAM users
- Use Roles for Applications That Run on Amazon EC2 Instances: Applications that run on an Amazon EC2 instance need credentials to access other AWS services. To provide credentials to the application in a secure way, use IAM roles.
- Delegate by Using Roles Instead of by Sharing Credentials: You can define a role that specifies what permissions the IAM users from another AWS account to access resources in your AWS account. You can also designate which AWS accounts have the IAM users that can assume the role.
When you connect to the IAM Dashboard, you can check the security status related to the before security best practices, also you can customize the IAM users sign-in link, initially, the URL has as prefix your account number as following:
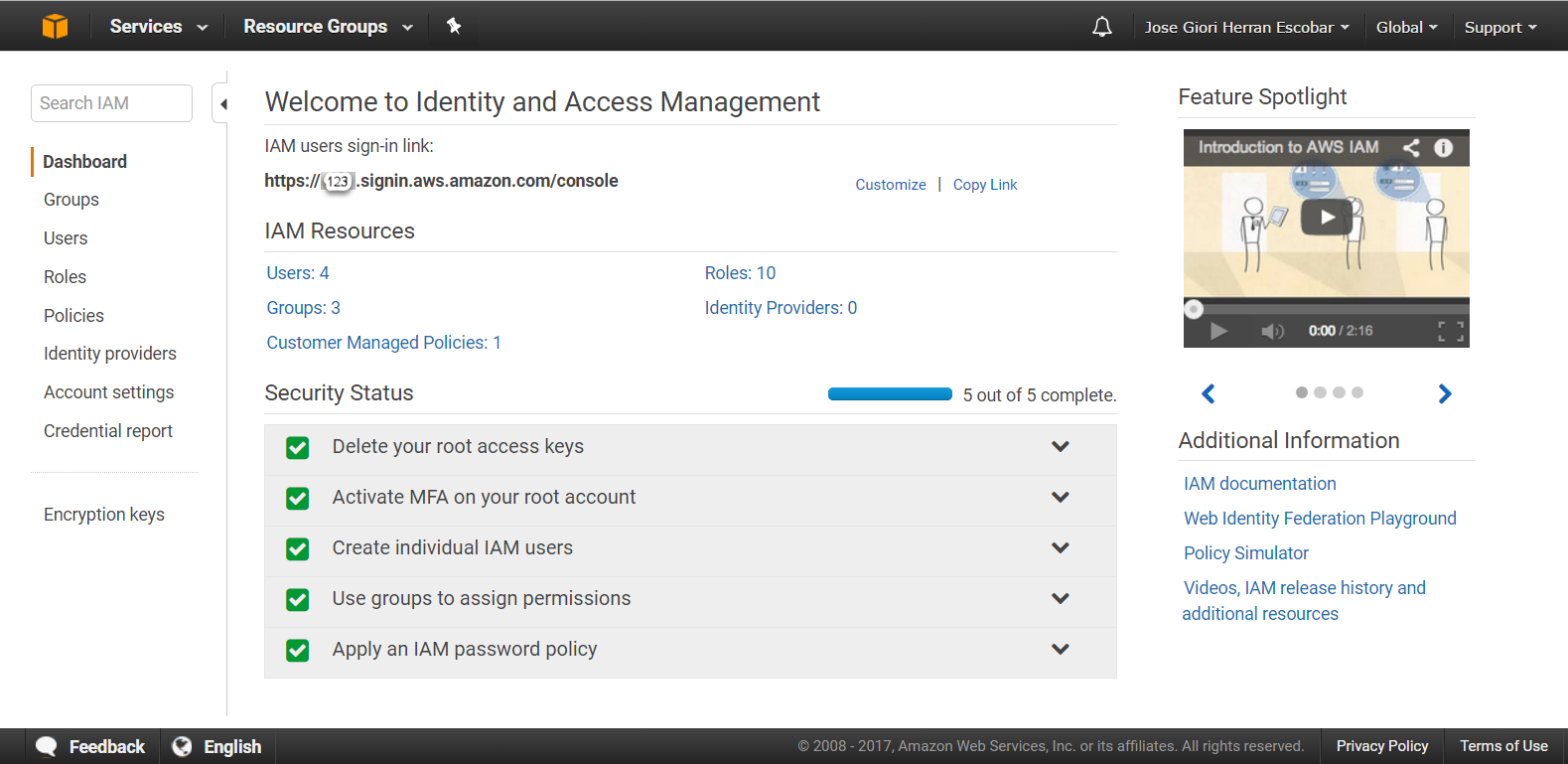
Figure #3. IAM Dashboard
Whizlabs is the pioneer institute provides various AWS Security Certification Courses for the AWS security only. Also If you are preparing for the any AWS certifications exam like; AWS Solution Architect, AWS Cloud Practitioner exam, AWS DevOps, AWS Data Science Certification, AWS Cloud Security Certification, AWS Associate Developer etc. We are also providing a complete guide to AWS Solutions Architect Associate Exam which includes number of articles over the internet regarding the AWS Architect Associate exam. And looking for any help, please send us a mail to call to our customer support team.
Important Points to Remember for the AWS Certified SysOps Administrator – Associate Certification exam
- AWS Identity and Access Management (IAM) is a web service that enables Amazon Web Services (AWS) customers to manage users and user permissions in AWS
- IAM is a feature of your AWS account offered at no additional charge
- Each IAM user has a unique identity (ID) and name
- When assign permissions, use Groups to assign permissions to multiple IAM Users and apply to those groups pre-build secure policies
- Always use AWS best security practices for authentication and authorization
Glossary
| Term | Brief description |
| Group | An IAM group is a collection of IAM users. Groups let you specify permissions for multiple users, which can make it easier to manage the permissions for those users. |
| User | An IAM user is an entity that you create in AWS to represent the person or service that uses it to interact with AWS. A user in AWS consists of a name and credentials. |
| Role | An IAM role is like a user, it is an AWS identity with permission policies that determine what the identity can and cannot do in AWS. However, instead of being uniquely associated with one person, a role is intended to be assumable by anyone who needs it. |
| Policy | A document in JSON format in which you define the permissions for a role. The document is written according to the rules of the IAM policy language.When you create a role, you create two separate policies for it: a trust policy, which specifies who can assume the role (the trusted entity, or principal; see the next term), and the permissions policy, which defines what actions and resources the principal is allowed to use. |
| Identity provider | With an identity provider (IdP), you can manage your user identities outside of AWS and give these external user identities permissions to use AWS resources in your account. You create an IAM identity provider entity to establish a trust relationship between your AWS account and the IdP. IAM supports IdPs that are compatible with OpenID Connect (OIDC) or SAML 2.0 (Security Assertion Markup Language 2.0) |
Summary
In this article, we have explained about relative concepts to the AWS Identity and Access Management (IAM) service, how to create groups, users and roles, and best practices about controlling the access to your AWS resources.
References:
[1] Amazon IAM Faqs. https://aws.amazon.com/iam/faqs
[2] Amazon IAM Documentation. https://aws.amazon.com/documentation/iam
[3] AWS Certified SysOps Administrator – Associate Certification.https://aws.amazon.com/certification/certified-sysops-admin-associate/
- Top 20 Questions To Prepare For Certified Kubernetes Administrator Exam - August 16, 2024
- 10 AWS Services to Master for the AWS Developer Associate Exam - August 14, 2024
- Exam Tips for AWS Machine Learning Specialty Certification - August 7, 2024
- Best 15+ AWS Developer Associate hands-on labs in 2024 - July 24, 2024
- Containers vs Virtual Machines: Differences You Should Know - June 24, 2024
- Databricks Launched World’s Most Capable Large Language Model (LLM) - April 26, 2024
- What are the storage options available in Microsoft Azure? - March 14, 2024
- User’s Guide to Getting Started with Google Kubernetes Engine - March 1, 2024


