In this blog, we will explore a Google Cloud Certified Associate Cloud Engineer, you are responsible for not only deploying and maintaining cloud applications and solutions but also configuring security access. This blog discusses the Google cloud security best practices based on the Google Certified Associate Cloud Engineer Certification exam. Let’s get started to understand how GCP cloud engineers handle security and IAM.
Google Cloud Platform Security
At the heart of Google Cloud Security is the shared fate model, which emphasizes close collaboration and partnership between Google and its customers for maintaining cloud security. In this approach, besides ensuring infrastructure security, Google provides customers with best practices, security configurations, compliance recommendations, and tools and services to securely deploy and manage cloud workloads.
While security teams play an important role in designing and maintaining cloud security, everyone working on the cloud is responsible for maintaining security. The misconfigurations or weak access controls can expose cloud infrastructure to vulnerabilities. As a result, organisations need to manage resources to prevent unwanted access, align with least privilege security principles and more.
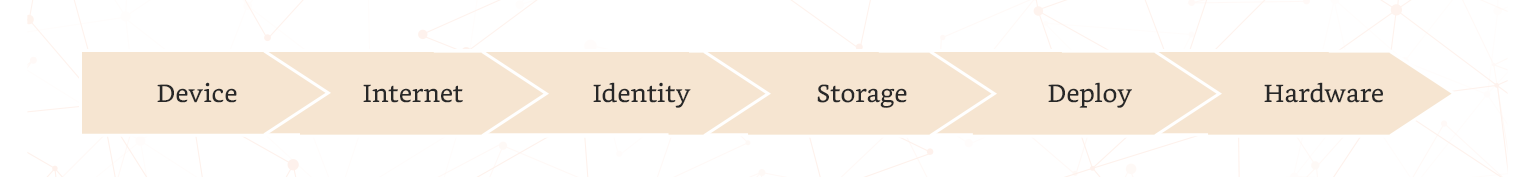
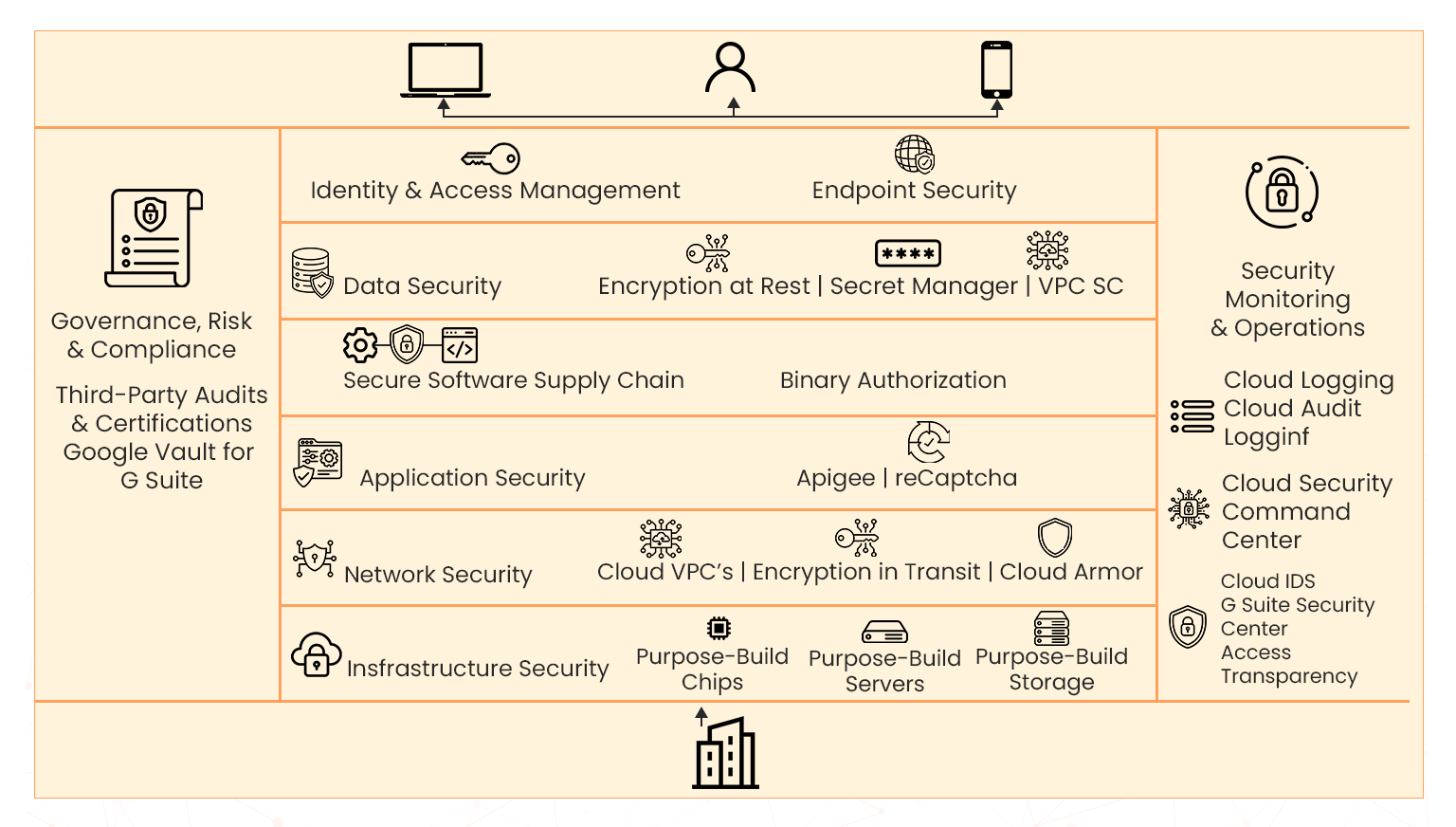
Google provides infrastructure security through six progressive layers, maintaining a defence of depth.
Figure. Six Security Layers of Google Cloud
The focus of this blog is identity security, which is authenticating all users’ identities and services. The Google Certified Associate Cloud Engineer course covers this topic in the Configuring Access and Security section. The two common approaches to secure identity are:
- Multi-factor authentication (MFA)
- Identity and access management (IAM)
Multi-Factor Authentication (MFA) in GCP
MFA is a verification process which asks users to present two or more factors to authenticate their identity and get access. The Multifactor Authentication (MFA) in GCP gets users “something you know (password) with “something you have (phone/security key)” to harden accounts. This makes multi-factor authentication (MFA) the best for an IAM practice. Starting in November 2024, MFA is now mandatory for Google Cloud in a phased manner. It provides an extra layer of security, which helps prevent unauthorized access to Google Cloud resources. With MFA enabled, along with your password, you must enter a second form of verification, such as:
- Prompts
- A security key
- An authenticator app
- Backup codes
Identity and Access Management (IAM)
In general, Google Cloud IAM is a model for verifying and authenticating user and account identities and regulating access to those identities. It is one of the core areas in the Google Cloud Well-Architected Framework: Security, privacy, and compliance. GCP IAM controls access to GCP resources. It enables you to:
- Allow and revoke access
- Enforce granularity on who and what they can access
- Manage roles and permissions
- Audit
Acting as the front gate for all types of security, IAM sets policies to control who can access what across data, network, applications, and infrastructure in a hierarchical format.
The following table shows the breakup of IAM functions:
| Who | members | Example: Users, groups, organizations, service accounts |
| What access | Roles | Example: Basic (broad) and predefined (granular) |
| Resources | GCP resources | Example: Instances, projects, cloud storage buckets, etc. |
Figure. IAM acts as the front gate for all types of GCP security
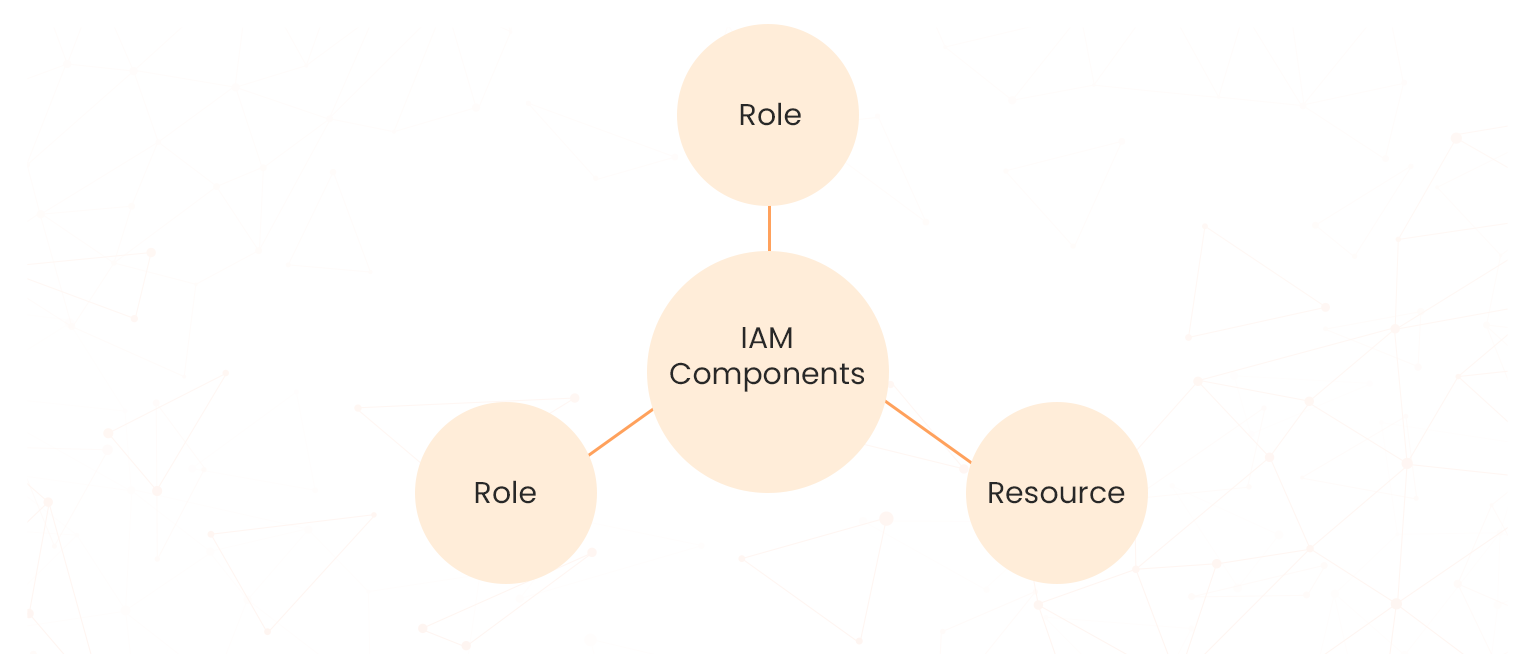
IAM core components
IAM defines who can do what on which GCP resources, using three components.
- Principal: also known as member, a principal represents authenticated identities of an end user or an application. IAM supports different types of principals, and they can be divided into two broad categories:
* Human users: represent human users; for example, Google Accounts, Google groups, and federated identities in workforce identity pools.
* Workloads: represent workloads; for example, service accounts and federated identities in a workload identity pool.
- Role: It is the collection of permissions assigned to a principal that determines what the principal can do and with what resources. A permission is a specific operation allowed on a resource.
- Resource: Everything in Google Cloud is a resource. Google Cloud resource that you want to let the principal access
IAM important features
Deploying and managing applications and services in GCP requires a clear understanding of IAM features and the way Google structures projects and manages identities and access control. The following are some of the core IAM features:
- Role-Based Access Control (RBAC )
- Resource hierarchy and policy inheritance
- Service accounts
Your knowledge of these features will help you perform tasks such as managing identity and access management (IAM) assignments, creating customer roles, managing service accounts, and viewing audit logs. In addition, you will be able to relate how these features help meet Google security best practices, such as:
- Least privilege: Grant minimal permissions to predefined roles.
- Separation of duties: allow some users to have the ability to change codes and others to deploy codes
- Defense of depth: apply multiple overlapping security controls
IAM Role
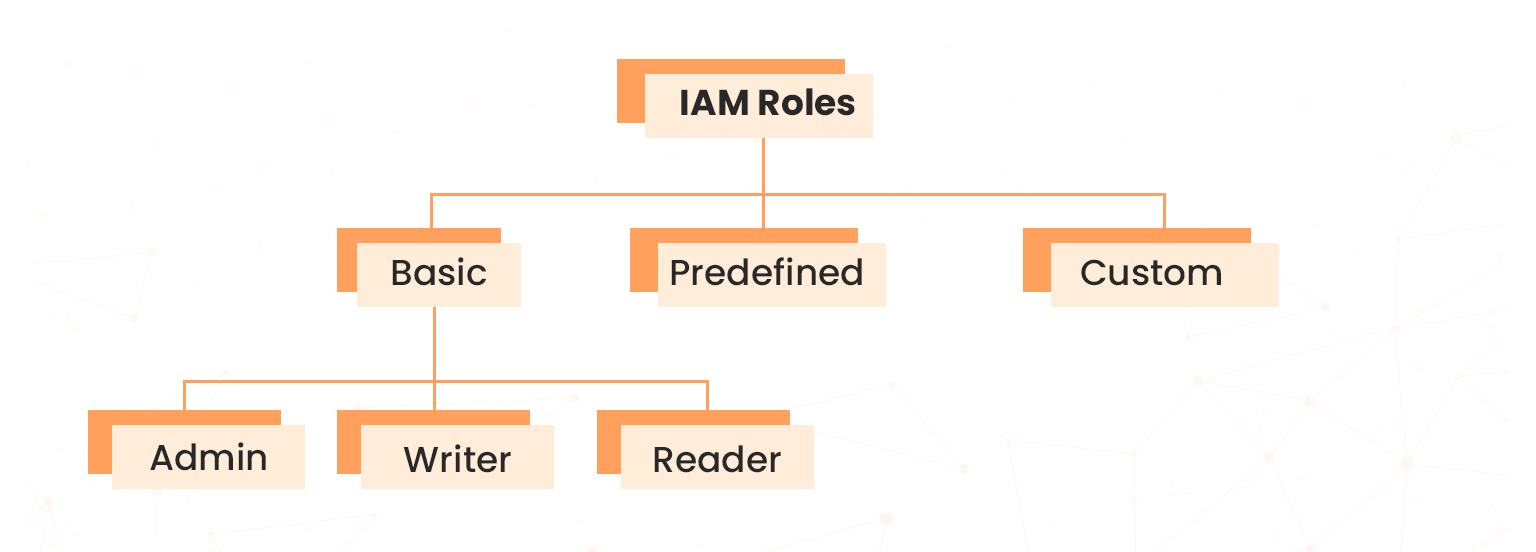
Cloud engineers can enforce granularity on who and what they can access through roles. IAM supports three types of roles.
- Basic roles: These are broad roles that are applied at the project level of the resource hierarchy. They are of three types: reader, writer, and admin.
- Predefined roles: also known as curated roles, these roles provide granular access for a specific service and are created and managed by Google Cloud. They are designed to map to job functions, for example, Compute Network Admin, Security Reviewer, Storage Admin, and much more.
- Custom roles: These are created and managed by users to provide granular access according to a user-specified list of permissions.
Example: a group of users is granted the instance admin role on project a.
Resource hierarchy and policy inheritance
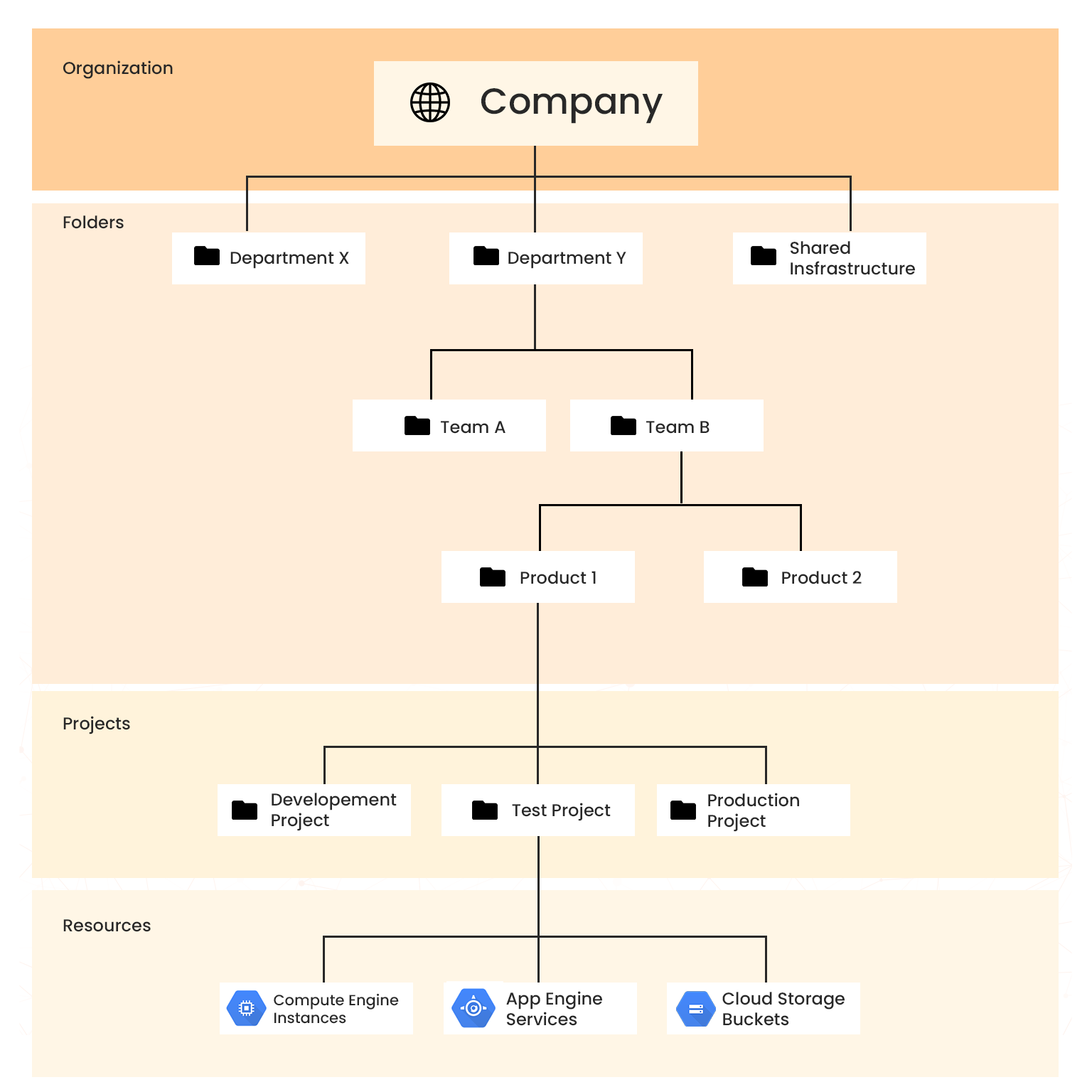
Google follows a fixed hierarchy consisting of Organizations, Folders, and Projects to distribute and manage GCP resources. IAM works in tandem with this resource organization to define who can access what at different levels.
- Organization: it is the super node of the hierarchy that represents an organization such as a company.
- Folders: they are optional and provide sub-organizations for additional grouping to represent department, team, application or environment.
- Projects: They are mandatory and act as the primary container for managing Google resources.
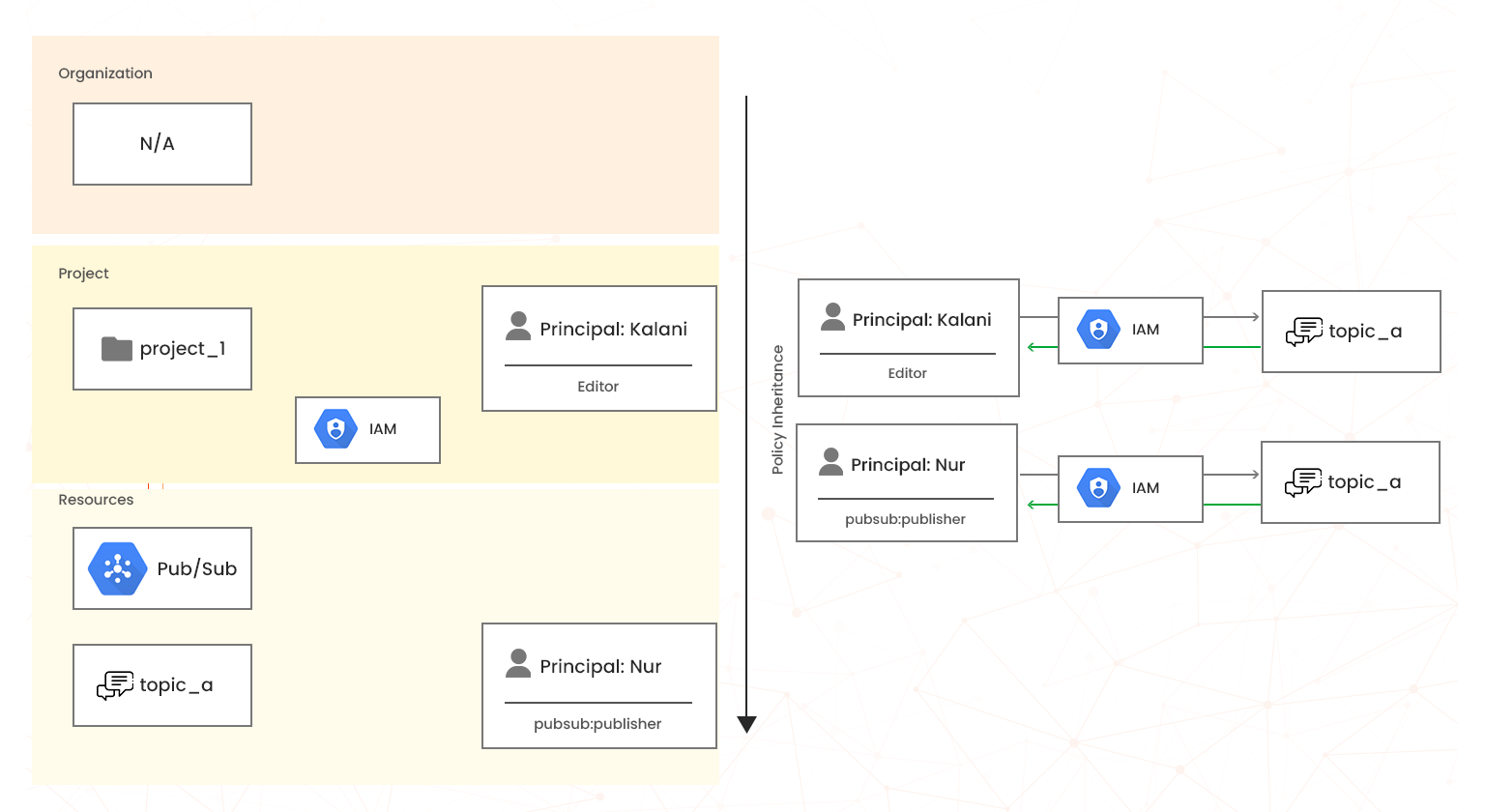
As a cloud engineer, you must understand the resource hierarchy and the inheritance properties that propagate down because it directly relate to how policies are managed and applied when you use Google Cloud. Policies and permissions work together to control access because permissions are assigned to roles and not to members. A policy binds members with roles.
Example. Google resource hierarchy
Figure. Resource hierarchy and IAM policy inheritance
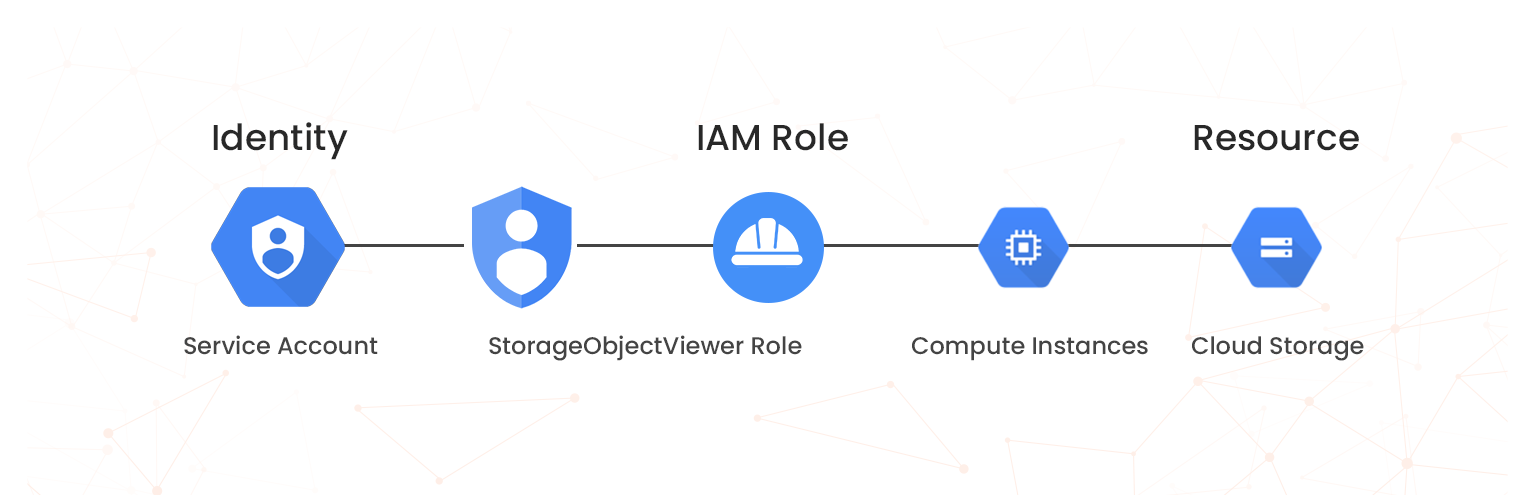
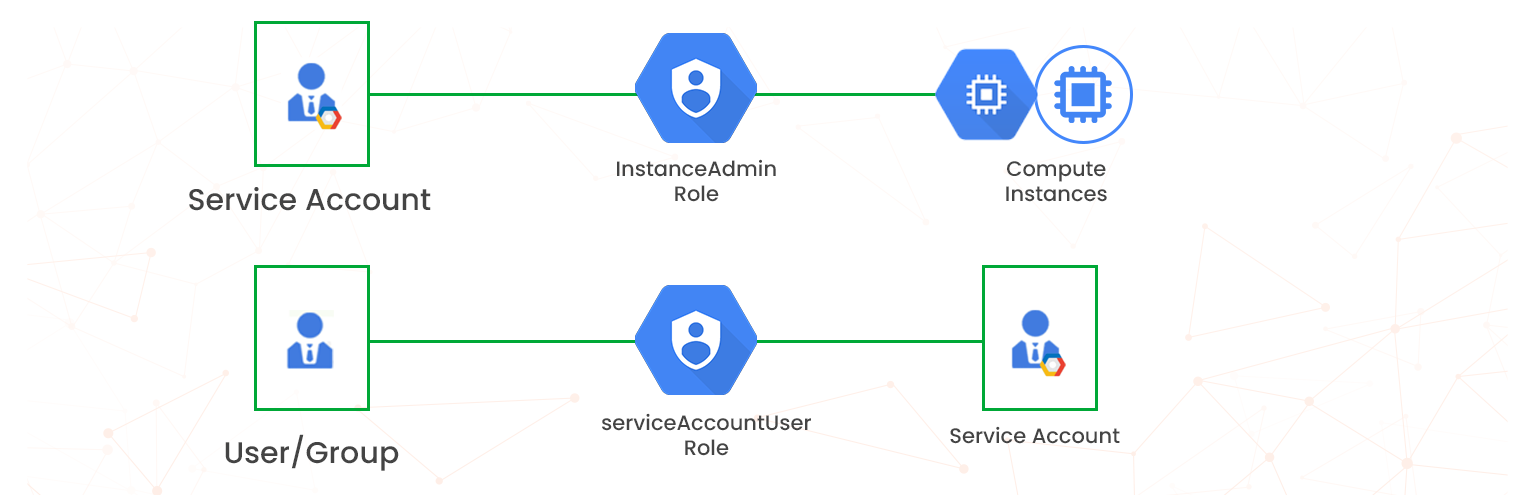
Service Accounts
Service accounts are special accounts for non-human users such as applications, services, and VM instances. Service accounts control server-to-server interactions:
- Authentication from one service to another
- Control privileges used by resources
They are of two types:
- User-managed service accounts: users create and manage them
- Service agents: Google Cloud creates and manages
Service accounts can act as both principals and resources. You can grant service accounts access to Google Cloud resources and permit other principals to access the service account.
IAM Security Best Practices
Google IAM is a powerful tool, yet it can become complex due to its fine-grained access control, hierarchical policy inheritance, and multiple identity types. The following best practices will help you simplify it:
- Use projects to isolate resources and understand policy inheritance thoroughly
- Use groups when configuring Google Cloud access and assign roles to the group for the ease of managing permissions.
- Basic roles can be overly permissive. Instead, use the most limited predefined roles or custom roles that meet your needs.
- Grant role by smallest scope, for example Compute Admin role vs. Compute Instance Admin.
- If a role is needed across multiple projects, grant at organization or folder level.
- Implement processes to manager service account keys
Final thoughts
The Google Associate Cloud Engineer certification is an entry-level certification for IT professionals who are new to GCP. For a Cloud Engineer it is tasked with designing, implementing and maintaining secure cloud infrastructure. Becoming proficient in the Cloud security model and IAM best practices is important for passing the exam and applying these principles in real-life scenarios. You can pick the best resources from us, we have dedicated course specific practice tests, video courses, Sandboxes and Hands-on Labs to help you gather all required knowledge. What now? check out our content. And achieving this certification, you can perform a bit of everything, and from here, you can further your cloud career by specialising in an advanced role such as Cloud Security Engineer, Solutions Architect, DevOps Engineer and many more.
- How GCP Cloud Engineers Handle Security & IAM - May 15, 2025
- What Is Amazon Redshift and How Does It Work? - April 28, 2025
- What Is the Role of AWS Lambda in AI Model Deployment? - April 2, 2025
- What Are ETL Best Practices for AWS Data Engineers - March 17, 2025
- How to Create Secure User Authentication with AWS Cognito for Cloud Applications - September 30, 2024
- 2024 Roadmap to AWS Security Specialty Certification Success - August 16, 2024
- Top 25 AWS Full Stack Developer Interview Questions & Answers - August 14, 2024
- AWS Machine Learning Specialty vs Google ML Engineer – Difference - August 9, 2024