In the ever-evolving landscape of technology, cybersecurity remains a crucial concern for individuals and organizations alike. With the increased reliance on technology and the rise of digitalization, it is no surprise that cybersecurity threats have become more sophisticated and widespread.
As we move towards 2024, it is important to stay up-to-date with the latest cybersecurity trends to protect against potential threats. In this blog post, we will discuss the top cybersecurity trends that are expected to dominate in 2024.
From artificial intelligence to the growing demand for ethical hacking, these trends will shape the way we approach cybersecurity and help us stay ahead of potential threats.
Let’s dive in!
Here’s the list of top cybersecurity trends that are expected to manipulate in 2024 and they are:
Cloud attacks
Nowadays, many organizations are migrating to cloud technology due to its potential benefits. Even though organizations are well-equipped with sufficient security tools and techniques to ensure data protection, threat attacks pop up due to the security immaturity of the cloud network.
Read More: How to become cybersecurity professional?
Here are some of the most common types of cloud security attacks:
- Data breaches: A data breach occurs when unauthorized individuals gain access to sensitive data stored in the cloud. This can happen due to weak passwords, insecure APIs, or other vulnerabilities in the cloud infrastructure.
- DDoS attacks: Distributed denial-of-service (DDoS) attacks can target cloud servers, overwhelming them with traffic and causing service disruptions for users.
- Malware: Malware can be introduced into cloud systems through infected files or emails. Once inside the system, malware can steal data, encrypt files for ransom, or take control of the system.
- Insider threats: Insiders with access to cloud systems may intentionally or unintentionally compromise the security of the system. This can include employees, contractors, or partners with access to the cloud infrastructure.
- Misconfiguration: Misconfigurations in cloud infrastructure can leave it vulnerable to attack. For example, if cloud storage is left open to the public, anyone can access the data stored in it.
Human error
Today, many companies know the importance of IAM and adopt cybersecurity tools to assure data protection. The DBIR report generated by Verizon says that 82% of cybersecurity breaches occur due to human factors and it becomes minor cybersecurity trends. And also lack of cybersecurity principles paved the way for most of the attacks to evolve.
The employees in an organization lie as a major cause for security breaches and their actions will be categorized as intentional and unintentional. There will be potential loss by means of this attack.
Ransomware attacks
We cannot just be careless about ransomware attacks when it is specifically targeted. Because the impact of ransomware causes huge losses to both individuals and organizations.
For instance, the occurrence of Wanna cry ransomware on NHS hospitals in Scotland has corrupted 70,000 Medical Equipment. The intention behind this attack such as to become financially benefited by just stealing the user data. Until the amount is paid to the attackers, the data will not be passed to the authorized individual.
IoT technology risks
The IoT technology interconnectivity features attain its popularity with the advent of the 5G network. Communication through multiple devices increases the vulnerability of these devices to outside influences, attacks, or undetected software defects.
Even Google’s popular browser, Chrome, has been found to have significant security issues. With 5G being a relatively new technology in the market, a thorough investigation is necessary to identify and rectify security flaws and protect the system from external attacks.
Here are some of the key security risks associated with IoT:
- Lack of standardization: There is currently no universal standard for IoT technology, which means that devices from different manufacturers may not be able to communicate with each other securely.
- Vulnerabilities in the hardware and software: IoT devices may have vulnerabilities that can be exploited by cybercriminals. These vulnerabilities may be due to errors in the design or coding of the devices, or they may be introduced through firmware updates.
- Inadequate encryption and authentication: Many IoT devices lack proper encryption and authentication protocols, making them vulnerable to attacks that can compromise sensitive data or take control of the device.
- Data privacy: IoT devices often collect and transmit sensitive data, such as personal information or location data. If this data is not properly protected, it can be intercepted by cybercriminals and used for malicious purposes.
- Distributed denial-of-service (DDoS) attacks: IoT devices can be used as part of a botnet to launch DDoS attacks on other targets. These attacks can overload servers and cause service disruptions for users.
The various levels of the 5G network may be susceptible to numerous network attacks that are currently unknown. Manufacturers must create intricate 5G hardware and software with extreme caution to prevent data breaches.
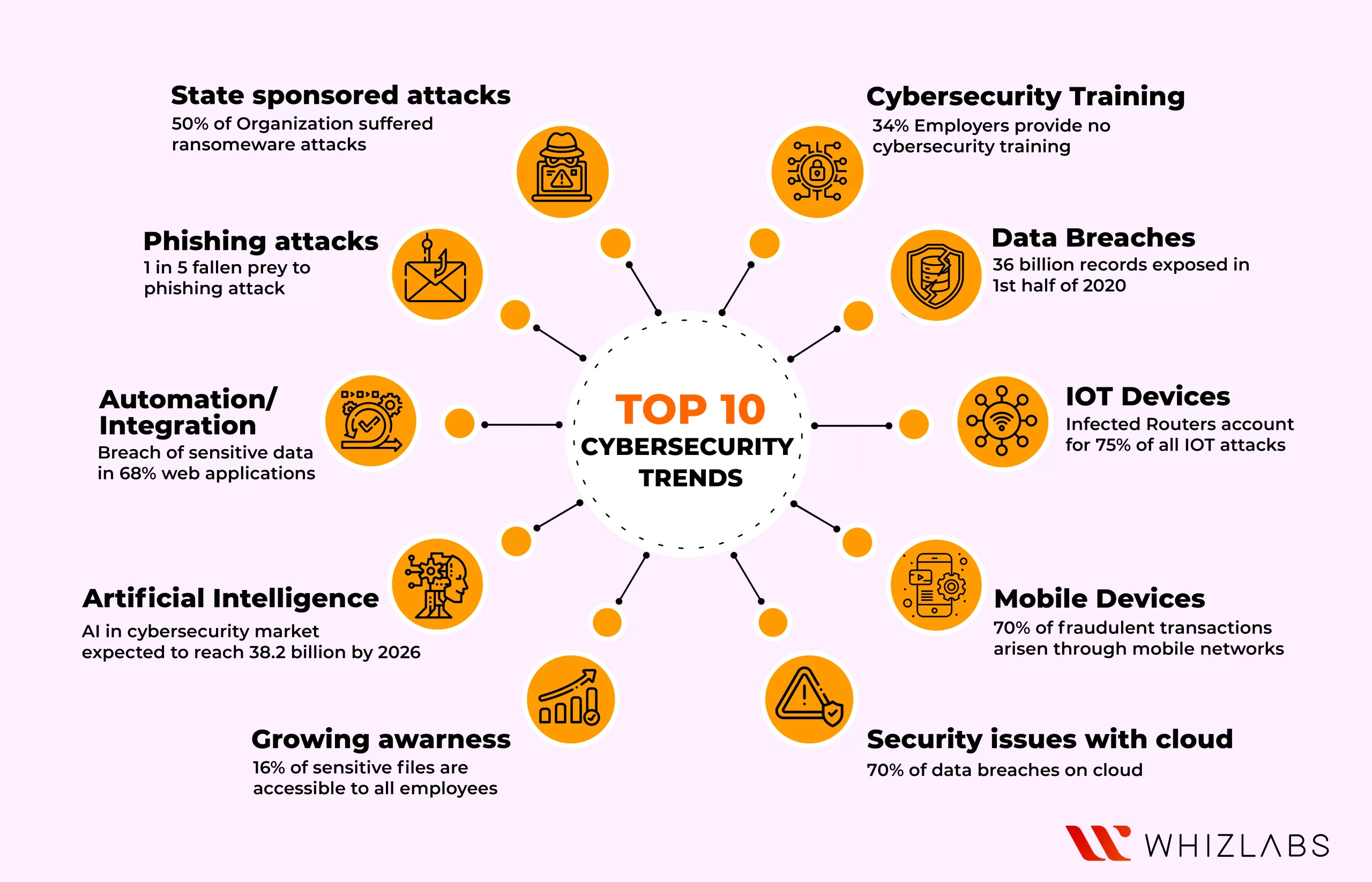
Mobile security attack
Everything is now possible with the help of mobile phones and thus hackers considered them as the primary target for successfully carrying out potential attacks and threats. Individual data such as images, emails, financial transactions, and communications get trapped by hacking mobile devices and it becomes major cybersecurity trends.
These attacks can take many different forms, including:
- Malware: Malicious software can infect a mobile device through an app, text message, or email. Once installed, malware can steal sensitive data, track the user’s location, or even take control of the device.
- Phishing: Cybercriminals can use phishing tactics to trick mobile users into sharing their login credentials or other sensitive information. This can be done through fake login screens or links to malicious websites.
- Man-in-the-middle attacks: In this type of attack, a cybercriminal intercepts the communication between a mobile device and a server. They can then eavesdrop on the conversation or even alter the data being transmitted.
- Wi-Fi attacks: Cybercriminals can set up fake Wi-Fi networks in public places, such as airports or coffee shops, and trick users into connecting to them. Once connected, the attackers can monitor the user’s online activity or steal sensitive information.
- Device theft: If a mobile device is lost or stolen, sensitive data can be compromised. This is particularly true if the device is not password-protected or if the data is not encrypted.
Cyberwarfare
Unlike traditional warfare, cyber warfare is conducted through the use of sophisticated hacking techniques, malware, and other digital tools. The goal is to cause significant damage or disruption to an enemy’s communication networks, power grids, financial systems, or other critical infrastructure.
One of the unique aspects of cyber warfare is that it can be conducted remotely, allowing attackers to launch attacks from anywhere in the world. This makes it difficult to identify the source of an attack and to respond with traditional military force. The usage of cybersecurity trends can make malware attacks to be eliminated.
Want to try some other cybersecurity certification? Try out CISSP certification
Another challenge of cyber warfare is that it can be difficult to defend against. As technology evolves and becomes more sophisticated, new vulnerabilities and attack vectors are constantly emerging. This means that defenders must remain vigilant and adaptive, continually updating their defenses to stay ahead of potential attackers.
In addition to traditional nation-state actors, cyber warfare is also being used by non-state actors such as hacktivists and criminal organizations. This raises new questions about how to respond to cyberattacks, particularly those carried out by non-state actors.
Overall, cyber warfare presents unique and complex cybersecurity trends for military and government leaders around the world. As technology continues to advance, it will be critical to develop new strategies and defenses to protect against these types of attacks.
How can organizations become ready for Future cybersecurity attacks?
According to a Global Cybersecurity Outlook 2023 made by the World Economic Forum, ‘Awareness and preparation can assist the organizations to balance technology value against the cyber risk that emerges with it.’
Here are some top solutions to defend the above-listed cybersecurity attacks and threats:
Artificial Intelligence (AI) for cybersecurity
AI is increasingly being used in cybersecurity to identify and prevent cyber threats. AI-powered systems can detect unusual behavior and patterns, allowing cybersecurity teams to quickly respond to threats. In 2024, we can expect to see more advanced AI technologies being used in cybersecurity, including machine learning, natural language processing, and predictive analytics.
Zero Trust Architecture (ZTA)
ZTA is an approach to cybersecurity that assumes all devices and users are untrusted until proven otherwise. This means that even if a device is inside the corporate network, it is not automatically trusted. Instead, ZTA uses a variety of security measures, including multi-factor authentication, encryption, and access controls, to ensure that only authorized users and devices can access sensitive data.
Cloud Security
With the increasing popularity of cloud computing, cloud security is becoming more important than ever before. In 2024, we can expect to see more organizations adopting cloud security solutions, such as cloud access security brokers (CASBs), to protect their data and applications in the cloud.
Biometric authentication
Biometric authentication, such as fingerprint or facial recognition, will become more common as a way to improve security and user experience.
Cybersecurity awareness training
Employee training will continue to be a critical component of cybersecurity, as organizations seek to educate their staff on the latest threats and best practices for protecting against them.
Internet of Things (IoT) Security
IoT devices are becoming more common, and they can be vulnerable to cyber-attacks. In 2024, we can expect to see more emphasis on IoT security, including the use of encryption, access controls, and other security measures to protect IoT devices and the data they collect.
Cybersecurity Automation
Cybersecurity automation refers to the use of automation technologies, such as artificial intelligence and machine learning, to detect and respond to cyber threats. In 2024, we can expect to see more organizations adopting cybersecurity automation to improve their threat detection and response capabilities.
Identity and Access Management (IAM)
IAM is a critical component of cybersecurity, and in 2024, we can expect to see more emphasis on IAM solutions, including multi-factor authentication and identity verification technologies, to prevent unauthorized access to sensitive data.
DevSecOps
DevSecOps is an approach to software development that integrates security into the development process. In 2024, we can expect to see more organizations adopting DevSecOps to ensure that security is built into every stage of the software development lifecycle.
In addition to these techniques, there are several technologies that can be used to defend against cyber attacks. These include firewalls, intrusion detection and prevention systems, anti-malware software, and security information and event management (SIEM) systems. These technologies work together to identify and respond to cyber threats in real-time, helping to minimize the impact of an attack.
Overall, effective cybersecurity requires a multi-layered approach that combines a range of techniques and technologies to protect against cyber threats. By implementing robust security measures and staying up-to-date with emerging threats, organizations can ensure that they are well-prepared to defend against cyber attacks and protect their systems and data.
Machine learning is a technology that holds a lot of promise for the future of cybersecurity. It has the potential to not only detect threats but also proactively address them before they can cause harm. As a result, many experts believe that artificial intelligence and machine learning will play an increasingly important role in the field of cybersecurity in the years to come.
FAQs
Which technology has a better scope in cyber security?
Machine learning is a technology that holds a lot of promise for the future of cybersecurity. It has the potential to not only detect threats but also proactively address them before they can cause harm. As a result, many experts believe that artificial intelligence and machine learning will play an increasingly important role in the field of cybersecurity in the years to come.
Is cybersecurity a good field for the future?
Cybersecurity is an ever-growing industry. It is estimated to proliferate by 11% in 2024 and by 20% in 2025 median salary of $81,000.
What are the top cyber threats in the year 2024?
There are several emerging cyber threats that could pose a risk in the near future. And thus usage of cybersecurity trends can defend these threats. And thus threats that are faced may include:
- Increased cloud attacks
- Mobile security vulnerabilities
- IoT targeted attacks
- Vulnerabilities in the healthcare sector
- Use of AI in cybersecurity
- Users as a potential attack surface
- Diversified cyber risk
Summary
Hope this blog helps in understanding the cybersecurity trends that may evolve in 2024 and how they impact organizations and individuals. Organizations need to stay ahead of the curve by adopting the latest cybersecurity trends to protect their assets and data from potential attacks.
By implementing AI and ML, cloud security, post-quantum cryptography, IoT security, and blockchain technology, organizations can stay ahead of the curve and ensure their data and assets are secure.
If you have any queries on this blog post, please feel free to ping us!
- 7 Pro Tips for Managing and Reducing Datadog Costs - June 24, 2024
- Become an NVIDIA Certified Associate in Generative AI and LLMs - June 12, 2024
- What is Azure Data Factory? - June 5, 2024
- An Introduction to Databricks Apache Spark - May 24, 2024
- What is Microsoft Fabric? - May 16, 2024
- Which Kubernetes Certification is Right for You? - April 10, 2024
- Top 5 Topics to Prepare for the CKA Certification Exam - April 8, 2024
- 7 Databricks Certifications: Which One Should I Choose? - April 8, 2024



