When it comes to securing the organization’s data, there are various terms come into play. Among that, Privileged access management (PAM) attains its unique place.
Privileged accounts grant certain users special privileges to execute critical business functions, like accessing sensitive company information, managing user passwords, and making changes to IT infrastructure. However, if these accounts are compromised, the company faces major risks.
A robust PAM solution enables organizations to grant privileged access to authorized users while securing vital business systems against harmful cyberattacks.
What is Privileged Access Management (PAM)?
It is an identity security solution that helps in protecting the organization’s assets against the threat made by attackers by simply monitoring, detecting, and defending the privileged access given to the critical resources.
It primarily focuses on three key aspects such as people, process, and technology, and offers privileged account visibility into who is using the privileged accounts and what they are doing with them.
The main intention of the PAM such that limit the users to accessing the administrative function and it can certainly level up the system security by adding additional security layers just to mitigate the threat actors.
How Privileged Access Management (PAM) works?
As a first step, organizations need to identify which accounts have privileged access and subsequently determine the policies to be applied to these accounts.
For example, the organization may require service accounts to renew their passwords each time credentials are accessed or mandate Multifactor Authentication (MFA) for system administrators.
Additionally, maintaining a comprehensive log of all privileged sessions could be another crucial policy. Each process should align with specific risk considerations – like changing service account passwords to mitigate insider threats and enforcing MFA to counter password-related attacks.
Once the discovery phase is complete and privileged access management (PAM) policies are finalized, the organization can proceed to implement a technology platform dedicated to monitoring and enforcing Privileged Access Management.
This PAM solution automates policies and empowers security administrators with the tools to effectively manage and monitor privileged accounts. By integrating this solution, organizations can proactively fortify their security posture and safeguard against potential breaches or cyber threats.
Also Read : A Quick Introduction to Cybersecurity
Privileged Access Management (PAM) Features
PAM solution offers robust features to help you stay ahead of the following security risks:
- Offers just-in-time access to important assets
- Secured remote access with the usage of encrypted gateways instead of passwords
- Monitor privileged sessions to carry out investigative audits
- Analyze unusual activity which will be harmful to the organization
- Capture privileged account-related events to perform the compliance audits
- It also supports Security information and event management (SIEM) integration
- Reports generation done on privileged user access and activity
- Security to the DevOps with the usage of integrated password security
Types of Privileged Accounts
In Privileged Access Management (PAM), following certain best practices is crucial to level up security, especially in handling administrative accounts.
While non-IT users are assigned standard user accounts for routine tasks, IT employees may possess both standard user and superuser accounts.
The key PAM practice here is limiting the use of administrative accounts to essential tasks and for the shortest possible duration due to their elevated privileges and associated risks.
Various privileged accounts have been listed below:
- Local administrative accounts: Non-personal accounts granting administrative access to the local host or instance only.
- Domain administrative accounts: Relying on privileged administrative access across all workstations and servers within the domain.
- Break glass (emergency/firecall) accounts: Reserved for unprivileged users to obtain administrative access during emergencies.
- Service accounts: Privileged local or domain accounts used by applications or services to interact with the operating system.
- Active Directory/domain service accounts: Facilitating password changes for accounts, among other functions.
- Application accounts: Utilized by applications to access databases, run batch jobs or scripts or enable access to other applications.
In IT environments, privileged accounts increasingly belong to machine identities rather than human ones. The growth of machine accounts, as seen in RPA and automated workflows, introduces complex security challenges and further increases the significance of PAM systems.
By adhering to these PAM best practices, organizations can significantly enhance their security posture, mitigating potential risks associated with privileged access and safeguarding critical systems and data.
PAM vs. PIM
Privilege Access Management (PAM) plays a critical role in organizations by effectively managing identities and fortifying their cybersecurity defenses. By implementing PAM, organizations create barriers that defend threat actors from infiltrating the networks and gaining unauthorized privileged access to critical accounts.
It provides essential protection to privileged groups controlling access to domain-joined computers and associated applications.
One of the core strengths of PAM lies in its monitoring, visibility, and precise controls. This empowers organizations to closely track privileged administrators, ensuring their activities are transparent, and their accounts are not misused or compromised.
On the other hand, Privileged Identity Management (PIM) serves as an additional layer of security by offering time-based and approval-based role activation.
This strategy mitigates the risks of granting excessive, unnecessary, or misused access to sensitive resources within the organization. PIM focuses on enforcing just-in-time access and just-enough access for privileged accounts, minimizing potential vulnerabilities.
| PIM | PAM |
| Focus on resource management | Focuses on securing resources |
| Determines the parameters of access | Focuses on monitoring unauthorized access |
| Based on roles or attributes | Validates user identities |
| Distributes access to prevent | Providing secure access to authorized resources |
| Excessive privileges | Provide just-in-time access for users who require temporary privileged access |
Privileged Access Management (PAM) and PIM are similar in some aspects but differ in their approaches to improvise security. PAM utilizes advanced tools and technology to control and monitor access, ensuring the “least privilege” for employees.
On the other hand, PIM focuses on time-bound access for privileged accounts like admins and super users, adding an extra layer of security. Together, they form a powerful security framework to protect organizations against potential threats.
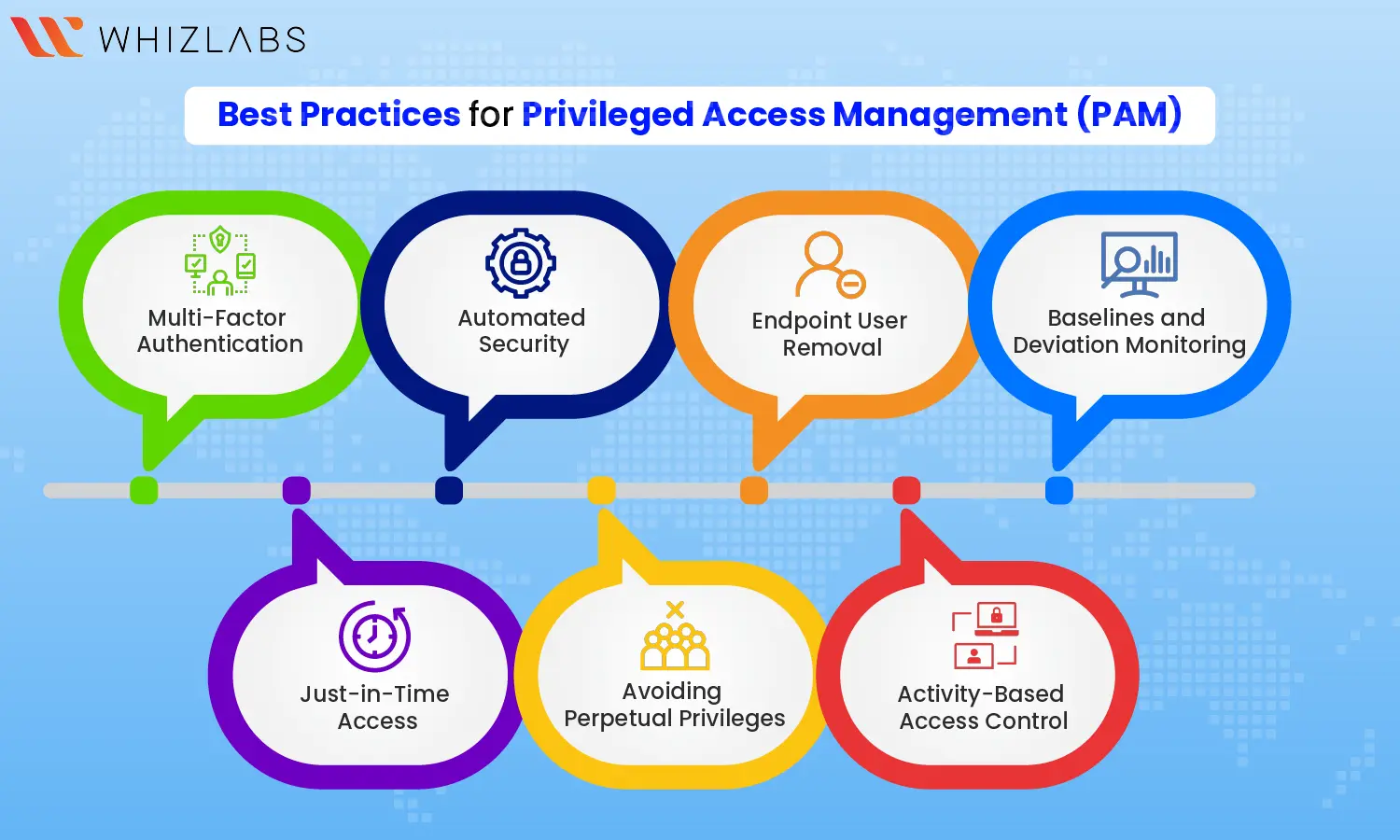
Privileged Access Management (PAM) Best Practices
Implementing the Privileged Access Management (PAM) strategy requires unique best practices:
- Multi-Factor Authentication (MFA): Strengthen your sign-in process by mandating MFA, ensuring users verify their identity through a second verified device or by the usage of Microsoft Security identity and access solutions. This adds an extra layer of protection against unauthorized access.
- Automated Security: Bolster your defenses and boost efficiency by automating security protocols. Automatically restrict privileges and prevent unsafe actions when potential threats are detected, reducing human error risks.
- Endpoint User Removal: Identify and eliminate unnecessary end-point users from local admin groups on Windows workstations. This helps to defend the threat actors’ ability to exploit admin accounts and traverse the network.
- Baselines and Deviation Monitoring: Maintain a vigilant eye on privileged access activity, observing who accesses the system and how privileged passwords are utilized. Setting baseline metrics aids in promptly spotting anomalous behavior.
- Just-in-Time Access: Follow the “least privilege” principle by granting minimal access initially and elevating privileges when necessary. This tailored approach based on trust levels, needs, and privileges boosts overall system segmentation.
- Avoiding Perpetual Privileges: Use temporary just-in-time access or just-enough access, rather than providing perpetual privileges. This ensures users possess valid reasons for access, reducing exposure to potential security risks.
- Activity-Based Access Control: structuring the access by evaluating past activity and usage, aligning privileges with actual resource utilization. By closing the gap between granted and utilized privileges, security gets enhanced.
Know More : Top 50 Cybersecurity Interview Questions And Answers for Freshers
Importance of privileged access management
Here are the benefits of Privileged Access Management such as:
Restricted access: We all know that we humans pave the way for security threats. Secondly, privileged accounts were found to be a major risk to the organization. To put an end to this, PAM train the security team on how to identify the risk that may arise due to privilege abuse and take a remedy to reduce those risks.
Meanwhile, PAM ensures that the teams only have restricted access to critical data while doing their jobs.
Higher privileges: In the digital world, privileges play a major role. In general, computing devices made interaction to complete certain tasks. Nowadays, organizations highly rely on the cloud, DevOps, IoT, and so on. The advent of those technologies surged the importance of privileged access. In return, the attack surface also proliferates.
This kind of non-human entity becomes outnumbered, which makes it harder to manage and monitor manually. Commercial-off-the-shelf (COTS) apps need access to the various network parts to get exploited by an attacker.
After the consideration of the above concern, many organization strongly believes that applying stronger privileged access management can help in detection of the anomalous activities in the on-premises, cloud, and in hybrid environments.
Security to endpoints and workstations: Cyber attackers have a keen interest in targeting endpoints and workstations within enterprises. The endpoints include laptops, smartphones, tablets, desktops, servers, and more, which typically hold inherent privileges.
While built-in administrator accounts empower IT teams to address local issues and they additionally introduce significant risks. Malicious actors can exploit admin accounts, moving undetected from one workstation to another, accessing the additional credentials, and elevating privileges to navigate through the network to achieve their malicious goals.
To proactively address these threats, a comprehensive Privileged Access Management (PAM) program must prioritize the removal of local administrative rights on workstations. This strategic step significantly reduces the overall risk posture of the organization.
Higher compliance: Beyond mitigating security risks, Privileged Access Management (PAM) plays a critical role in achieving compliance objectives. While monitoring and detecting suspicious events are vital, the focus should center on managing, monitoring, and safeguarding privileged access—the most vulnerable aspect.
Implementing PAM within a robust security and risk management strategy empowers organizations to record and log all activities related to critical IT infrastructure and sensitive data. This streamlined approach simplifies audit and compliance requirements by enhancing the organization’s overall security resilience.
Conclusion
Incorporating privileged access management (PAM) into a company’s identity governance strategy is paramount. A robust PAM solution ensures that privileged access is granted only to those who truly require it, safeguarding the organization against harmful attacks that may affect its integrity.
This integration streamlines the process for requesting, provisioning, and attesting to both privileged and limited user access can save time, and simplify the protection of all user identities.
If you have any questions about this Privileged Access Management (PAM) blog post, feel free to comment to us!
Maintain a vigilant eye on privileged access activity, observing who accesses the system and how privileged passwords are utilized. Setting baseline metrics aids in promptly spotting anomalous behavior.
- Top 20 Questions To Prepare For Certified Kubernetes Administrator Exam - August 16, 2024
- 10 AWS Services to Master for the AWS Developer Associate Exam - August 14, 2024
- Exam Tips for AWS Machine Learning Specialty Certification - August 7, 2024
- Best 15+ AWS Developer Associate hands-on labs in 2024 - July 24, 2024
- Containers vs Virtual Machines: Differences You Should Know - June 24, 2024
- Databricks Launched World’s Most Capable Large Language Model (LLM) - April 26, 2024
- What are the storage options available in Microsoft Azure? - March 14, 2024
- User’s Guide to Getting Started with Google Kubernetes Engine - March 1, 2024